What are the threats to your NGO? How to use threat intelligence for your risk assessment
Harnessing the power of threat intelligence in your NGO’s security risk management process.
As a sector that operates in some of the most unstable and insecure areas of the world, NGOs and other companies in the humanitarian aid and development sector have a particularly keen need for comprehensive security and risk management planning.
Duty of care is incredibly important for any organisation, especially those sending staff into difficult operating environments. This makes compiling an effective, well-informed risk assessment paramount for NGOs.
This is only possible when it is based on accurate, actionable intelligence.
The first, most important step of any new programme or deployment is to understand the context, risks, and threats to the organisation that exist in your area of operation.
If you don’t have a clear understanding of the particular threats you may be exposed to then it is impossible to effectively plan and implement your safety and security risk management strategies.
This article will highlight how to use threat intelligence to fully understand the threats you might face in your operating environment, and why you should be using threat intelligence data as part of your risk assessment and mitigation processes.
Where is your NGO's area of operation?
Drilling down into the region, country, and specific area of operation is an important early stage of carrying out a security and risk assessment for any potential new project or deployment. Where will your team be operating? Will they be based in a static location, have multiple operating sites, or travel from one area to another? Will there be a headquarters in a specific town or city? What sort of infrastructure exists in these locations, and how accessible are they?
Often, areas of need cross regional and national borders, too, making it necessary to understand the context in more than one country, as well as any nuances that are unique to the local area specifically.
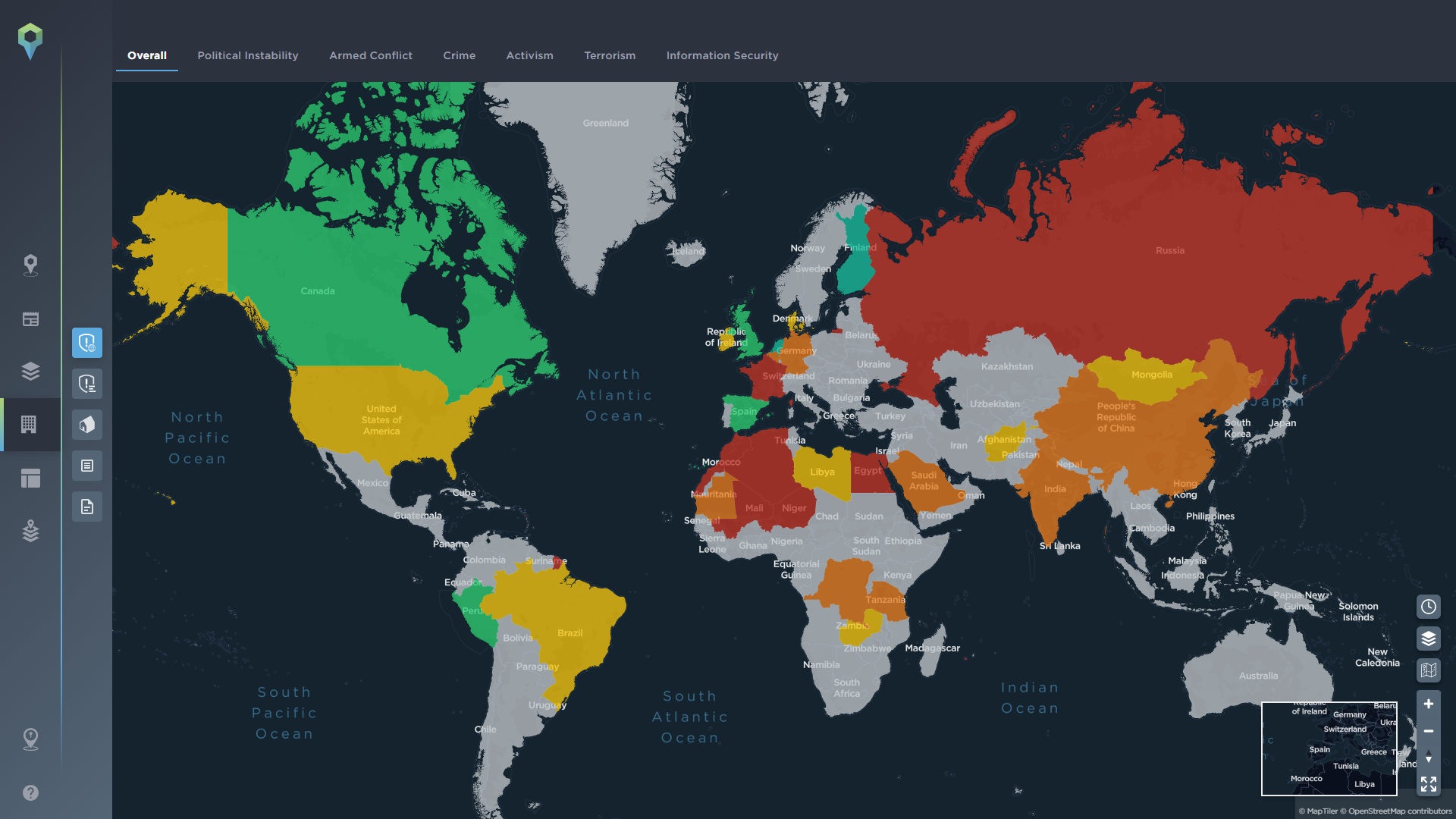
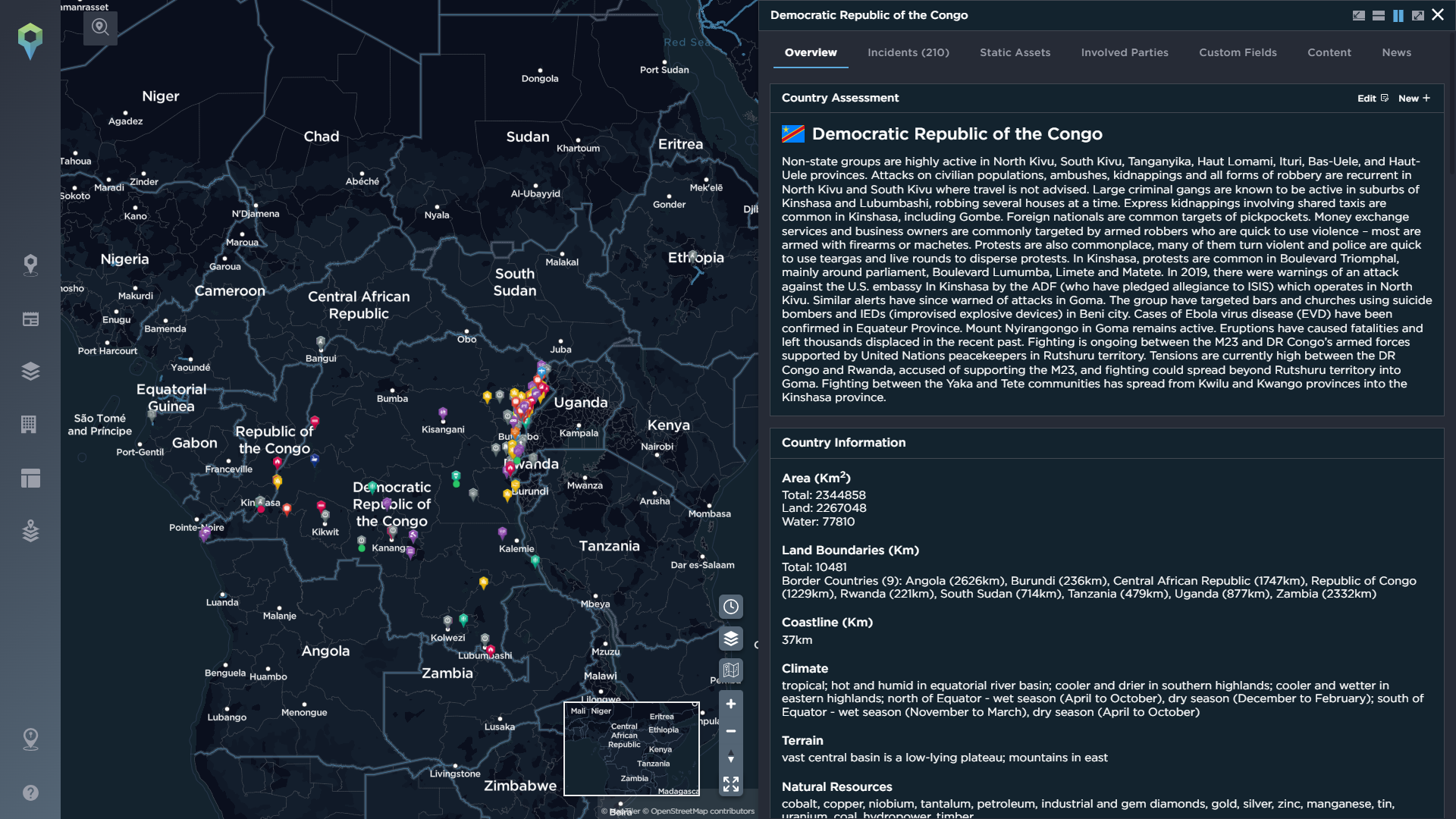
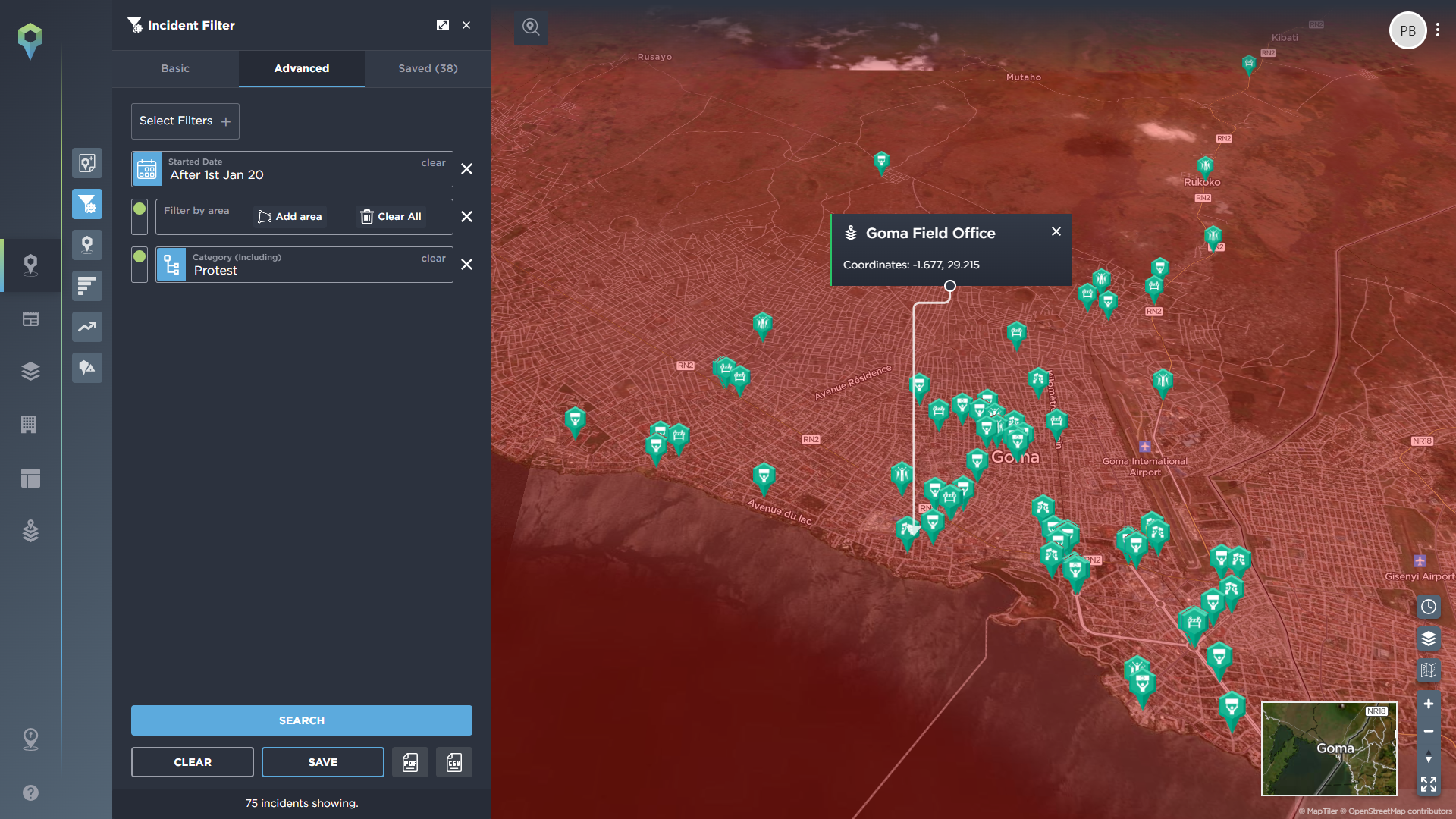
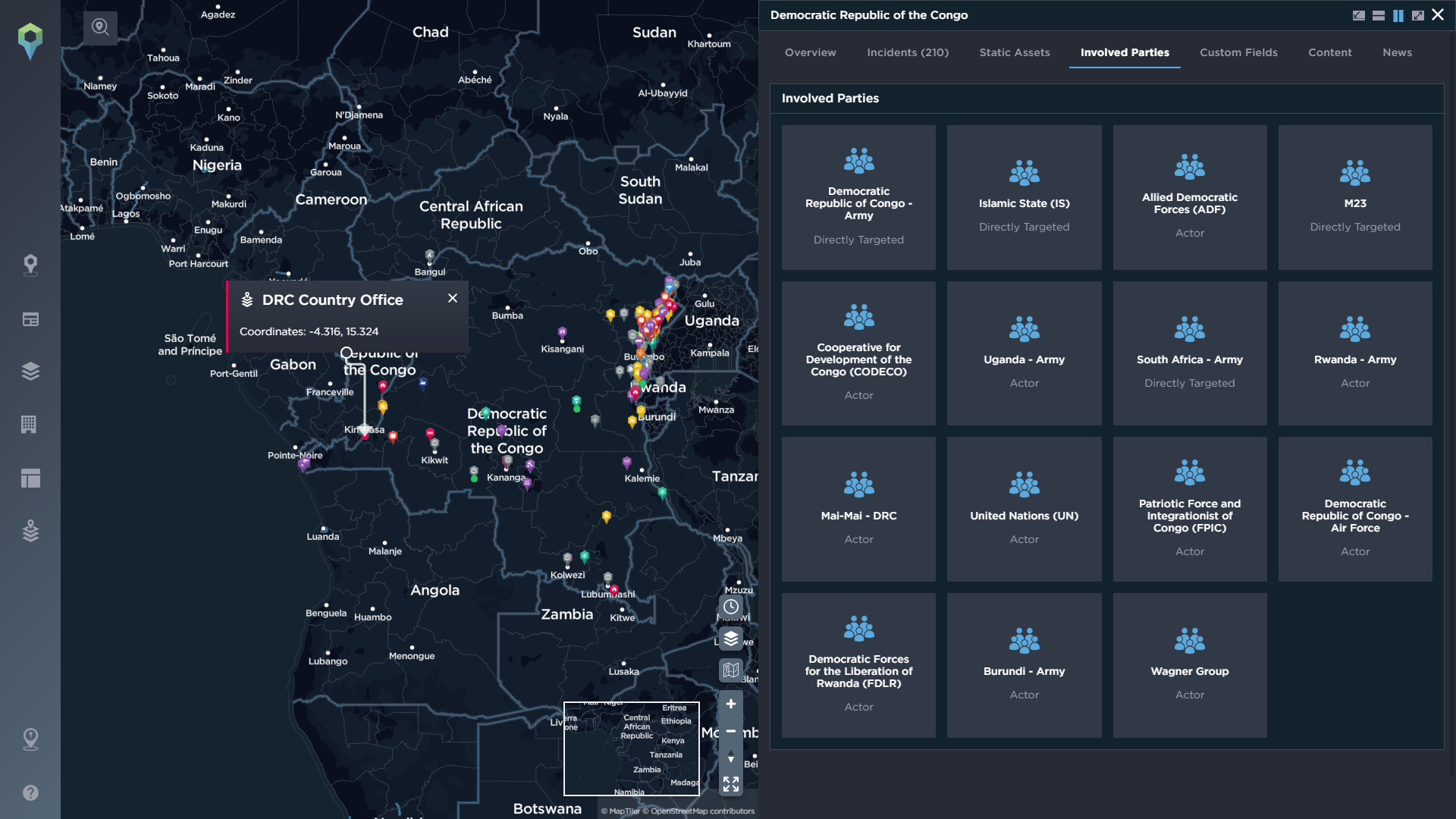
