Tracking armed conflict using threat intelligence software
How to use threat intelligence software for tracking armed conflict across the globe, so you can keep your people, assets and operations safe.
For many businesses, operating in conflict zones is a simple fact of life. With armed conflicts found across the globe, from the Donbas conflict and the threat of Russian invasion in Ukraine, to jihadist insurgencies in West Africa or the Middle East, and civil wars in South America or Southeast Asia, being able to track armed conflict activity is therefore essential for business operations in a wide range of industries, operating in vastly different parts of the world. Multinational companies in the extraction industry, for example, are bound to the location that their resources are found, and so relocation from conflict zones is not an option, as are companies from these countries and regions themselves, while humanitarian aid agencies will, naturally, be frequently operating in areas of conflict due to the nature of their work. For these companies, and many others, tracking armed conflict is essential.
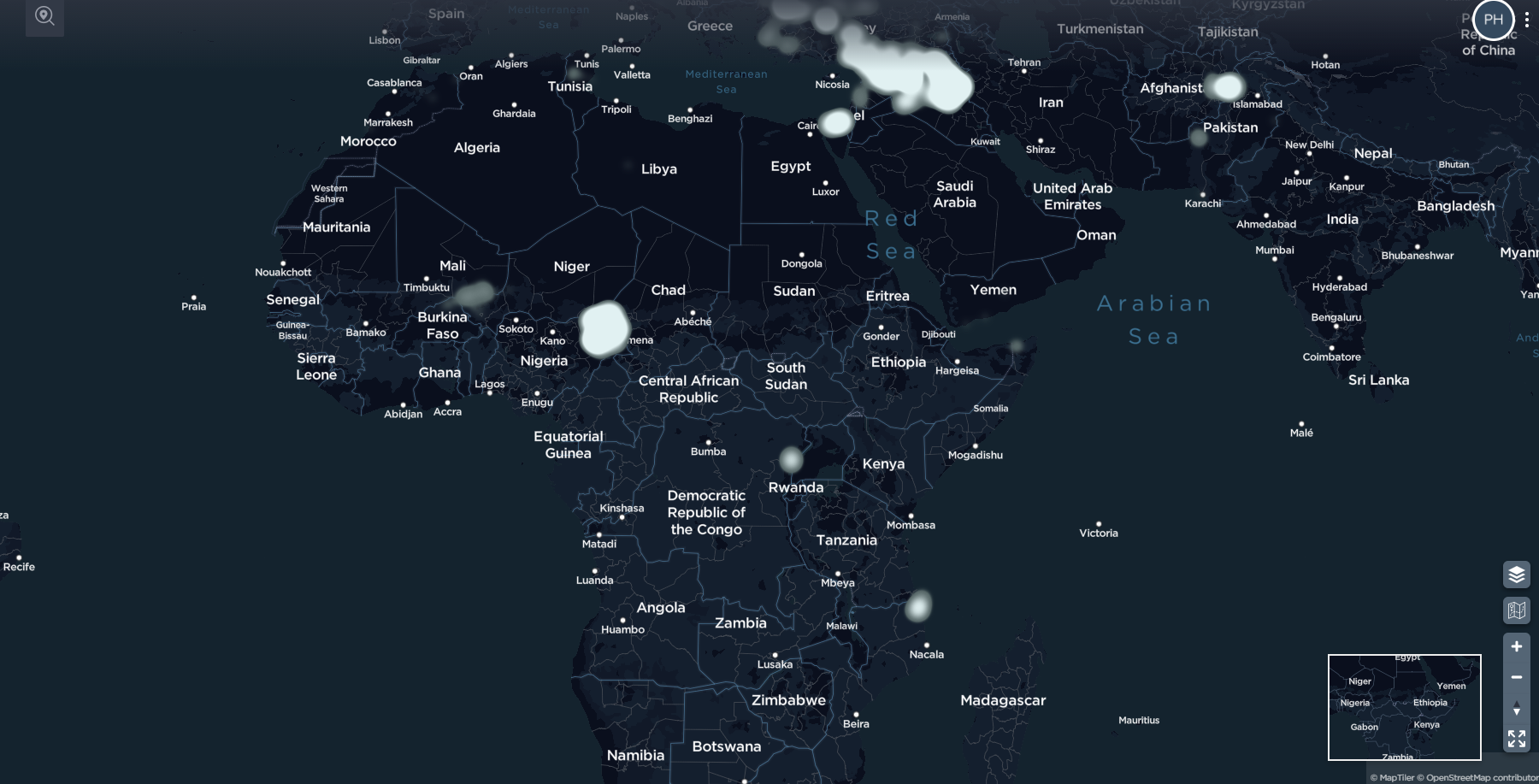
The 10,000 most recent direct and indirect weapons, complex attacks, bombings, grenade and air-related incidents mapped on the Intelligence Fusion platform [image source: Intelligence Fusion]
Being based in areas of armed conflict obviously presents a series of complex issues to business operations, with the safety and security of staff, risks to business continuity, transport and logistics, and even the viability of the operations themselves all a cause for concern. So a solution that can map, monitor and track armed conflict – and give you the tools to easily identify the areas of greatest risk – is therefore a must for any organisation based in a conflict area.
Increasingly for businesses, regardless of industry, this means embracing threat intelligence and situational awareness, with modern security teams now recognising it as a prerequisite for a comprehensive security programme, rather than a bonus.
Why should businesses track armed conflict?
As broken down in a 2014 paper by the SOMO, conflict itself can be broken down into different key phases: latent conflict, where there is currently no open armed violence, but where significant political, social and economic instability prevails; open and sustained violence, where there is currently organised armed violence in parts of or all of a country’s territory; and conflict settlement or resolution, where countries are transitioning out of armed conflict or have experienced armed conflict in the recent past.
[image source: ‘Multinationals and Conflict’, Stichting Onderzoek Multinationale Ondernemingen (SOMO), 2014; ‘Private sector development in conflict-affected environments’, DCED, 2010]
As mentioned above, many organisations have no choice but to operate in areas of conflict, including these areas of open and sustained violence – consequently facing a greater level of operational risk due to the myriad of different threats associated with these areas. Conflict zones often feature increased political instability, stretched, damaged or poor infrastructure, high levels of corruption, an uncertain operating environment, thorny structural and cultural issues such as ethnic or religious tensions, high levels of human rights abuses, increased opportunity and motivation for criminality, and – of course – the threat to safety and security that comes with direct armed conflict itself.
By operating in such an environment businesses have a greater responsibility for the security and protection of their workers, who are at greater risk to their safety than in a traditional operating environment. In areas of intra-state armed conflict, for instance, insurgent armed groups will often use kidnapping for ransom as a means of funding their activities, meaning workers are at greater threat of being abducted. Similarly, businesses themselves can become the target of armed groups, whether it be extortion in exchange for allowing them to continue to operate safely, or falling victim to attacks directed at their operations or workers. Many businesses might also be based in areas that are deemed relatively safe, only for existing armed conflicts from other parts of the country – or across the border – to spread closer and closer to their areas of operation, suddenly putting their business at risk.
Businesses themselves need to be careful not to exacerbate existing conflicts through their actions too, whether it be being perceived to favour a particular ethnic group, becoming affiliated with or dependent on governments engaging in intra-state armed conflict or repression, or by doing business with groups carrying out human rights abuses – in some cases in parts of businesses’ supply chains themselves. Areas with weak state governance or with power vacuums may also become effectively controlled by armed actors like insurgent groups or organised crime groups, potentially making businesses complicit with illegal operations should they find themselves working with these groups.
Being able to track armed conflicts in, near, or even further away from their areas of operation, should be a key consideration for businesses, then, given the severe risk that they pose to their operations and their workers. Embracing a threat intelligence led approach is a highly-effective way to do this.
What is threat intelligence?
Breaking it down into its simplest terms, threat intelligence is the military principle of using evidence-based knowledge about existing or emerging threats to inform your response to those threats. All threat intelligence must be relevant, actionable and contextual, in order to allow your organisation to take informed, concrete action to improve its security against the identified threats – which is why we use the Intelligence Cycle for every incident that we map on our threat intelligence platform to ensure accuracy and actionability.
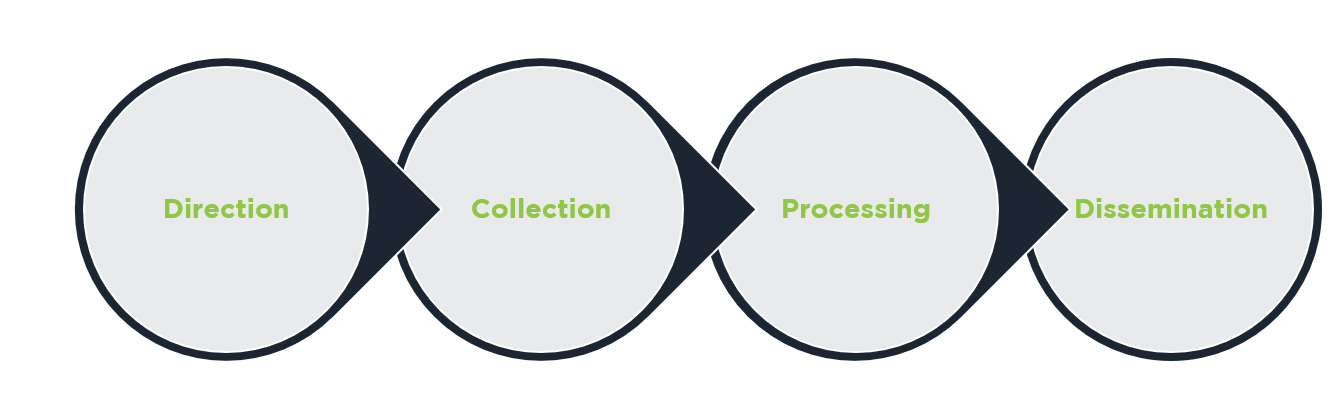
Diagram showing how the Intelligence Cycle works when processing threat intelligence [Image source: Intelligence Fusion]
This can be both historical data that allows you to identify intelligence trends and patterns, or emerging, real-time information that alerts you to active threats. Taking historical data as an example, having access to Intelligence Fusion’s database of over 650,000 incidents dating back to 2015 allows you to see which areas are most likely to see unrest, or that are particularly prone to attacks or ambushes – when planning a route, for example, you can therefore use this information to avoid these areas or particular roads for a safer route, or, if this isn’t possible, decide whether additional security measures may need to be implemented to counter any possible threat.