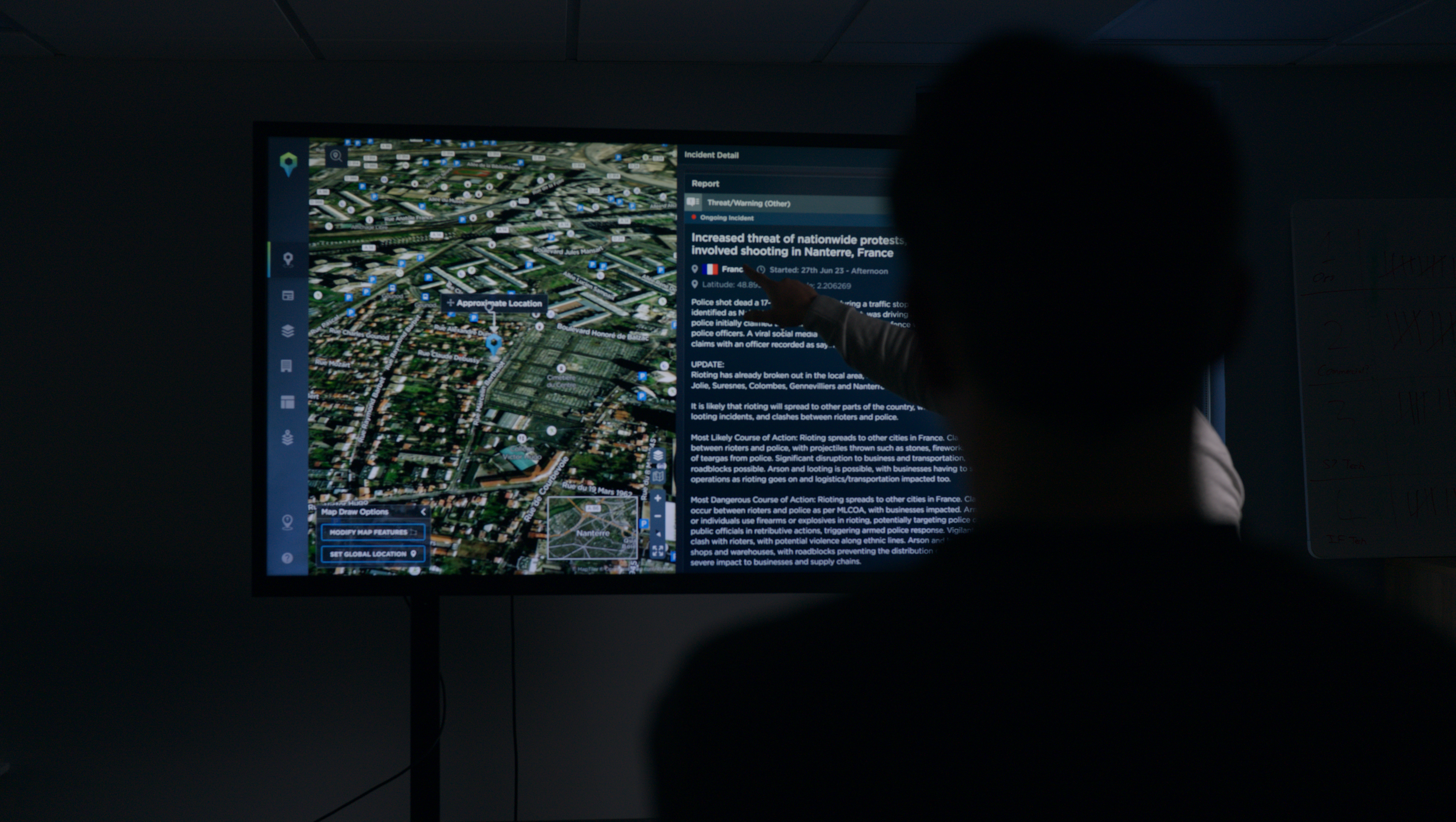
To conduct an effective threat assessment for the area you are operating in, it pays to have as much of an understanding of the locality as possible, with intelligence data playing a key role. A quick way to begin understanding the situation in a country is through the use of our optional country profiles feature, which lets you understand at a glance exactly what to expect when you begin to operate there, from a summary of the key threats, to demographic information, the actors to be aware of, and the latest incidents mapped on the platform.
At a global organisational level, we also have the additional available feature of a customisable risk map that you can update according to your own in-house risk assessment. This means when you are required to respond quickly to an emerging situation in a new country, you can see at a glance the level of risk associated with that country according to your organisation’s experts.
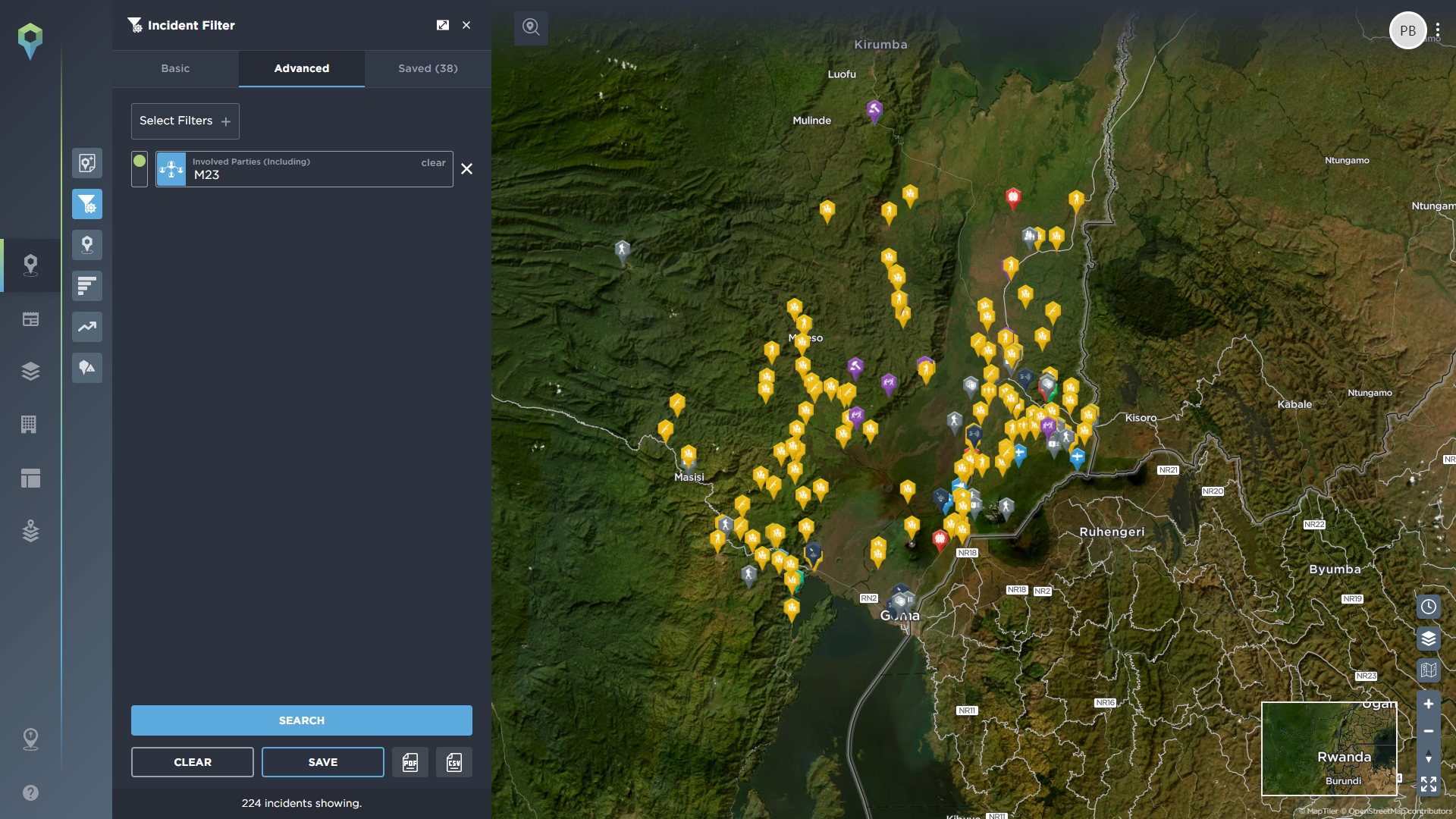
You can then begin to filter for more in-depth information via our advanced filtering tools.