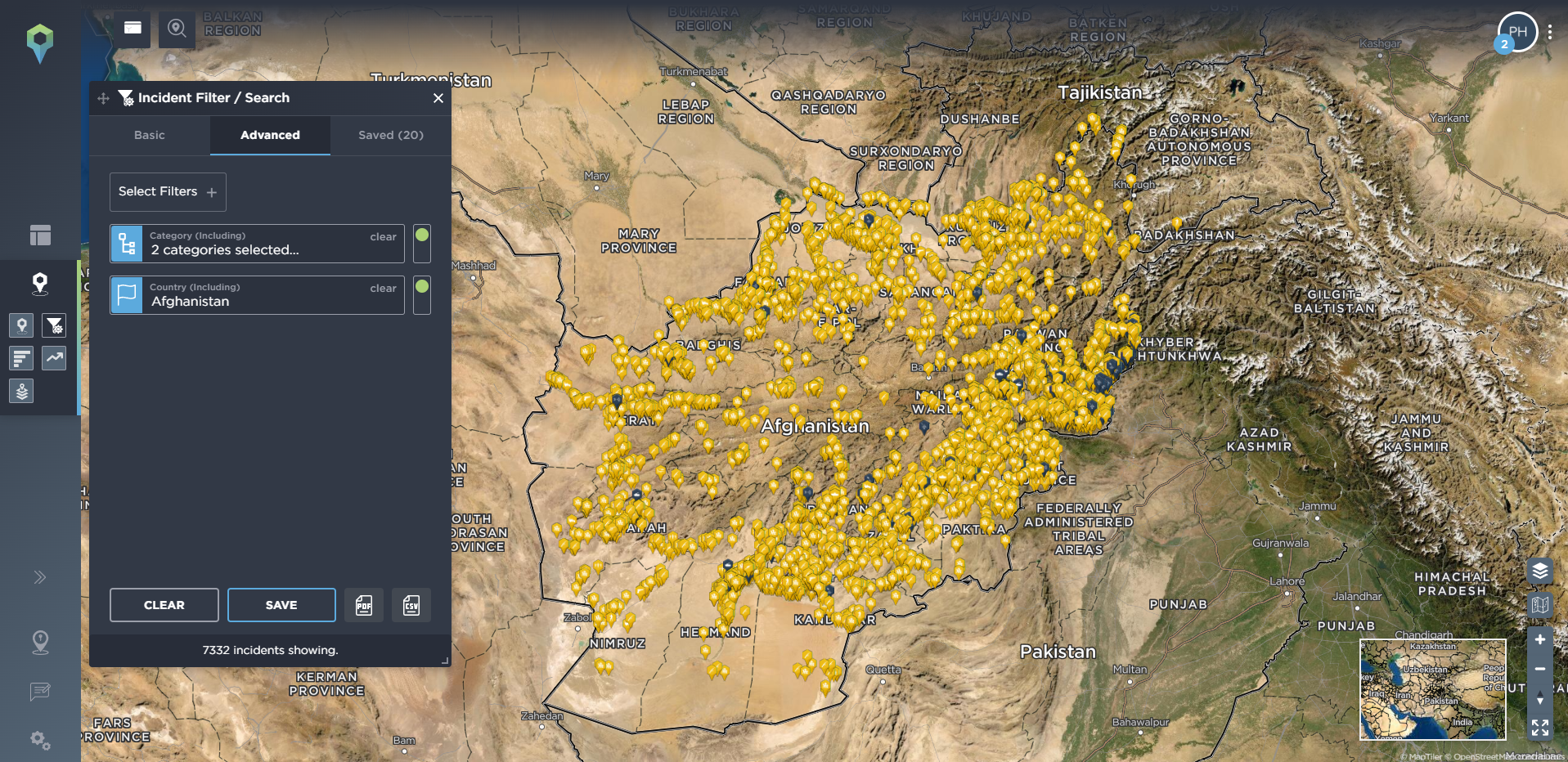
How can you track armed conflict using threat intelligence software?
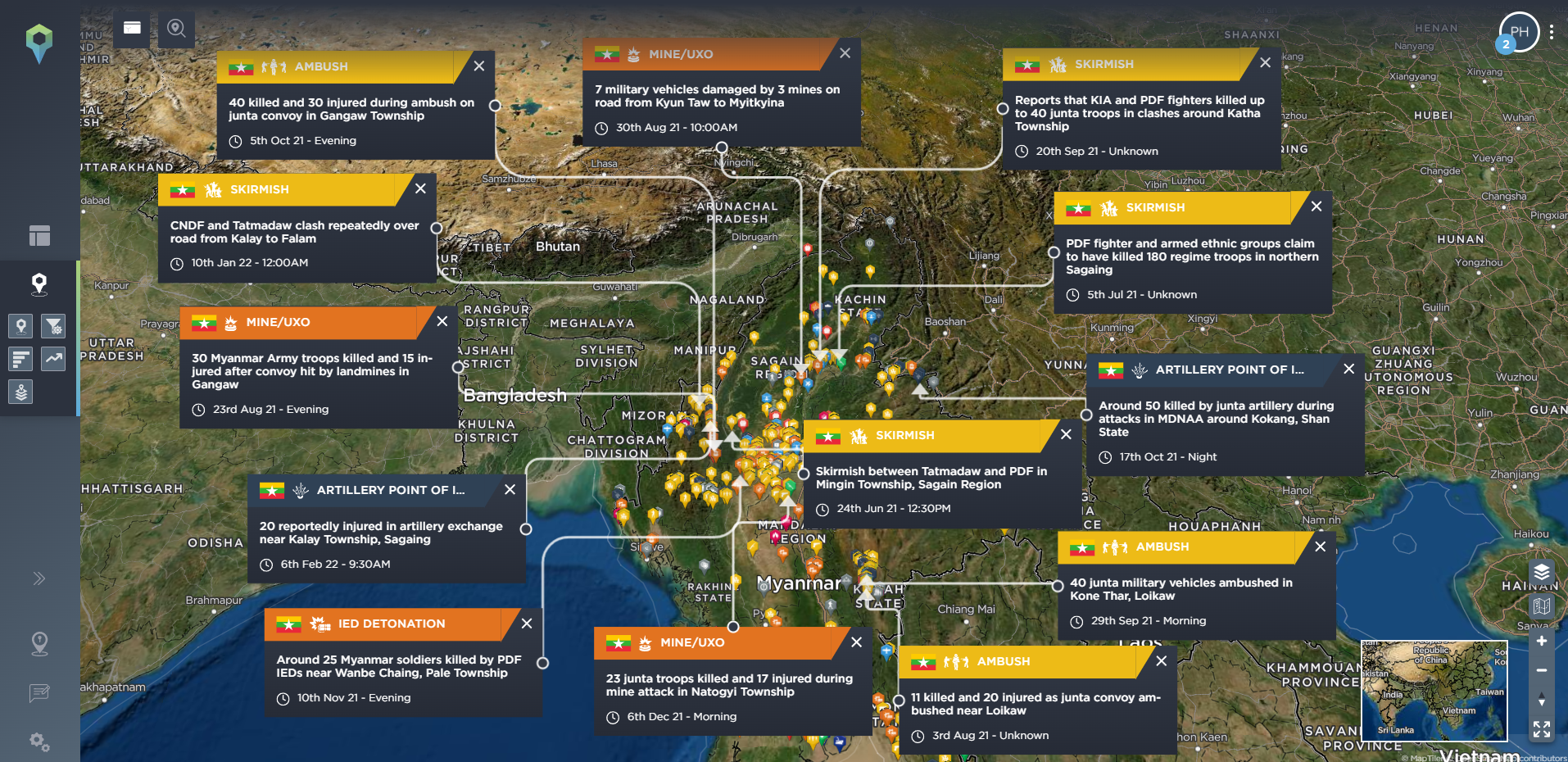
So, hopefully it should be clear why an effective threat intelligence programme is essential for keeping you, your workers and your operations safe – especially when your business operations are based in a conflict zone. Having a threat intelligence software solution to aid this intelligence programme is key to achieving this. At Intelligence Fusion we believe this means not just having a wide depth and breadth of data – as evidenced by our database of over 650,000 historical incidents across the globe, which we never archive – but also granularity of data, too. We break down our incidents into 11 different categories, covering 159 different incident types, with advanced filtering capabilities to allow you to hone in on the data that matters most for you. Your security team can then use this data to identify key trends and patterns, such as the spread of a particular conflict, the tactics and capabilities of particular groups, the areas that are particularly prone to armed conflict such as skirmishes between belligerents or ambushes from particular groups, or the times of year when armed conflict becomes more frequent.
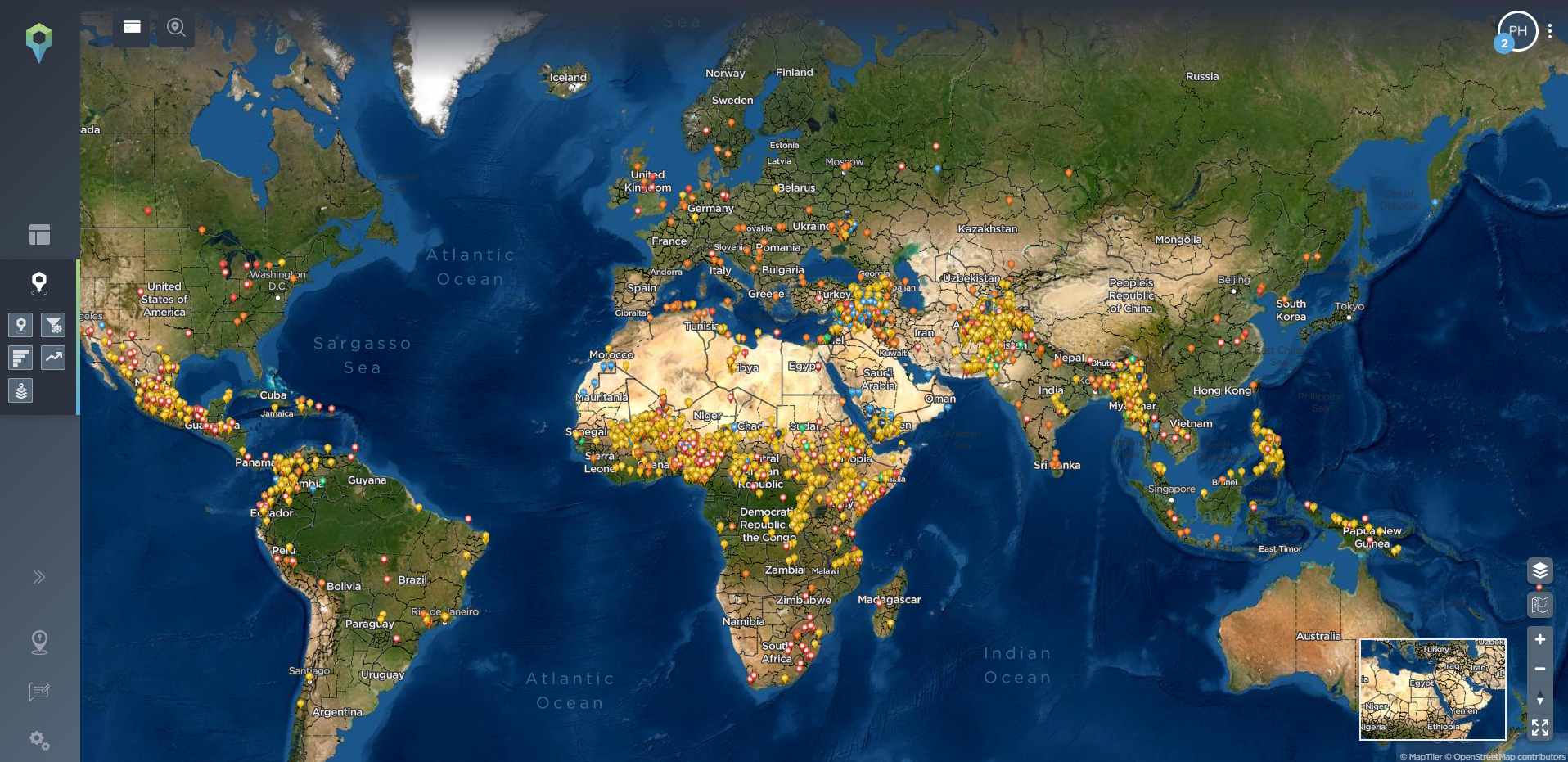
For those looking to track armed conflict, for example, breaking data down by type or category might include zeroing in on incidents from the direct weapons and indirect weapons categories, as shown below.