With Intelligence Fusion, you can filter through our threat intelligence data in an incredibly granular way, allowing you to drill down into the areas of interest that specifically affect your NGO. The most obvious of these tools is the ability to filter by country and continent, as you might expect, but we also have other tools that let you focus even more directly on your operations.
As mentioned above, the areas your organisation may be required to operate in may straddle borders, or be located within a specific region of a country or even town. The ability to geofence a specific area allows you to filter out any other irrelevant data and focus entirely on the intelligence that relates to that location.
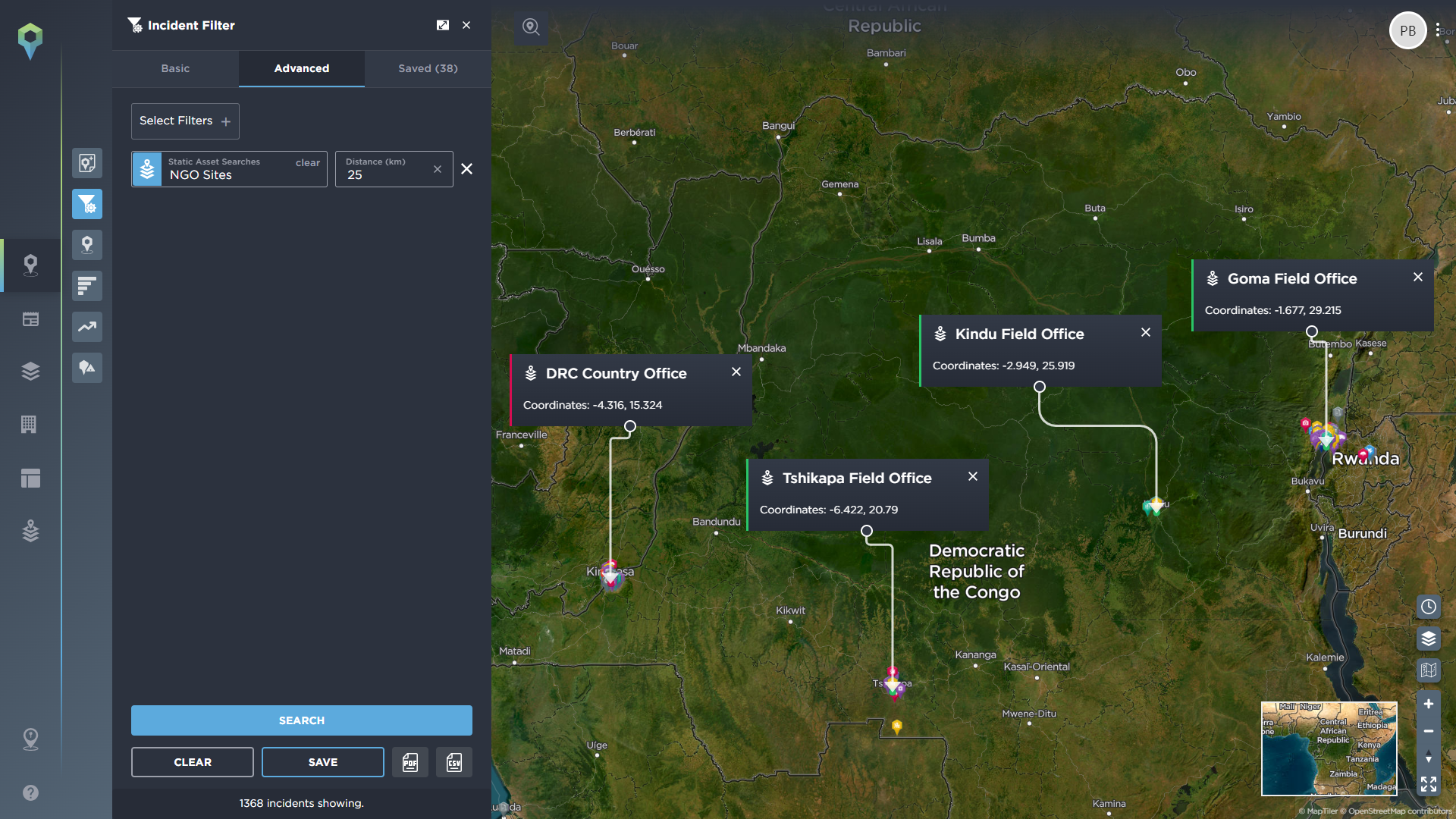
Users can also use our static assets management feature to build up a complete operational profile of your mission – mapping the exact locations of your planned deployment, and then filtering for incidents within a specific geographical radius of these assets.
You can then use these tools to understand the threat environment within your areas of operation – as we all as for other activities, such as carrying out an effective route threat assessment.
Identifying the threats to your NGO
Once you have drilled down into the locations you will be operating in, you can begin identifying the threats that your organisation might face in these areas. These threats can be broken down in a number of ways, from physical threats, such as the risk posed by criminality, to organisational threats, such as corruption or political interference, and environmental threats, posed by extreme weather or outbreaks of disease. They can also vary from risks specific to the sector or general threats related to the locality.
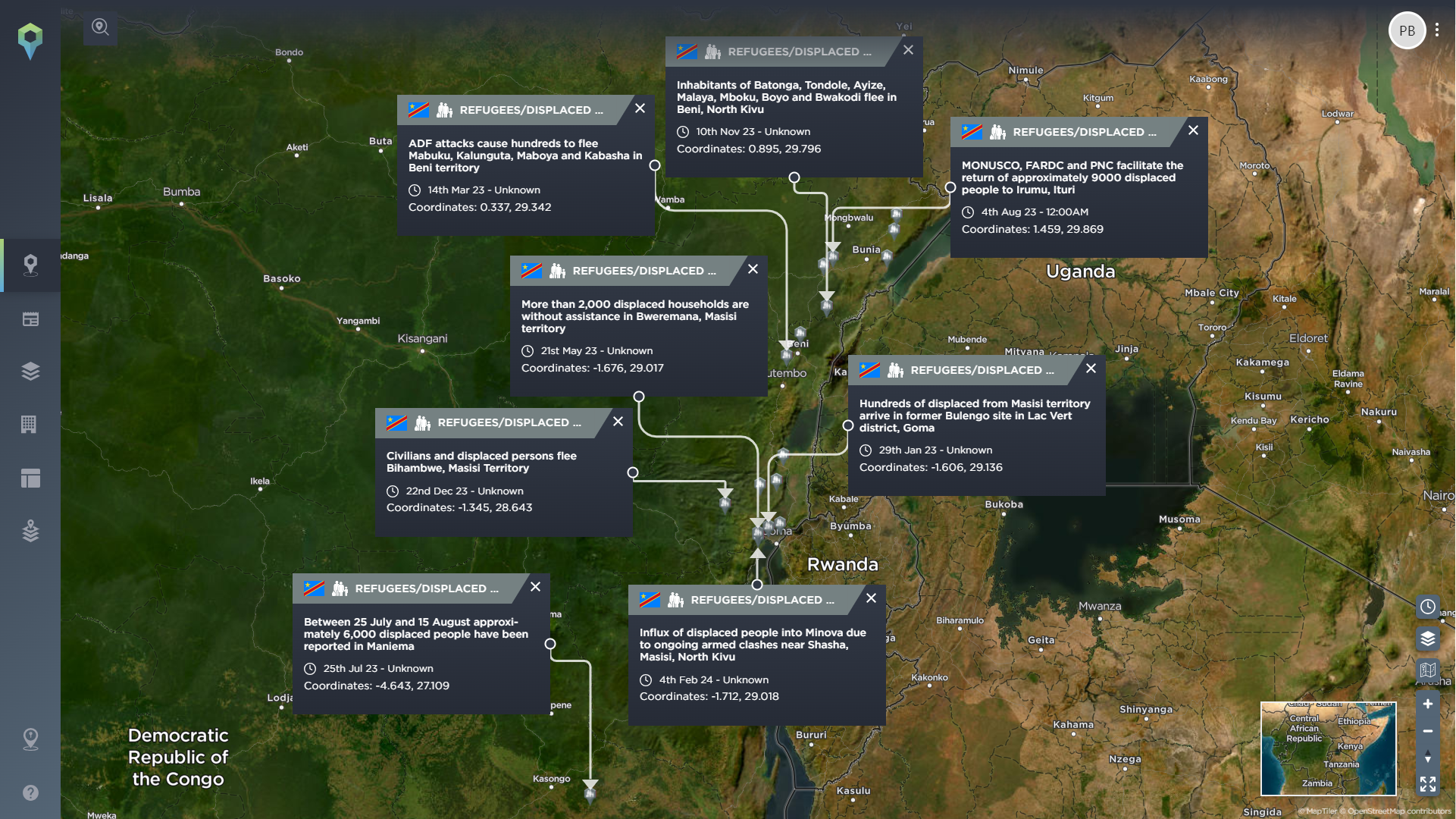
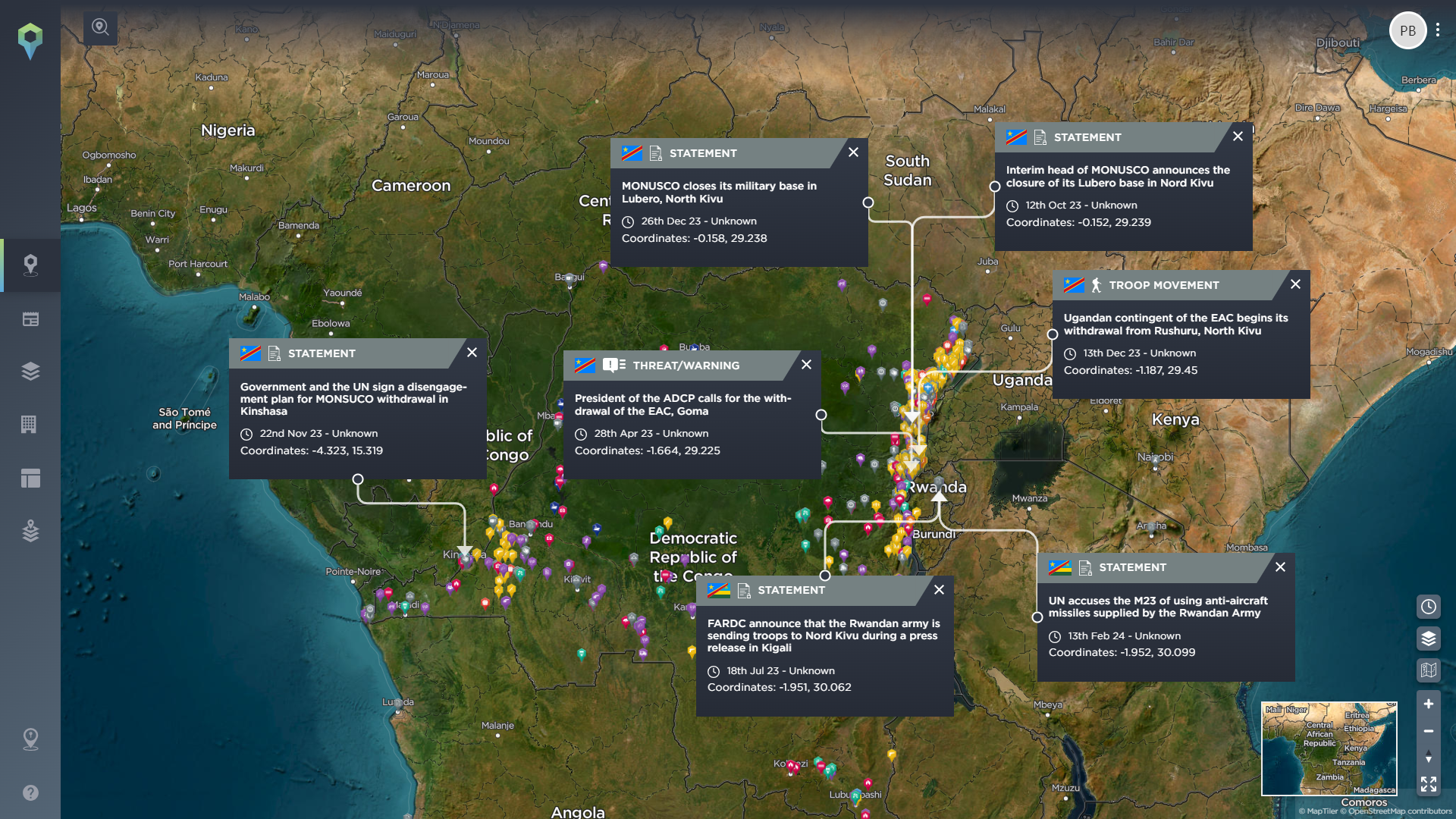
If you want to begin by seeing the types of incidents that have directly impacted the NGO sector, the Intelligence Fusion platform makes this possible. Whenever one of our intelligence analysts maps a new incident on the platform, as part of the process, they identify any sectors affected by the incident. This means that you can filter by affected sector within the platform and immediately see any incident that has directly impacted NGOs in the past, allowing you to quickly understand the sorts of direct threats that your organisation may have to deal with on their deployment.
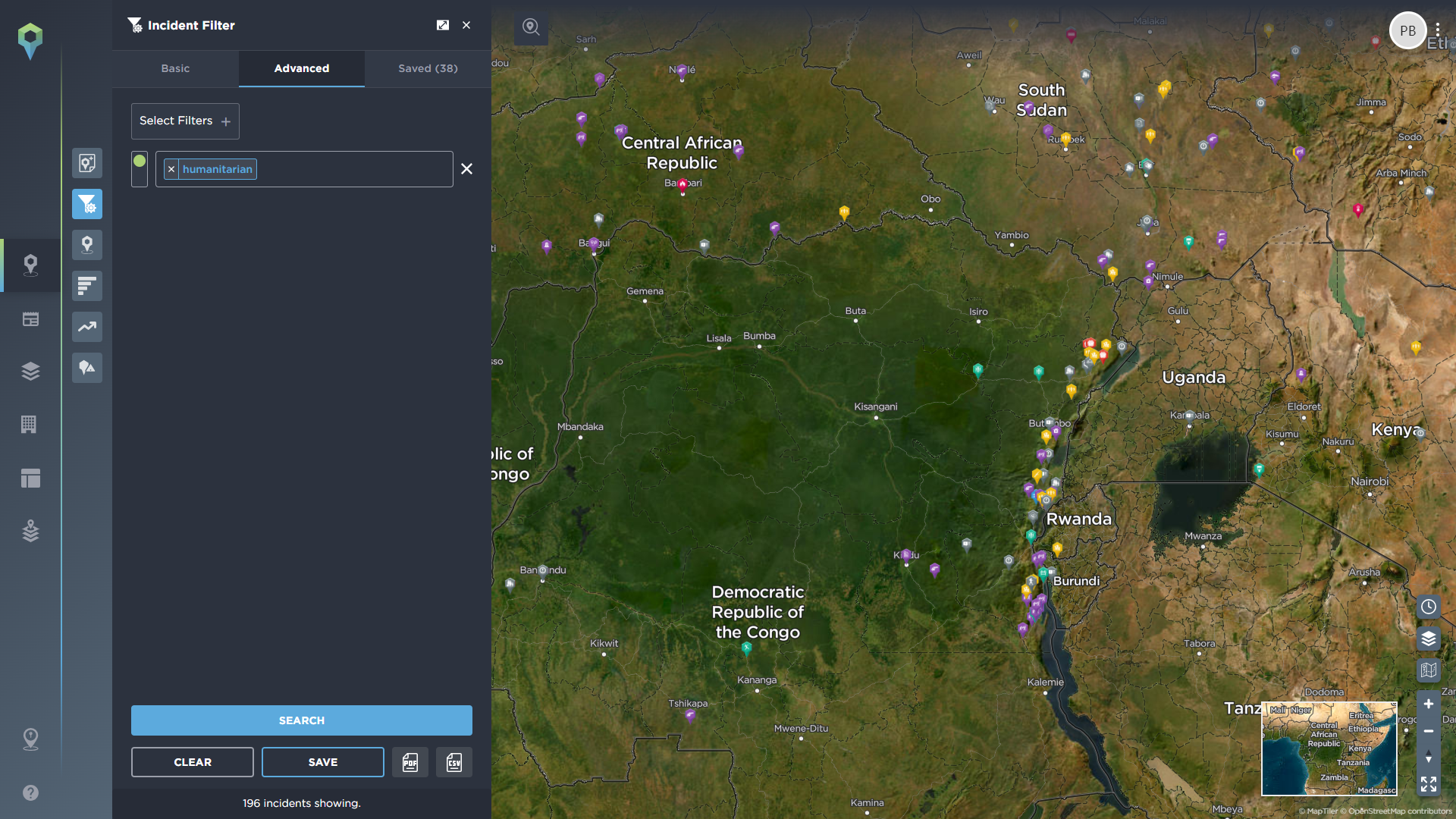
There are also a number of specific tags that our operations team uses when mapping an incident. As you can see in the image above, we have filtered for incidents that have been tagged as #humanitarian by one of our analysts, all of which have been accurately placed on our global map. This can then be further broken down by other categories, for example, by date, country, or even a specific area, so that you see the information that is most relevant to you.