Direct weapons (yellow) and indirect weapons (blue-grey) incidents mapped in Afghanistan on the Intelligence Fusion platform [image source: Intelligence Fusion]
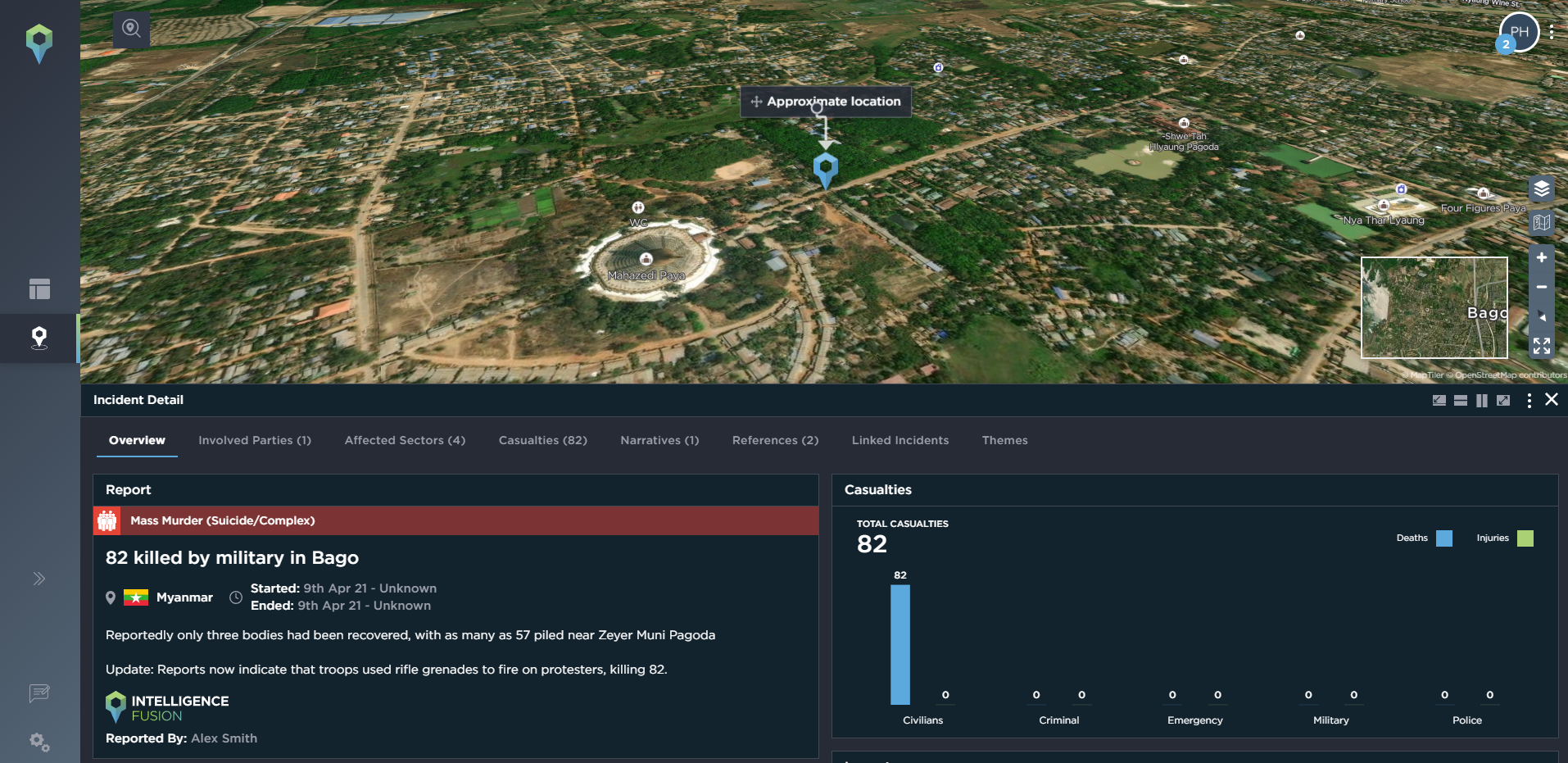
Alternatively, you may be interested in incidents of mass murder, complex and suicide attacks, or in bombing-related incidents, especially when monitoring an insurgency or terror-related conflict.
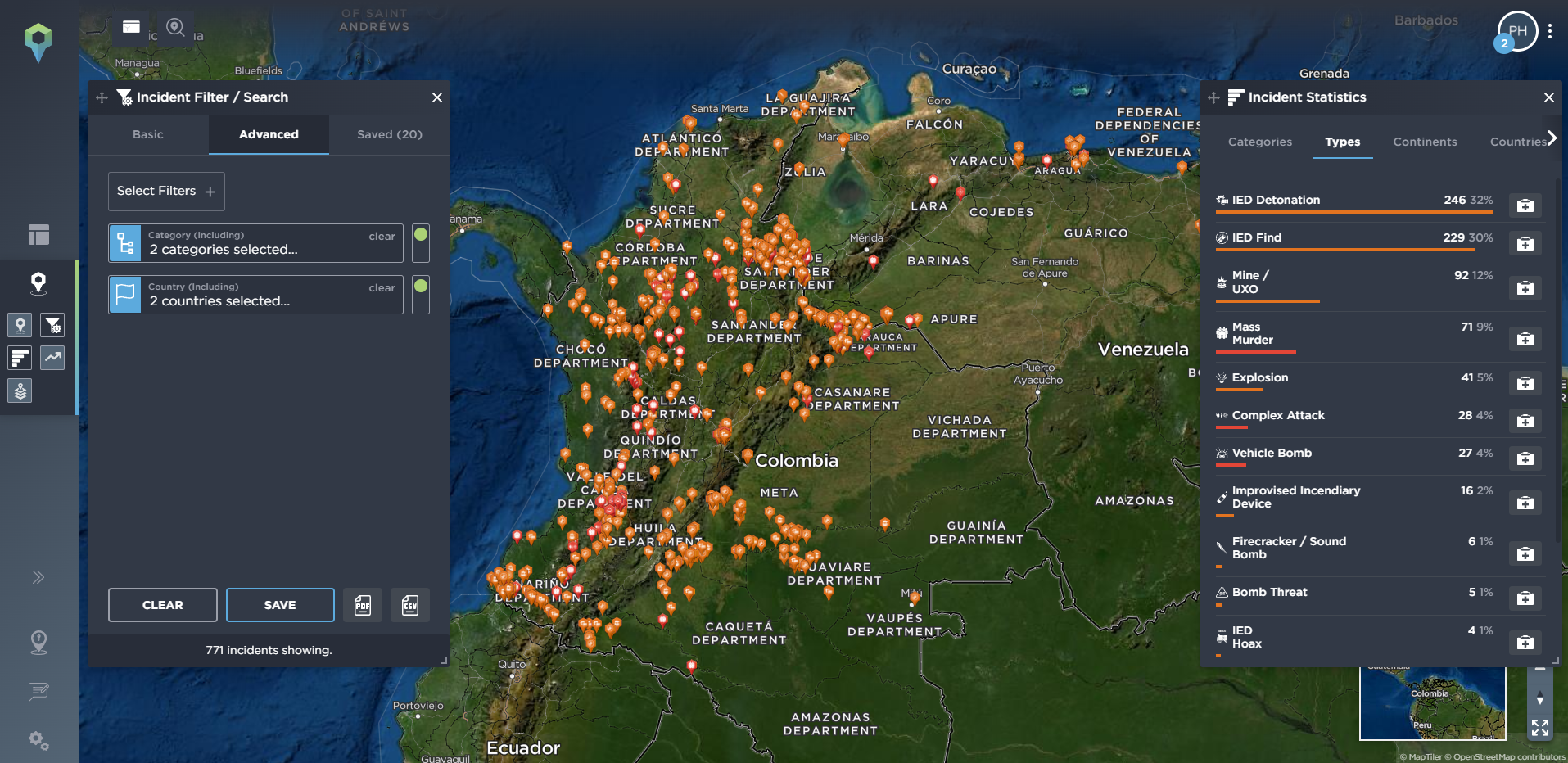
image shows the complex attacks and bombings categories in Colombia and Venezuela as mapped on the Intelligence Fusion platform [image source: Intelligence Fusion]
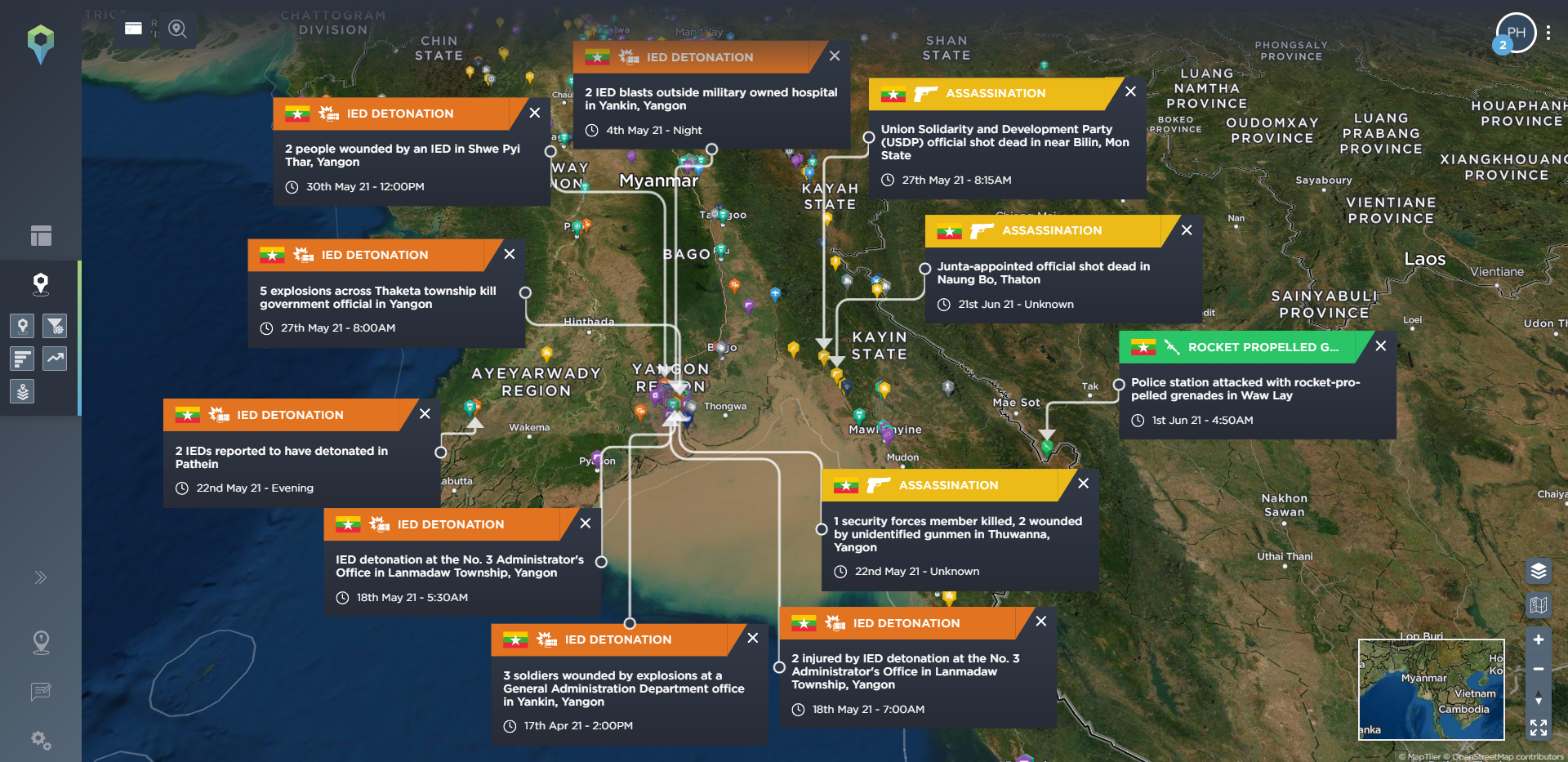
Or, if you’re simply interested in one particular type of incident, such as ambushes or IEDs, or perhaps unexploded ordinance for those operating in former conflict zones, then you can narrow it down to just those incident types, too. From there you can then further narrow it down by location and date to see, for example, all IED incidents in Iraq since January 2018.
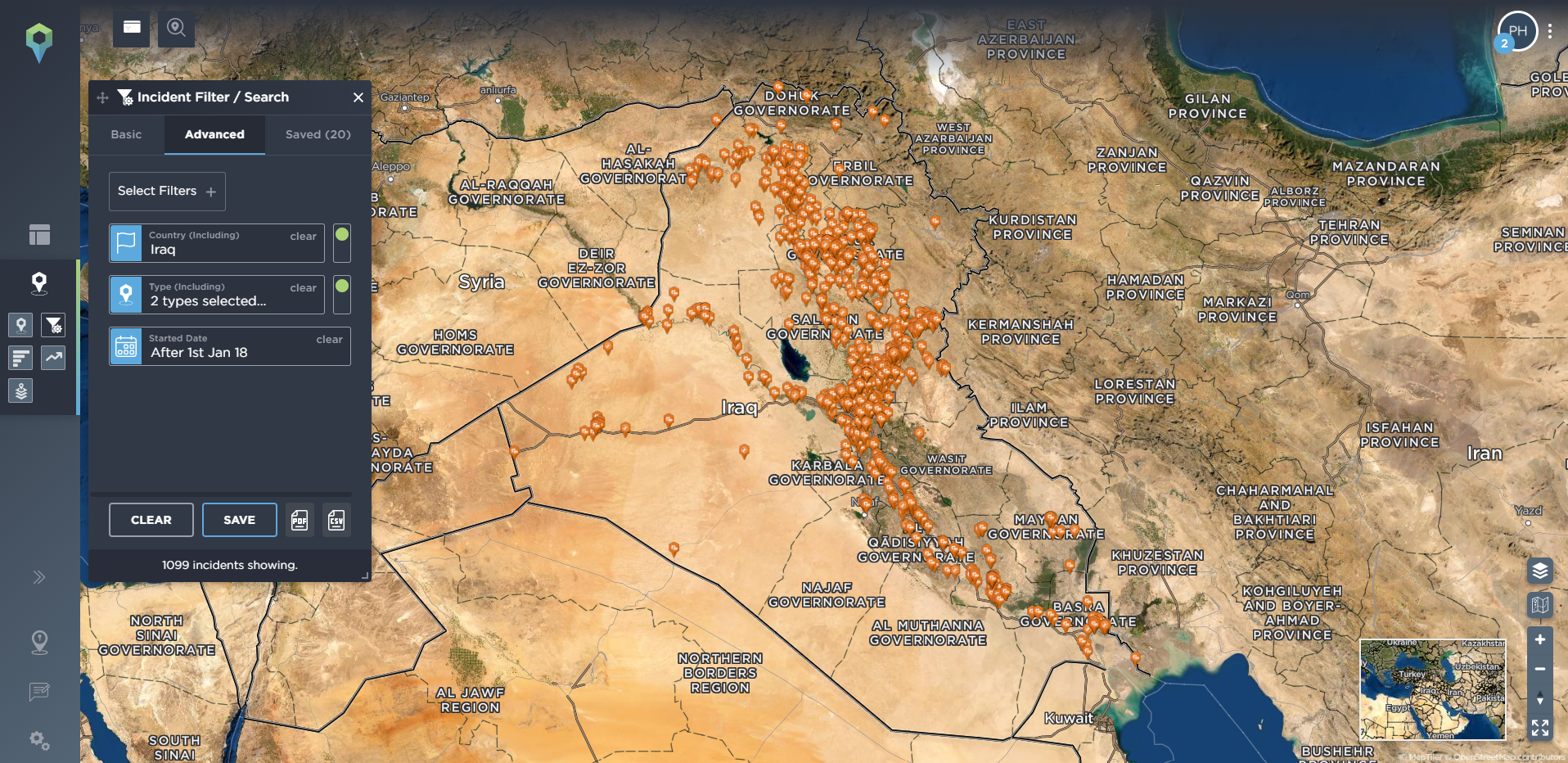
IED detonations and finds in Iraq since January 2018 [image source: Intelligence Fusion]
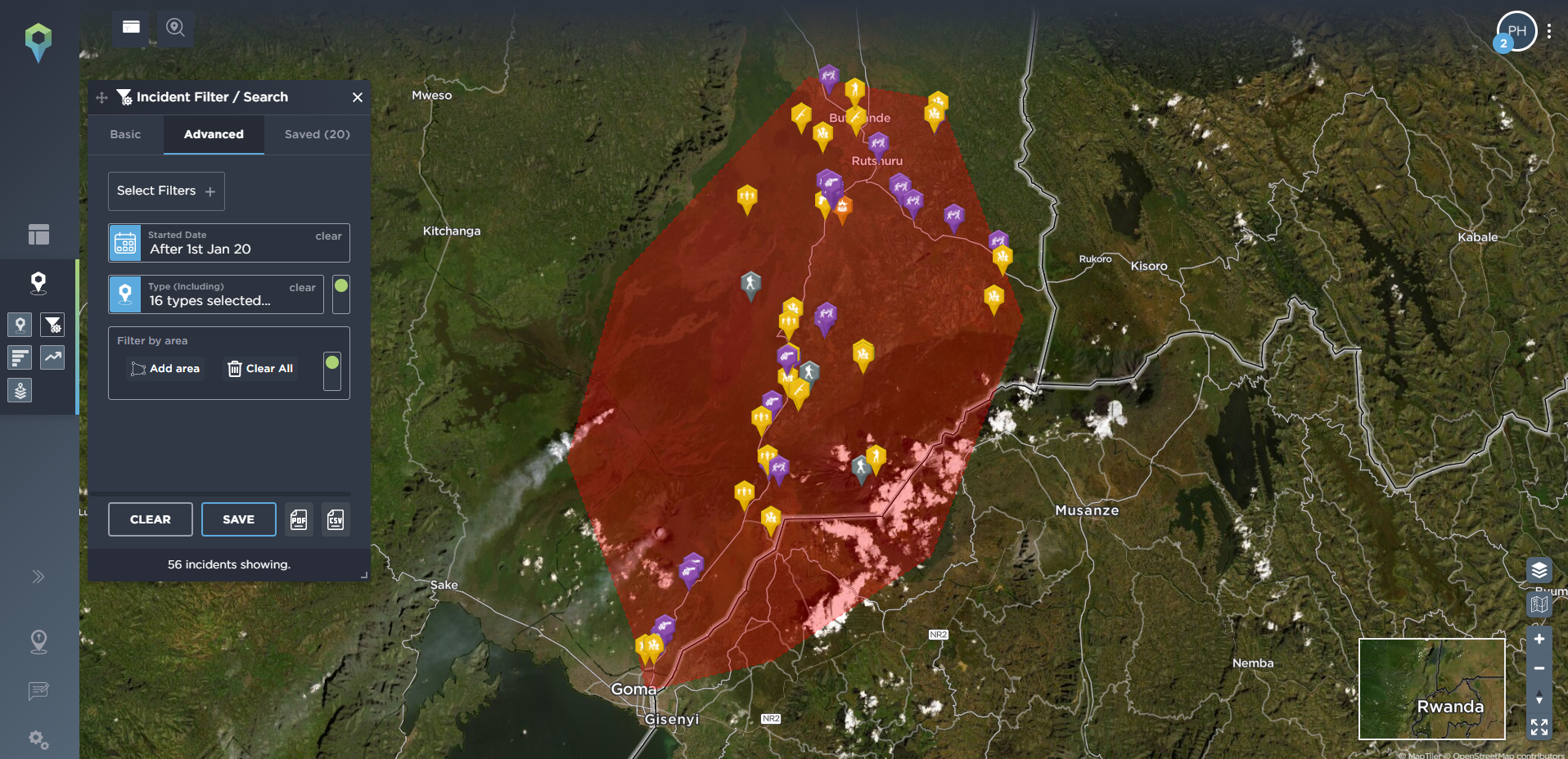
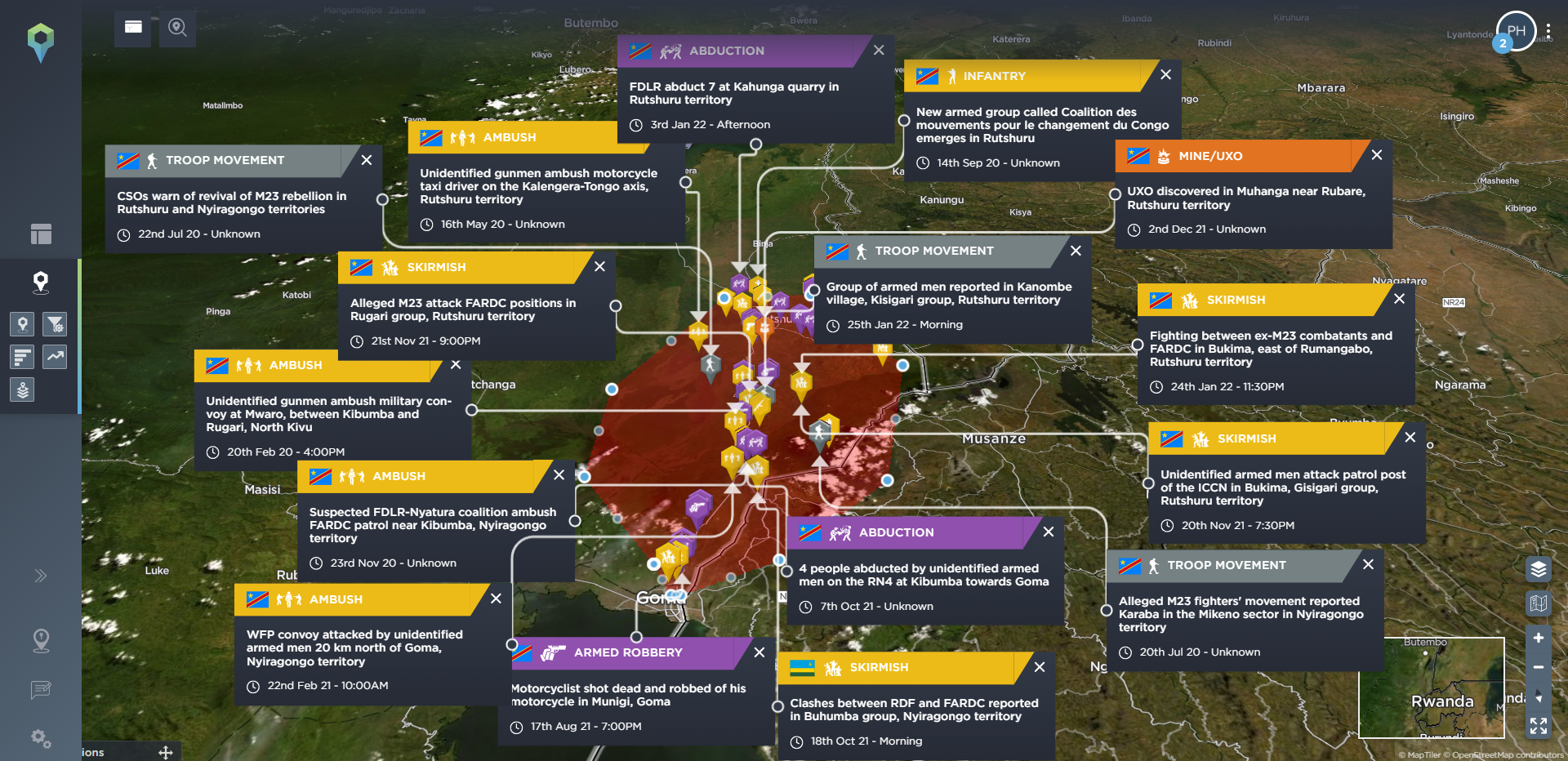
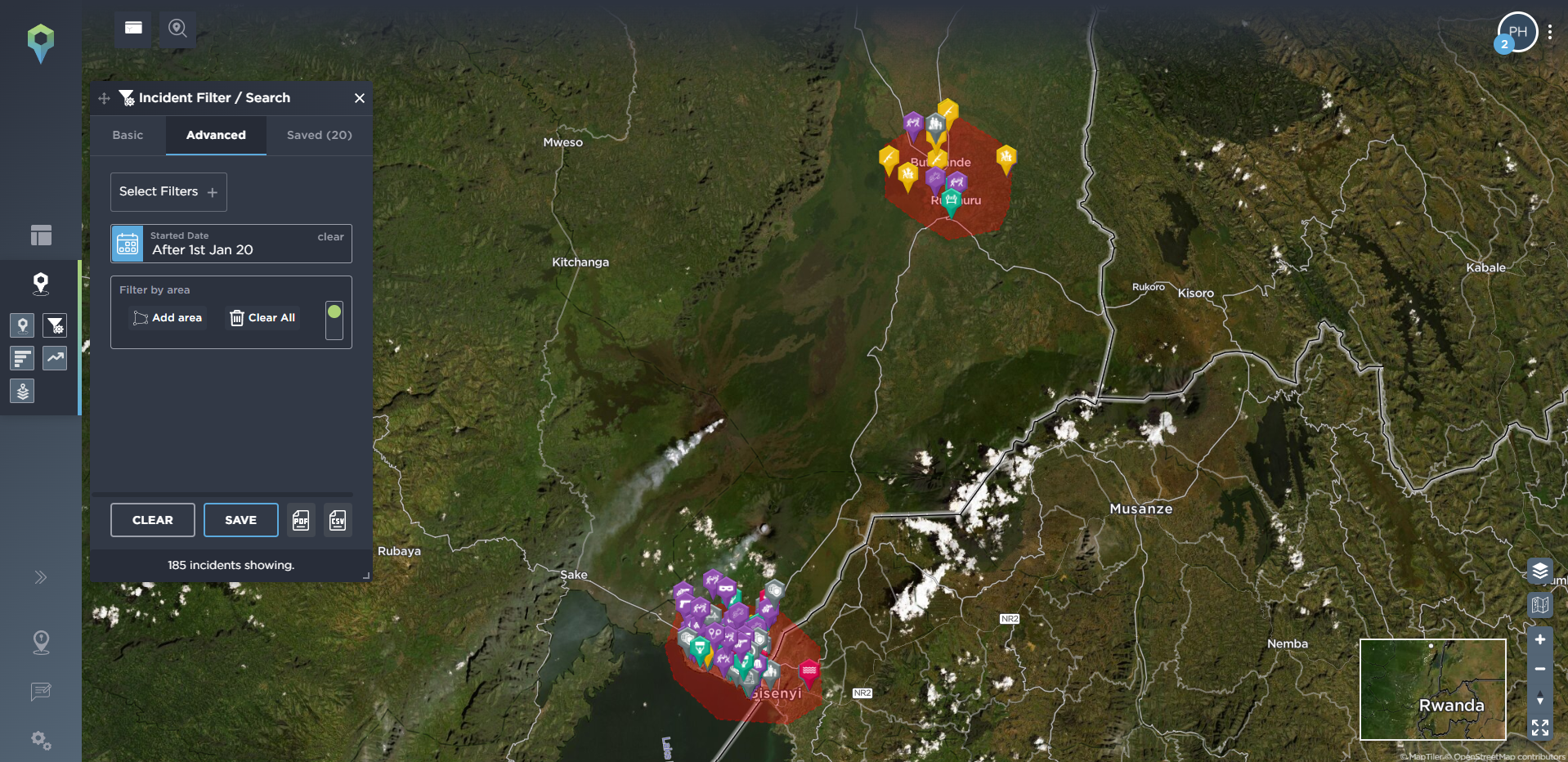
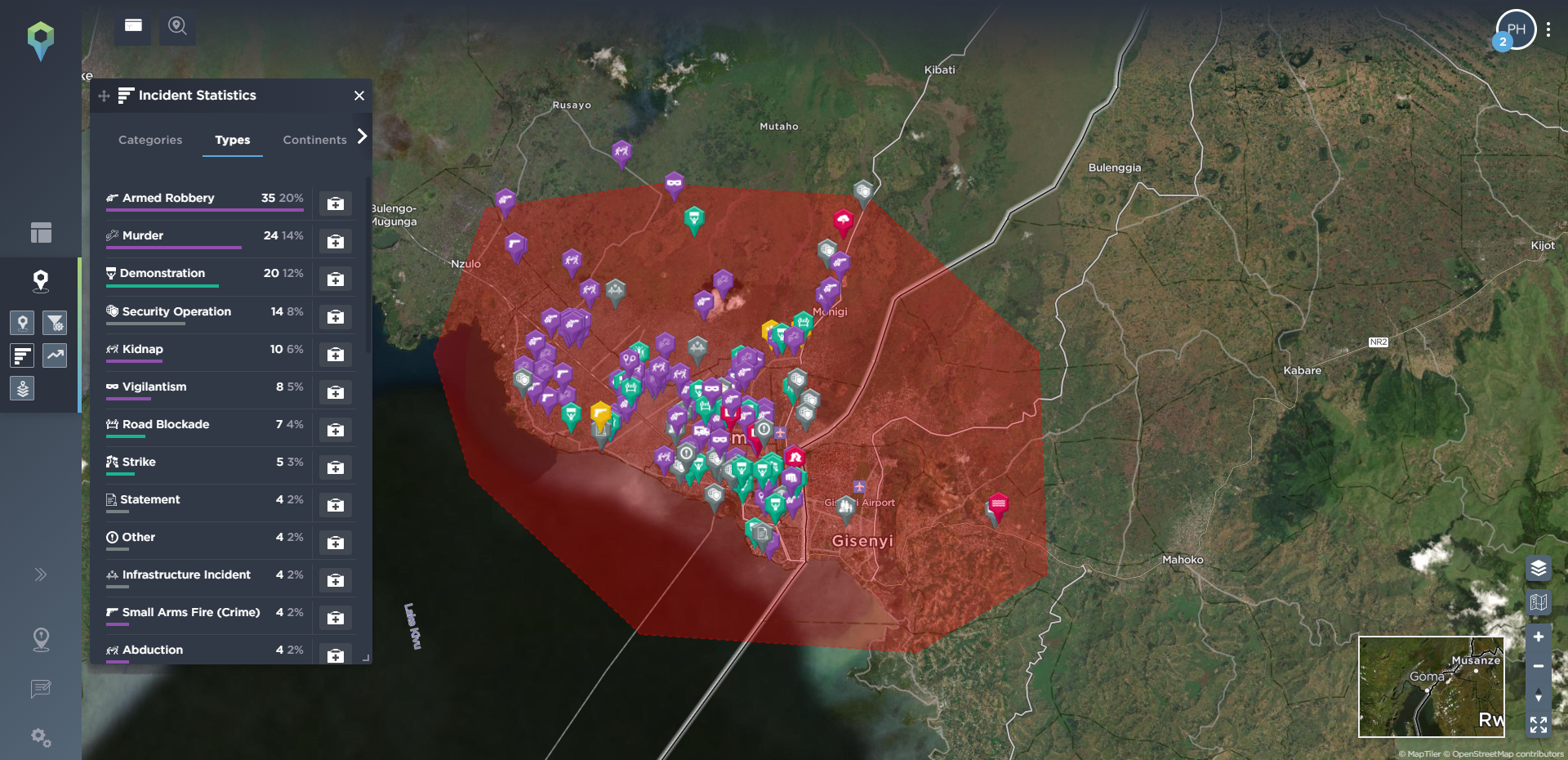
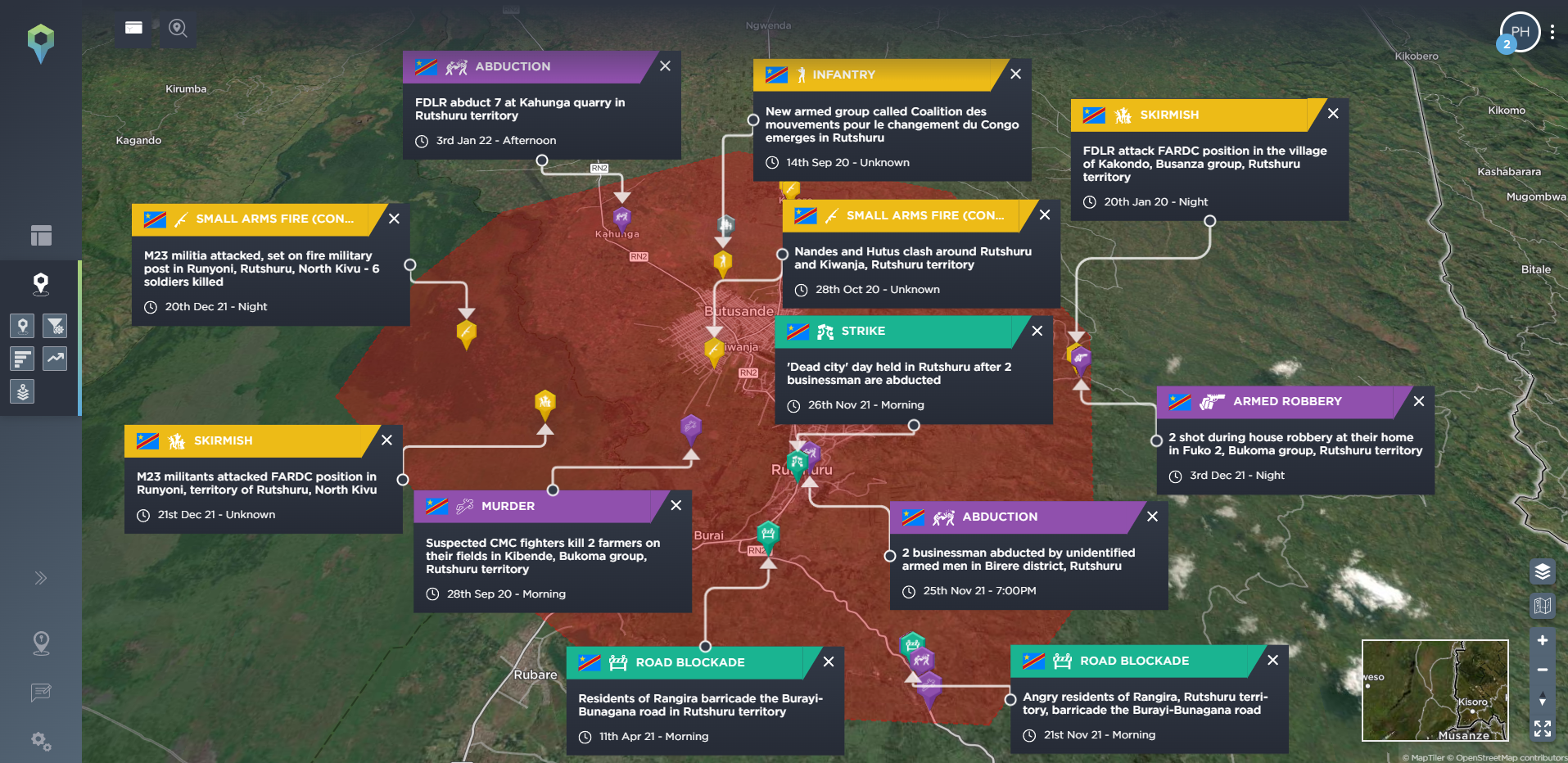
On the other hand, you may be more interested in everything that is happening, and has been happening, in one particular area, in order to see what the most common threats in that area are. Our filtering tools include a draw area tool, allowing you to filter for one particular area of operation, or even following a planned route, so you can see what, historically, have been the most common incidents mapped in that area, and how they’ve developed over time. Below, we’ve filtered for incidents that are particularly relevant for travel security, including ambush, kidnap and abduction, and armed robbery in the area surrounding a proposed route from Goma to Rutshuru in the Democratic Republic of Congo. We’ve then drawn an area around both of these locations so you can see the type of incidents that are prevalent in both destinations.