Beyond incidents that have directly targeted or impacted specific sectors in the past, it is also vital to know about the general context of the threat landscape and any threats that may impact your operations and your people.
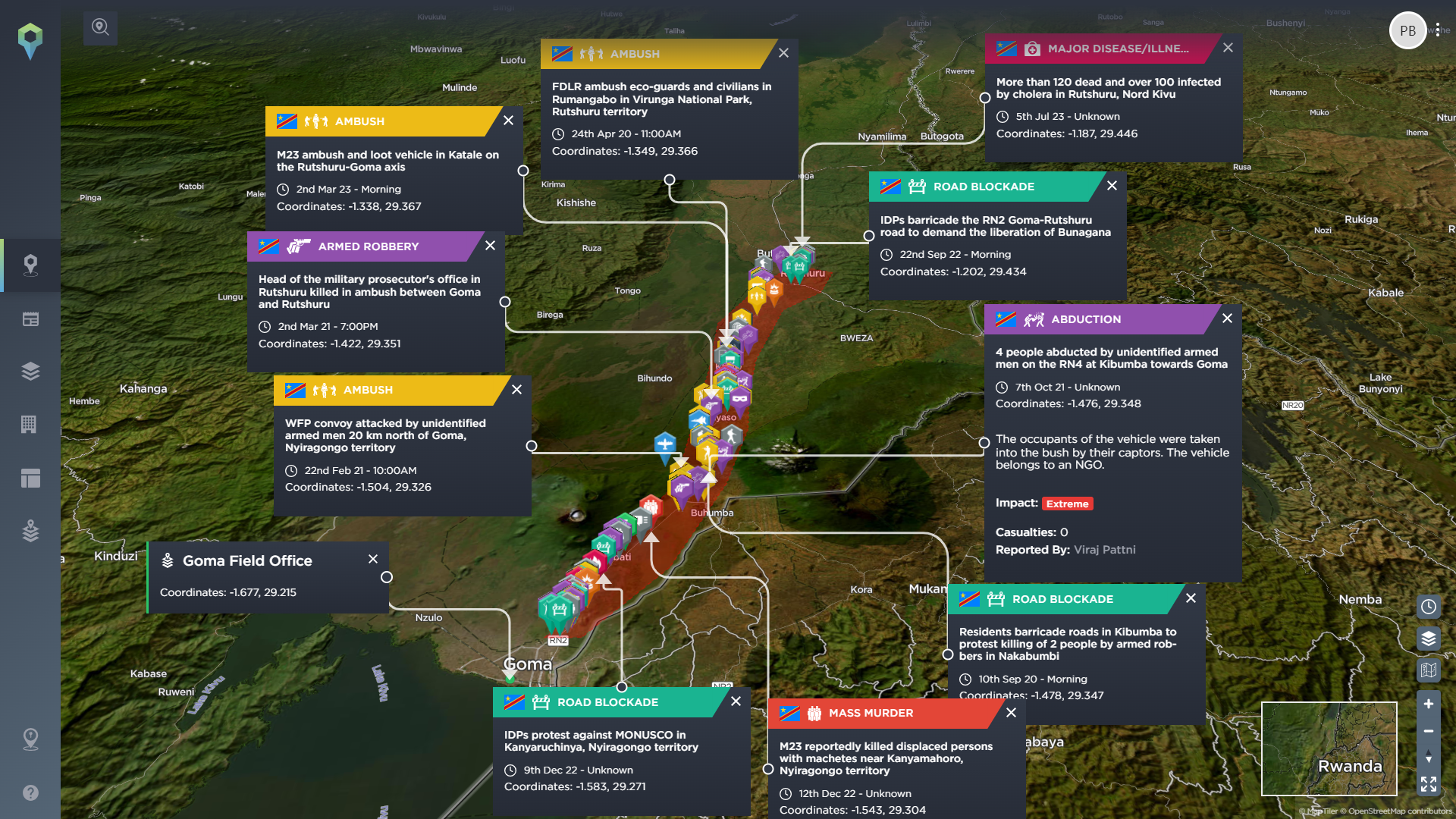
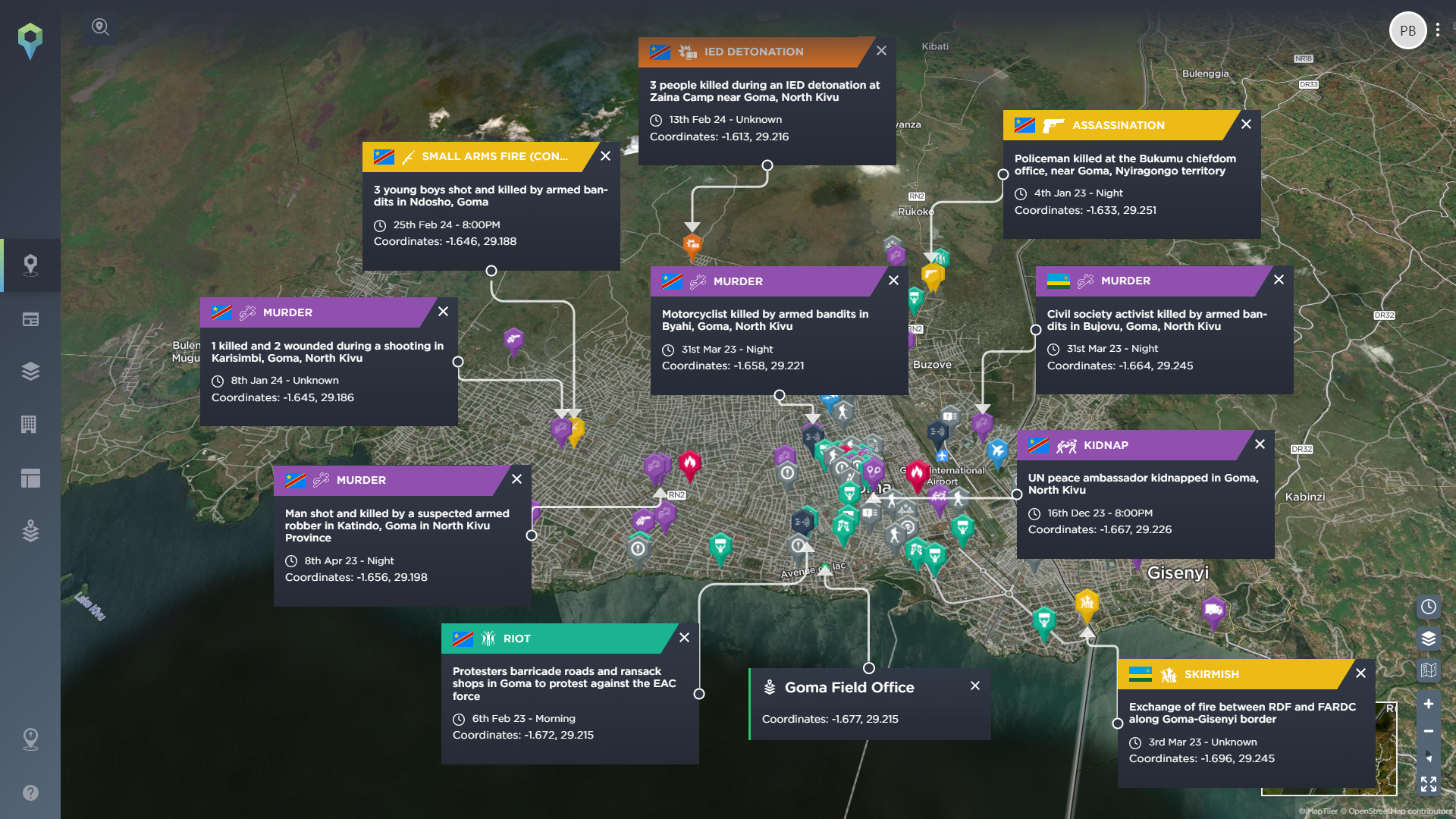
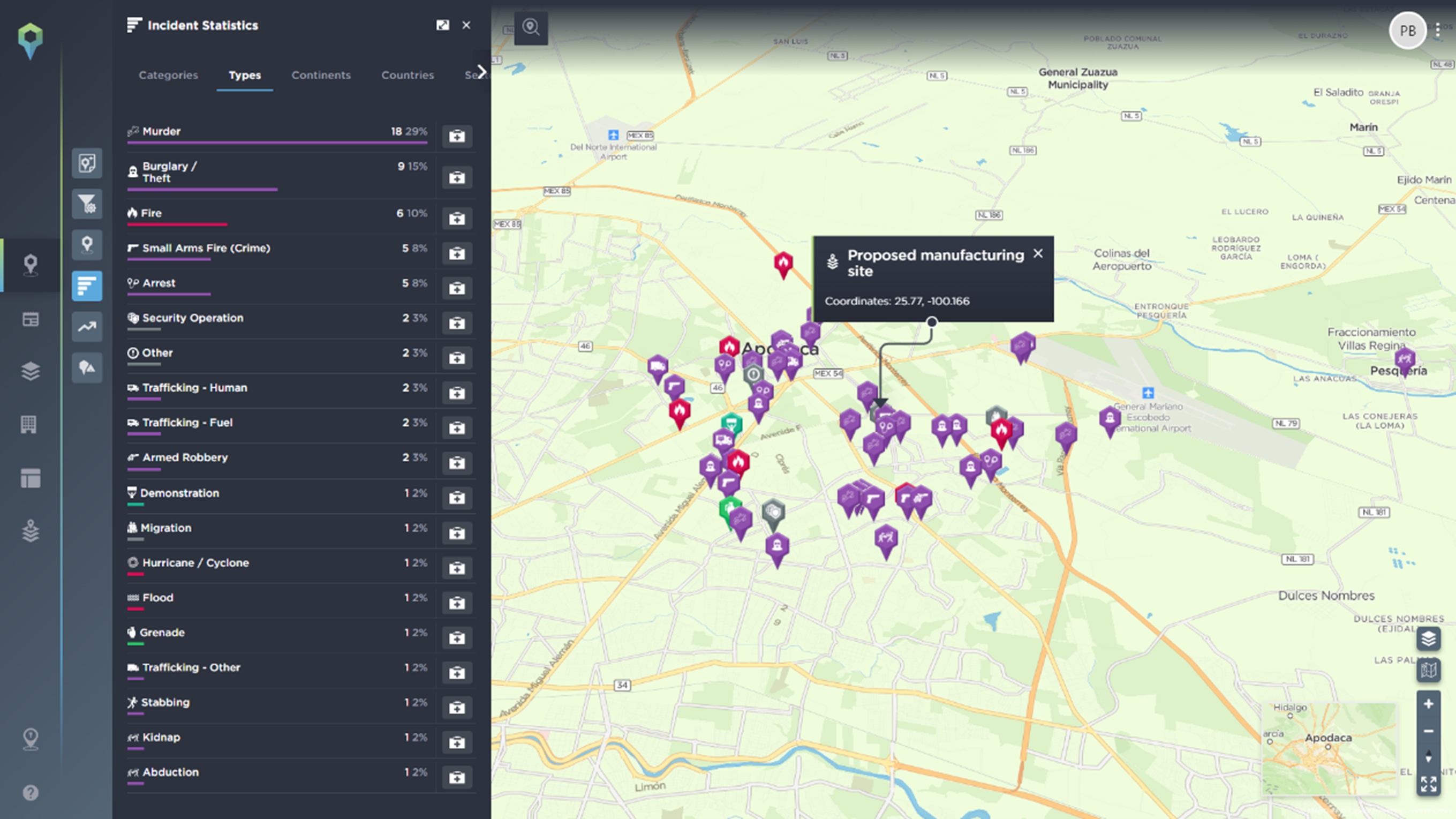
Physical threats such as armed robbery, kidnapping or sexual violence, or armed conflict, including terrorism, mass murders or warfare, are key factors to be prepared for. By using the Intelligence Fusion platform, you can filter from nearly 160 different incident types, broken down into 11 different categories, allowing you to quickly and easily look for the common physical threats in the area. These categories include criminality, direct and indirect weapons, bombing and grenade, and suicide/complex attack incidents.
This could help you identify roads that are particularly prone to ambushes and hijacking, areas with high levels of crime and the tactics utilised by local criminals, or monitor the spread of violent armed conflict in the region, to name just a few. You can also use this to track the incidents that indicate potential changes in the operational environment – what to look out for as potential early warning signs before more severe threats emerge.
Our coverage also includes those incidents that might pose an organisational threat to your NGO. This could include instances of corruption and fraud, political developments that might impact your NGO or incidents that could represent a reputational risk to the organisation without proper due diligence.
Protest activity is another factor that is important to be aware of – not least because demonstrations often take place along common routes or in particular locations. Being aware of these areas will reduce disruption to you and your team when a protest breaks out. They are also an excellent way of understanding any existing and historical grievances that you should take care to avoid inflaming.
We also map non-traditional threats, such as hazards that can cause safety and disruption risks to your operations. This includes extreme weather and natural disasters, such as flooding, droughts, hurricanes and more, as well as the spread of disease.
Who are the actors to be aware of?
When starting a new programme or deployment in a particular region, it is important to understand the actors within the operating environment that can impact upon your security and operations. Who are the key individuals, organisations, state institutions and non-state actors that will affect your organisation? What power do they have, what is their social or political position, what activities do they carry out or have they carried out in the past? Are there any armed groups in the region that present a security threat? What about political activists? How much contact might they have with your NGO, and what interest might they have in your operations?
Failing to understand the dynamics within the local area can lead to security and operational failures that can have serious consequences for your NGO, including risks to the safety of your employees or the forced expulsion of the organisation.
As part of the risk assessment, mapping the key actors ahead of time, including their interests, how they interact with each other and the local community, as well as how they will potentially interact with the NGO, is an important early step. The more context you can gain about these groups, the better. Using a tool that can help you gain an understanding of the interests, past actions, and potential tactics of different actors will greatly assist this process.