[image source: Intelligence Fusion; images show the ‘draw area’ tool in action: depicting an area covering a potential route from Goma to Rutshuru filtered for incidents related to route threat security since January 2020; incidents highlighted along the route; areas drawn around both locations; statistics for most common incidents in Goma; incidents highlighted in Rutshuru]
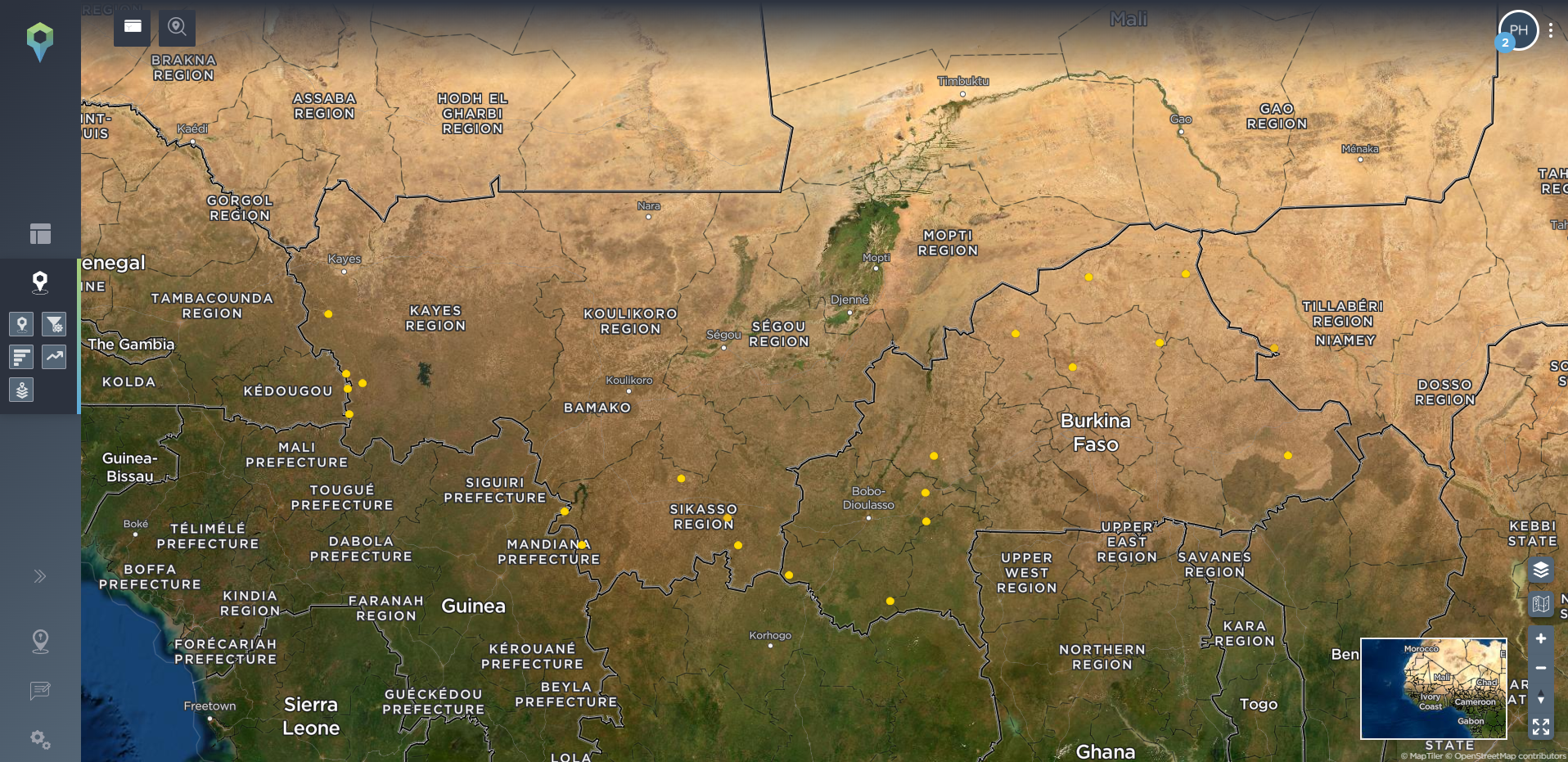
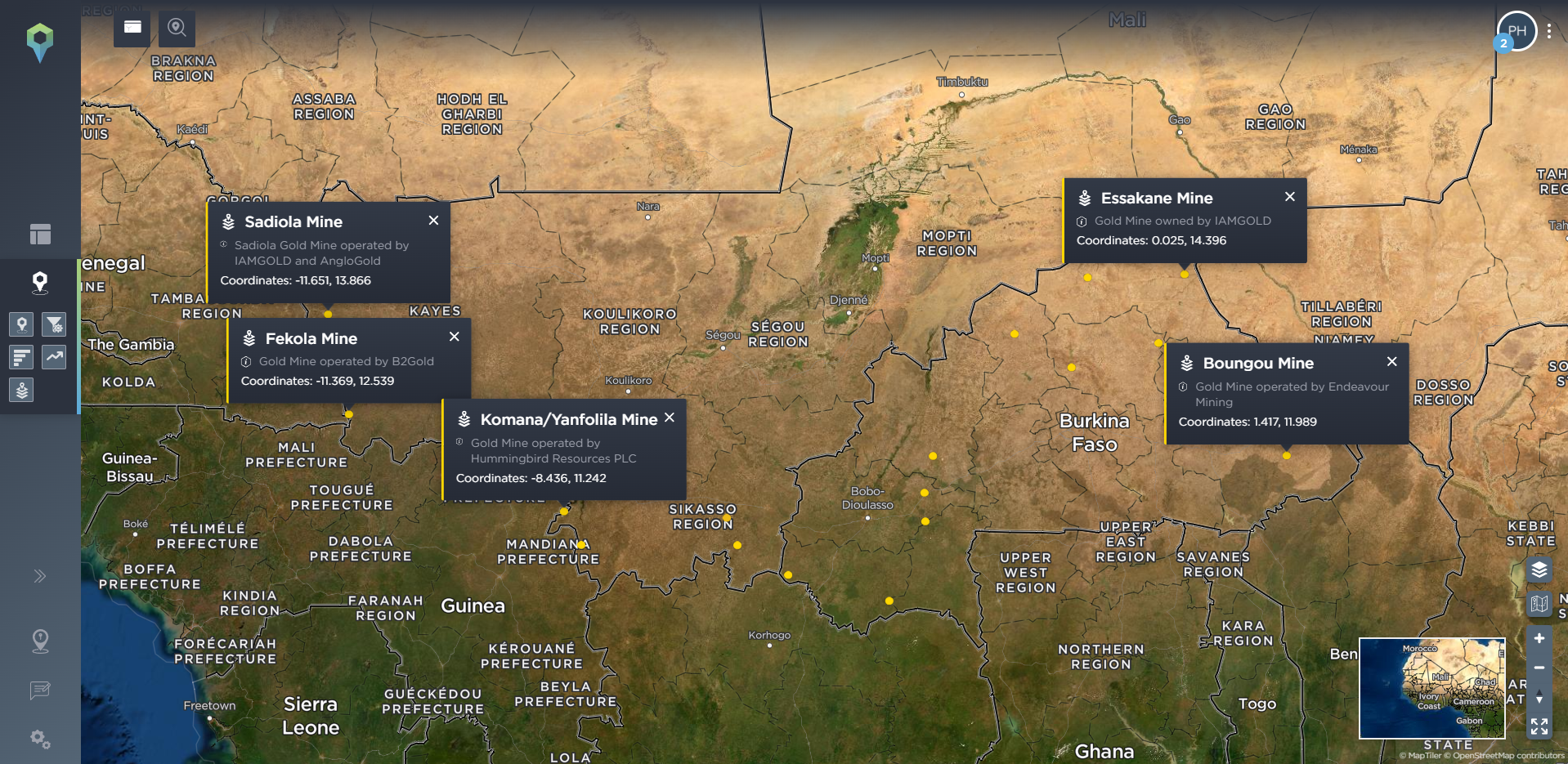
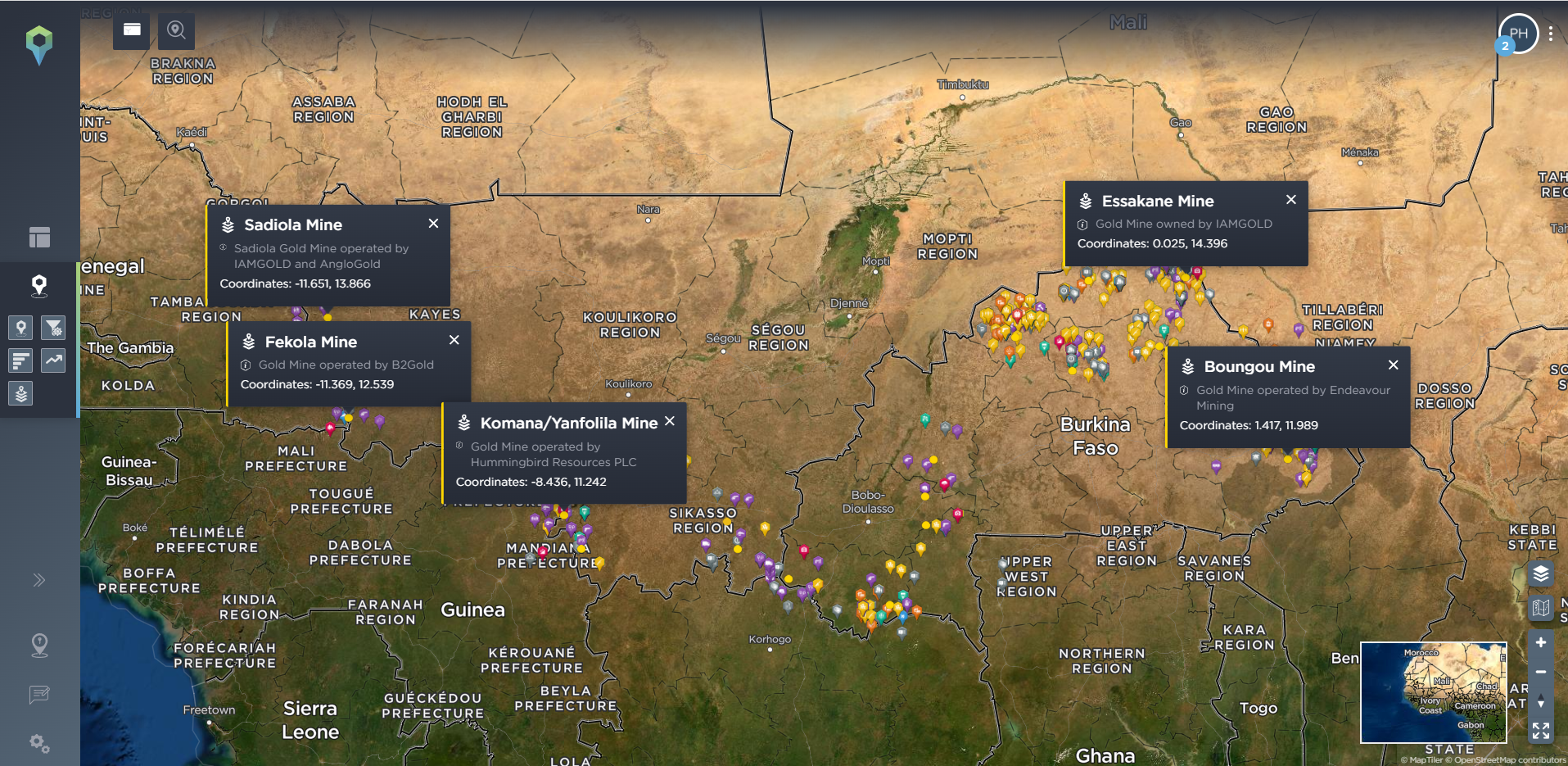
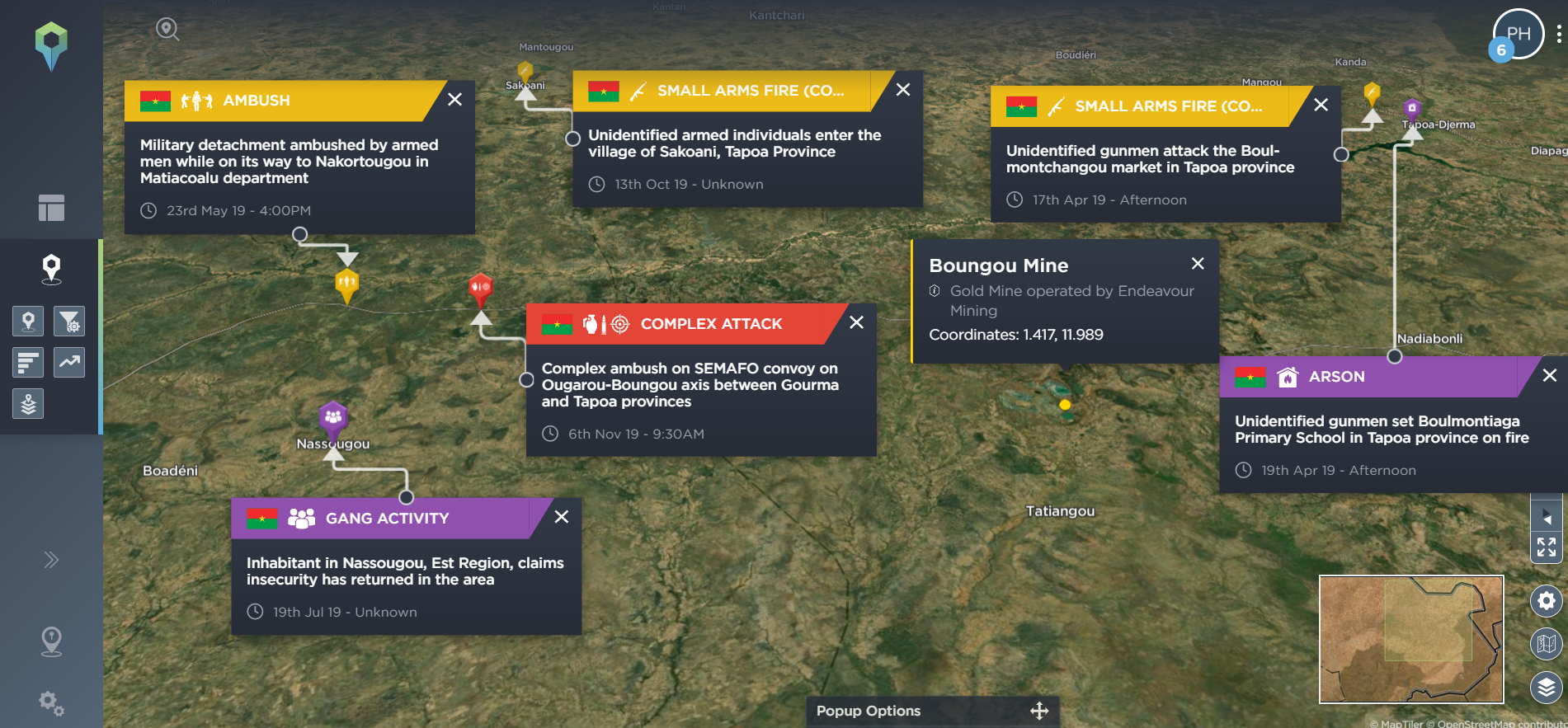
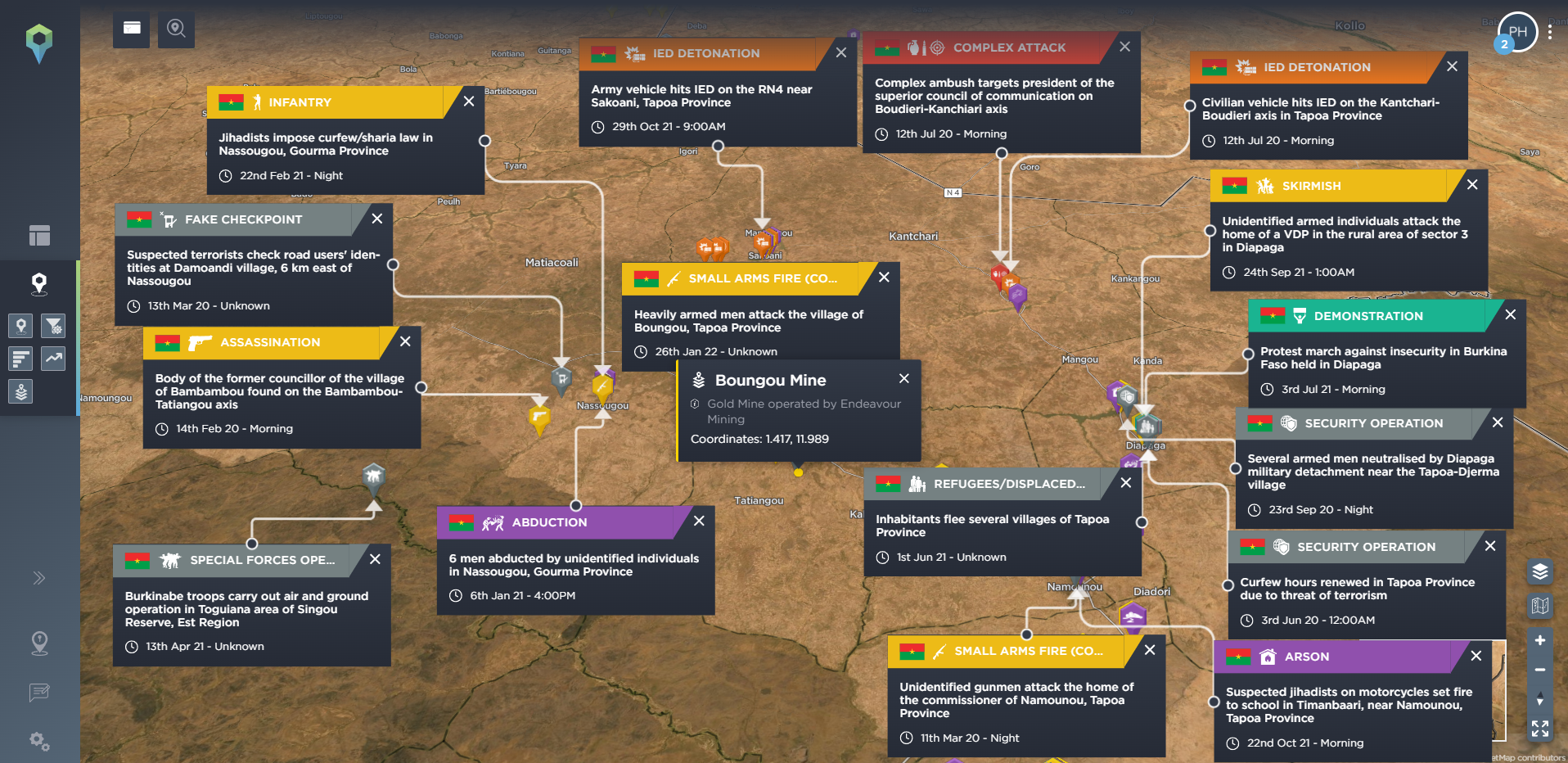
Many companies that are based in conflict zones will have key static assets that are vital for their operations. Taking a mining company as an example, this might be the mining or exploration sites themselves, refining sites, or ports for processing and exporting their mined materials. Our threat intelligence platform allows you to identify these static assets, and set filtering options for incidents that have occured within a certain distance of the site, allowing you to see what has happened, and what is happening nearby to your sites – whether these are your current sites or the location of potential or planned sites. Again, this can also allow you to see how the threat of armed conflict has spread, how close it might be coming to encroaching on or threatening your operations, and what types of incident you should particularly prepare for.
[image source: Intelligence Fusion; images show the ‘static assets’ tool on the Intelligence Fusion platform: significant gold mines in Mali, Burkina Faso and Niger have been identified; then incidents have been filtered for incidents that have been mapped within 50km of these sites; then zoomed in images depict incidents close to the Boungou gold mine in Burkina Faso, leading up to an attack on a convoy of mine workers in November 2019; then filtered for incidents close to the mine that have been mapped since that attack]
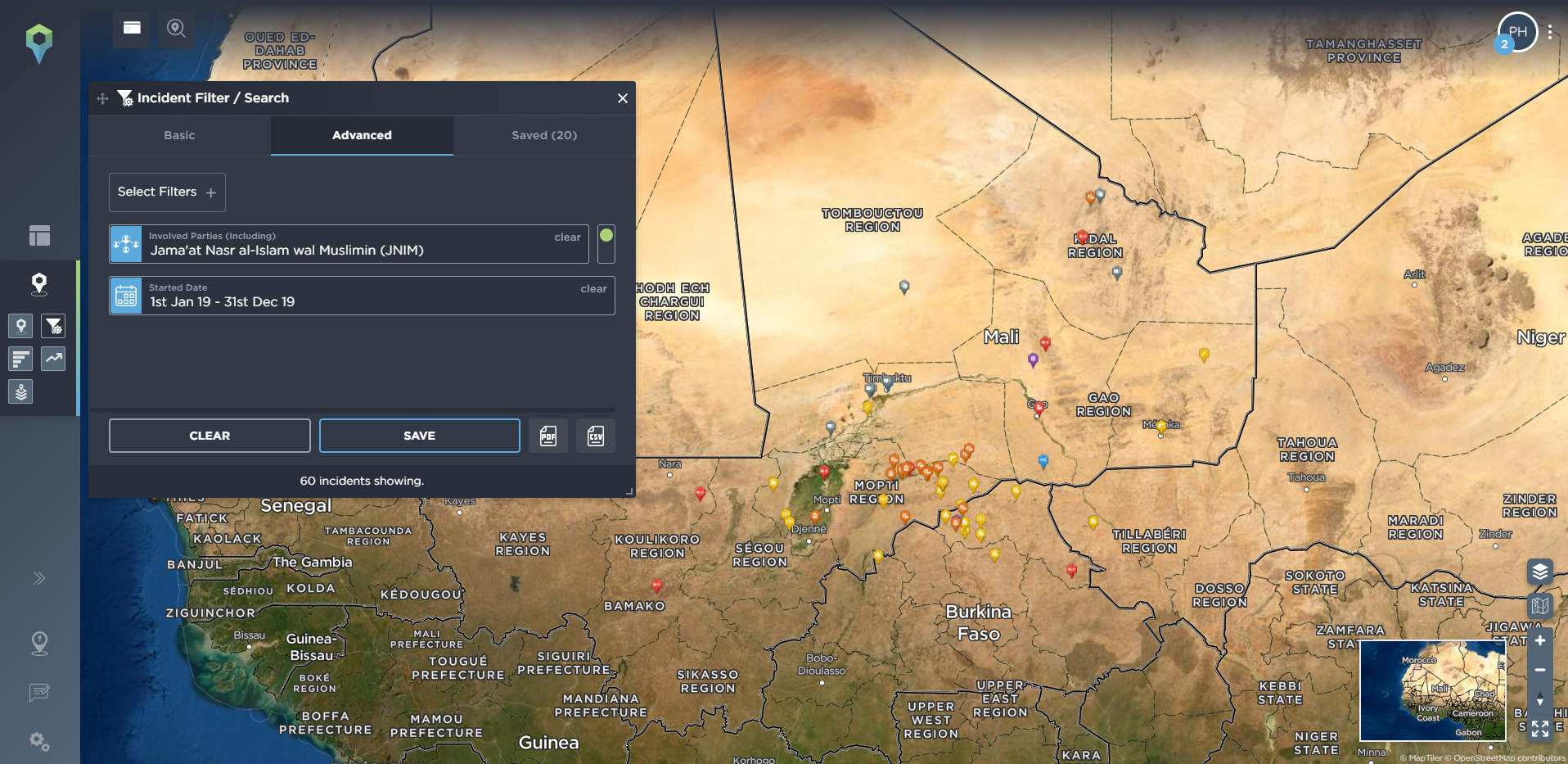