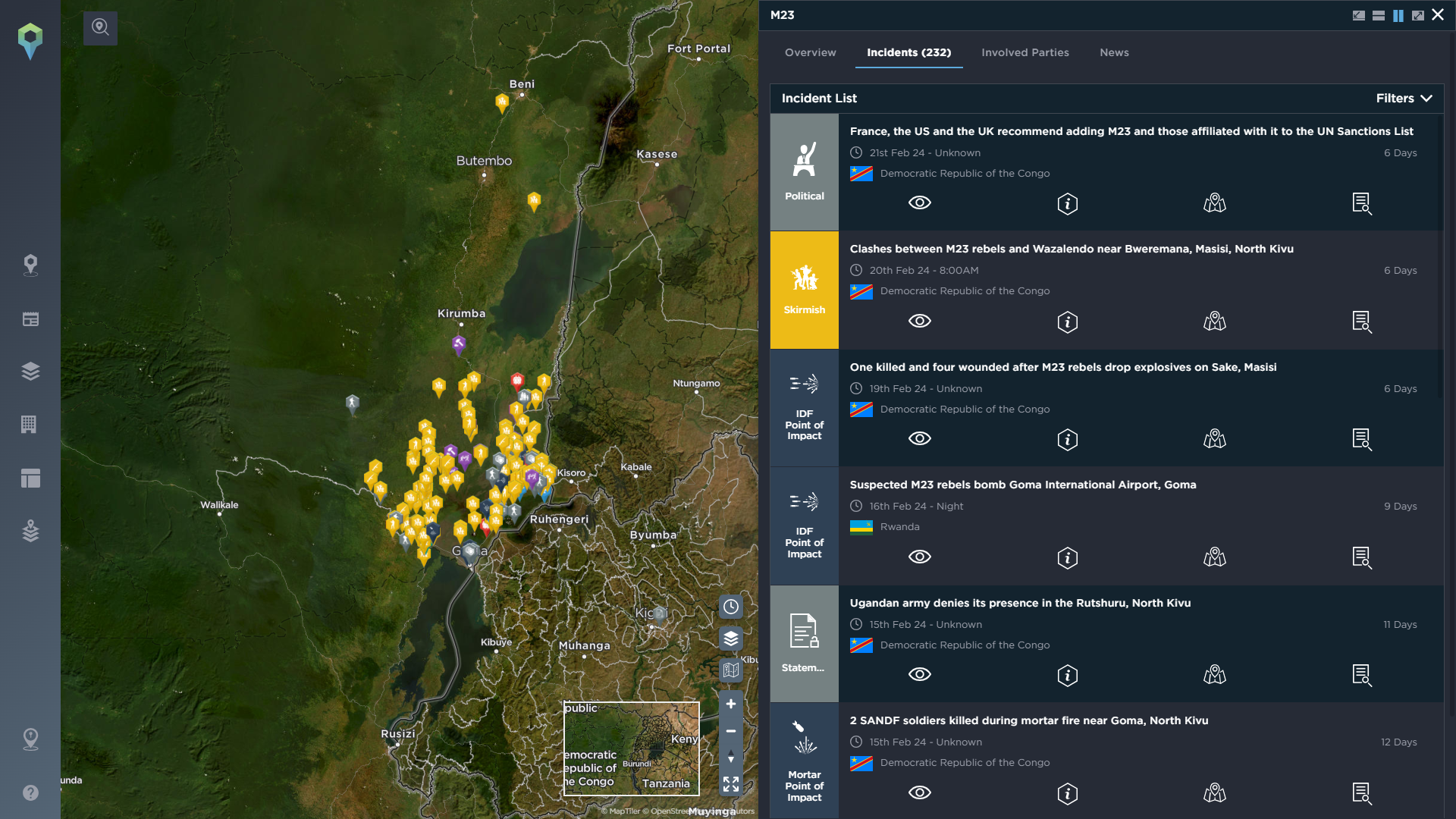
Once you’ve gained an awareness of the actors in the area, you can learn more about their common areas of operation, preferred tactics and historical activity by using the ‘involved parties’ filter on the Intelligence Fusion platform. This allows you to easily filter for any incidents involving a particular actor so you can see how, for example, certain criminal networks behave in the area, or their activities in a wider context, and note what kind of threat they may pose to your NGO’s operations.
You can also gain a deeper understanding of a particular actor via the actor profiles we offer on the platform. This additional feature provides detailed information about one of the actors identified on our database, with a brief summary of the history and activities of the actor, their areas of activity, a filtered result of incidents they are involved in, and more. This helps you quickly gain an overview of each group’s activity, get a better understanding of where they operate and allow you to monitor the changes in their movements, before conducting more in-depth research via our threat intelligence data.
Tracking the geopolitical context
While threat intelligence data is a key tool for informing your risk assessment in specific deployments, projects or locations, it can also play an important role in a more global, company-wide context.
Tracking geopolitical risk is a vital concern for the C-Suite across industries, and this should also be the case for NGOs, too. Understanding the global threat landscape, and how it is impacted by and reacts to geopolitical developments, better allows you to understand the level of risk across your global operations, as well as forecast potential new threats or areas of risk. It can also help you stay ahead of developing areas of need as global geopolitical events begin to play out on the ground.
As we explain here, while geopolitical risk is difficult to quantify and track compared to other areas of risk, using threat intelligence data can help make this a more accomplishable task.
A comprehensive level of threat intelligence coverage can help reduce the number of the ‘unknown unknowns’ within your risk planning, increasing your knowledge of which potential risks might impact your organisation. This, in turn, can assist with geopolitical risk assessments, with the data further serving to provide evidence for the analysis of those responsible for advising the NGO on geopolitics.
Threat intelligence data can also allow you to track the real-world impact of geopolitical developments as they unfold. For example, while geopolitical experts can advise on the likelihood of regional escalation in the ongoing Israel-Palestine conflict as other actors threaten to get involved, threat intelligence data can demonstrate the increase in Houthi rocket and drone attacks and the threat to shipping in the region from prior actions carried out by the group and its allies. This allows you to track the spread of violence in a more tangible way.
It can also help with horizon scanning and scenario mapping by providing examples of how similar situations have developed in the past, therefore assisting both your security and risk management teams in addition to your geopolitical advisors and ultimately helping you make informed decisions when responding to the geopolitical – and security – landscape. To continue with the previous example, as attacks on shipping continue, and vessels avoid transiting via the Red Sea and Suez Canal, this could have a knock-on effect on Egypt’s economy, leading to greater financial hardship and – potentially – an increase in need for aid from NGOs. This allows you to begin preparing for those scenarios you deem as likely to occur, before they happen, giving you a head start when it comes to reacting to a quick-developing situation.
Conducting your NGO's risk assessment
After understanding the full context and gathering your threat intelligence, you can then use this to put together a comprehensive risk assessment and put effective risk management measures in place.
In simple terms, this process involves identifying the threats based on your intelligence gathering; evaluating the threat level and the organisation’s exposure to risk, including who and what will be at risk, what the impact will be, where the risk is greatest; and then developing risk mitigation strategies to reduce the probability of an incident from occurring, and to reduce its impact.
Your in-house team will be able to use their expertise to put this intelligence to effective use, but you can also work with industry experts to create bespoke risk evaluations and mitigation plans. Companies such as RSM have an impressive track record when it comes to consultancy on strategic, operational and tactical level risks, including working directly with NGOs to better protect their operations, their assets and their people. For more information on the services they provide, click here.
Once you have compiled your risk assessment, and your risk management plans and processes, you can upload them to the document repository on the Intelligence Fusion platform. This additional feature allows you to streamline your processes by creating a central system to store, manage and share relevant documentation, giving you direct access to reports, files and digital documents, all of which can be tagged and filed against assets, countries or groups. This can be accessed by anyone within your team who has access to the platform, regardless of where they are in the world.

What are the biggest threats facing NGOs in 2024?
As organisations that are often based in some of the most dangerous locations in the world, NGOs are potentially exposed to more risk than most other companies – so what should they be braced for in 2024?
Learn more about what others in the industry think of the current threat environment for the sector. Featuring an in-depth discussion between Chief Security Officers from different humanitarian aid companies and risk and resiliency experts from Sigma7, our panel delved into some of the key dynamics shaping the threat environment for the industry – available to watch on demand now.
Watch the webinar on demand now