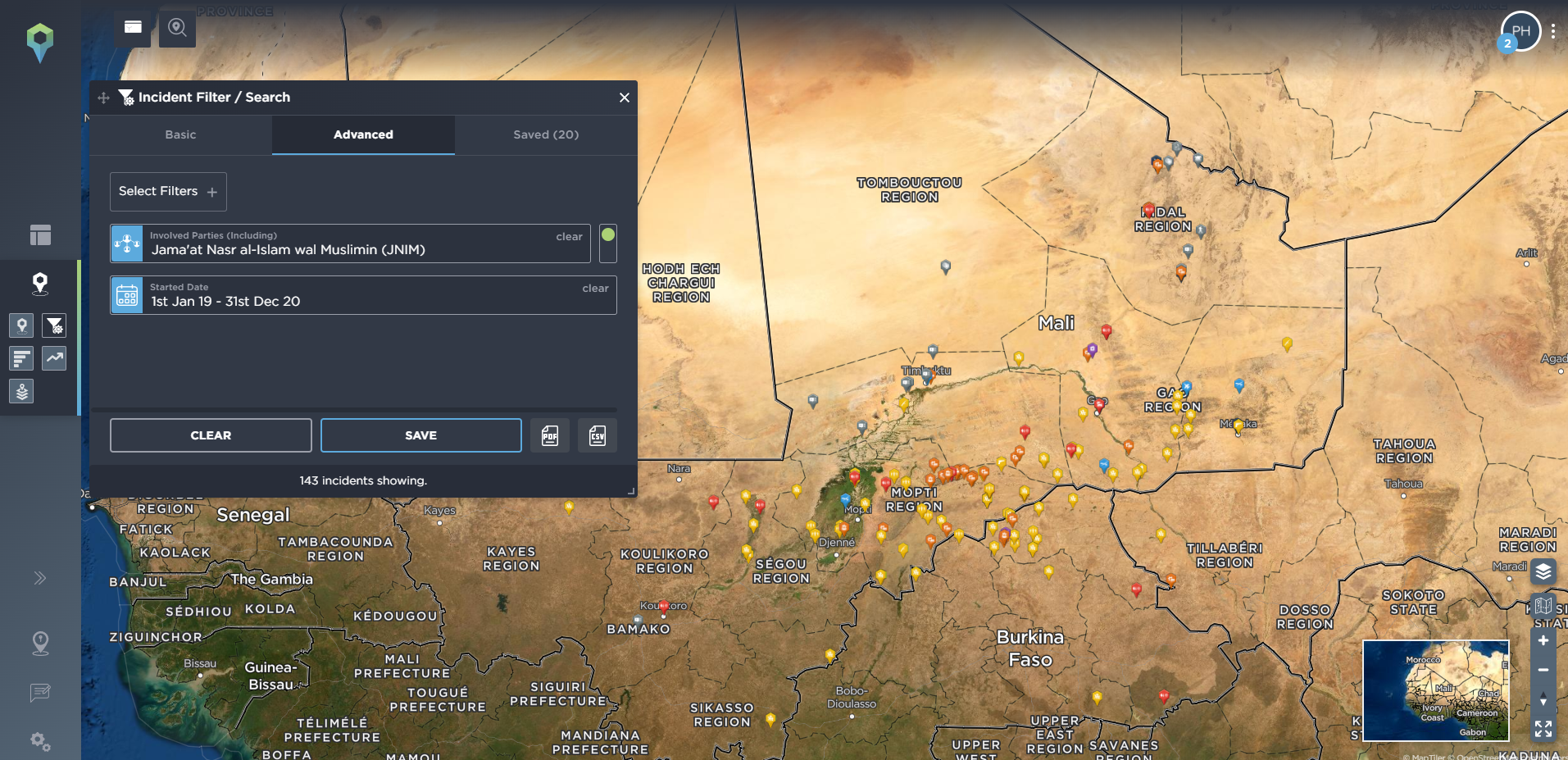
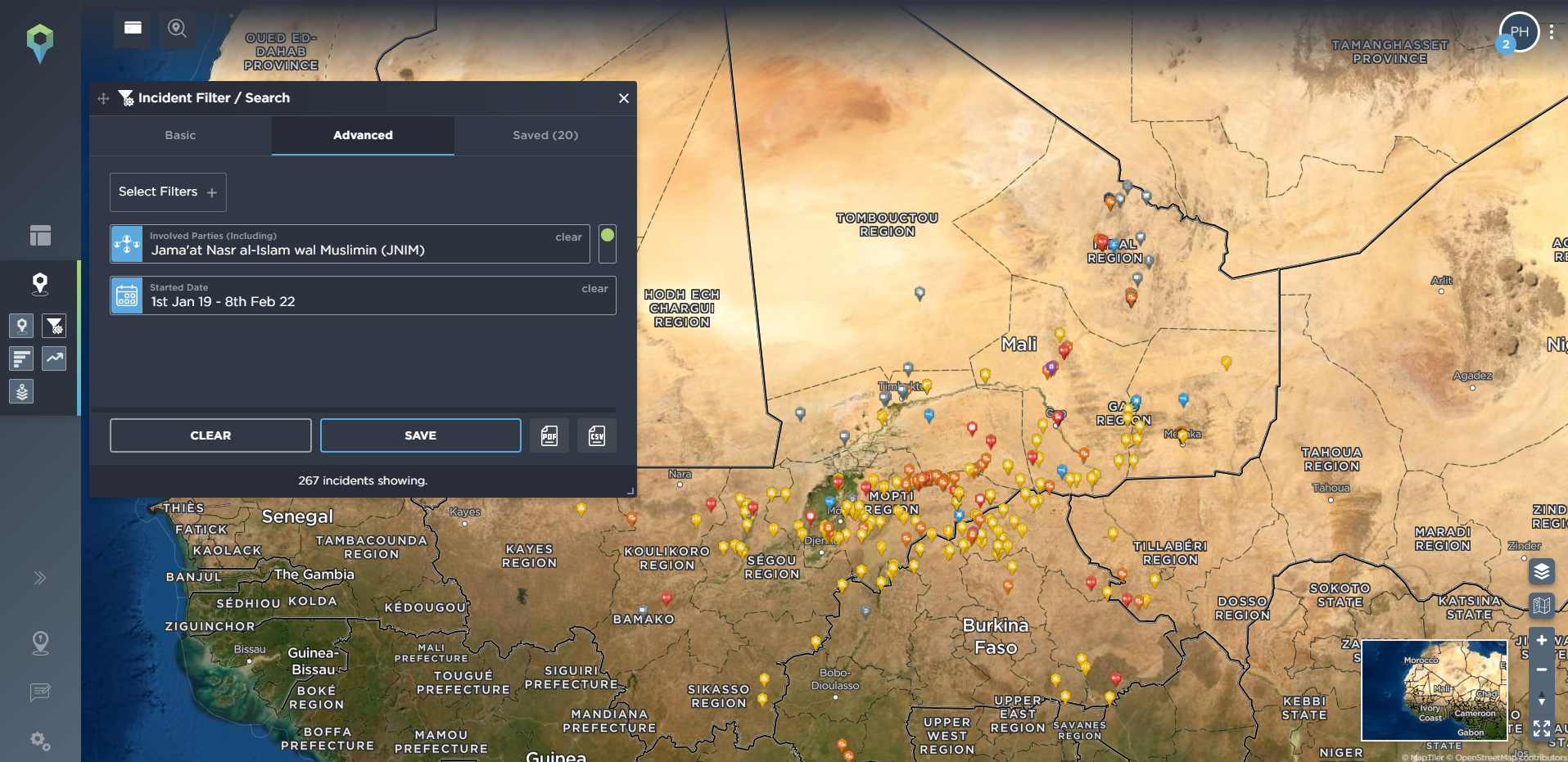
When mapping incidents on our platform we also identify any key actors involved in the incident. This means you can easily filter for any activity from a particular armed group, or groups, when using our threat intelligence software. Going back to West Africa as an example, we’ve filtered for any incidents involving the Islamic insurgent group JNIM, an Al-Qaeda affiliated group that operates in the Sahelian countries of Mali, Niger and Burkina Faso. Filtering by year, we can see how the group has spread its area of activity over time, to now threaten vast parts of the region, including increasingly directly targeting convoys of mining workers.
[image source: Intelligence Fusion; image shows the ‘involved party’ tool on the Intelligence Fusion platform; tracking ‘Jama’at Nasr al-Islam wal Muslimin’ (JNIM) activity and its cumulative spread year-on-year from 2019 onwards]
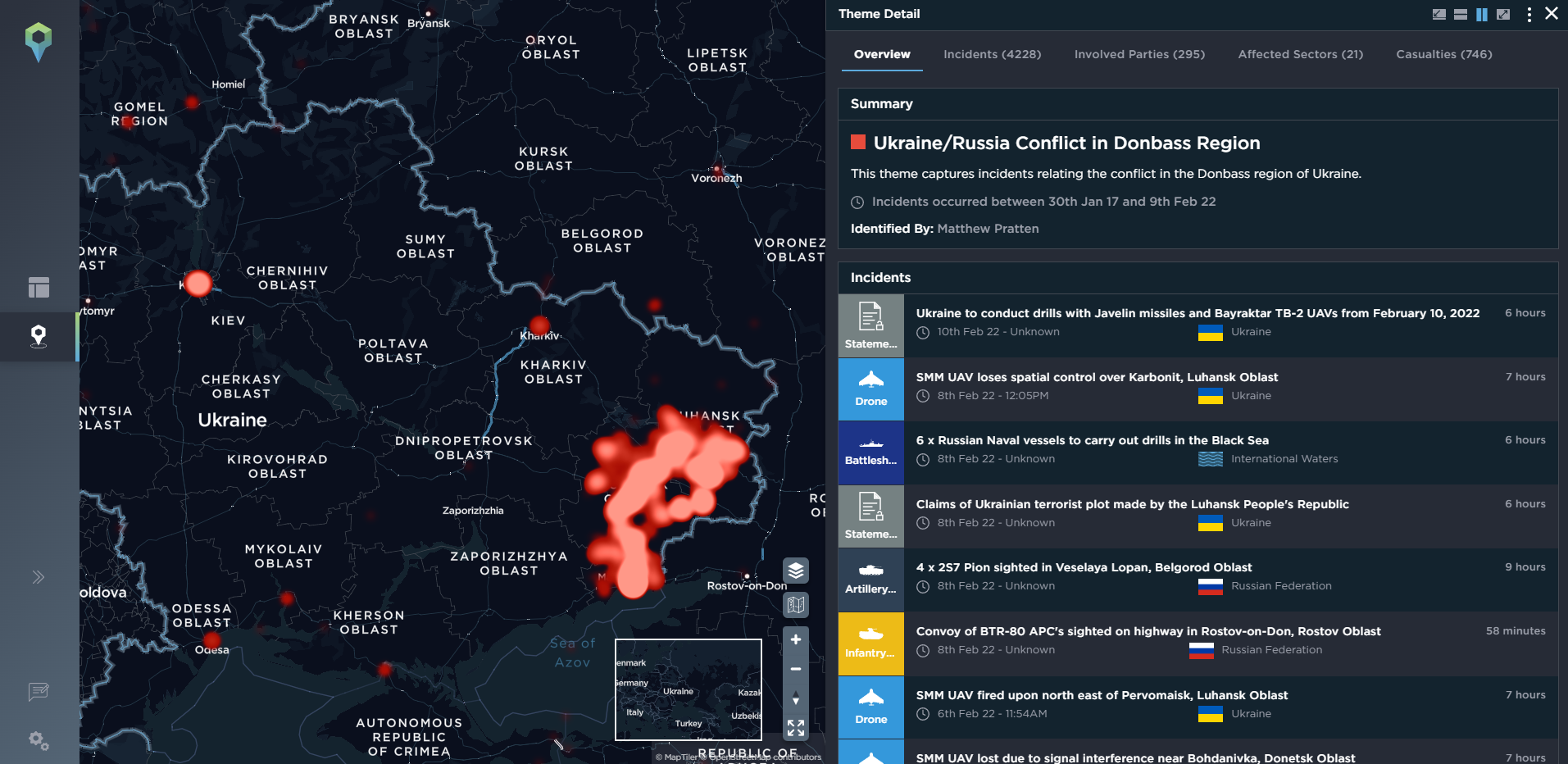
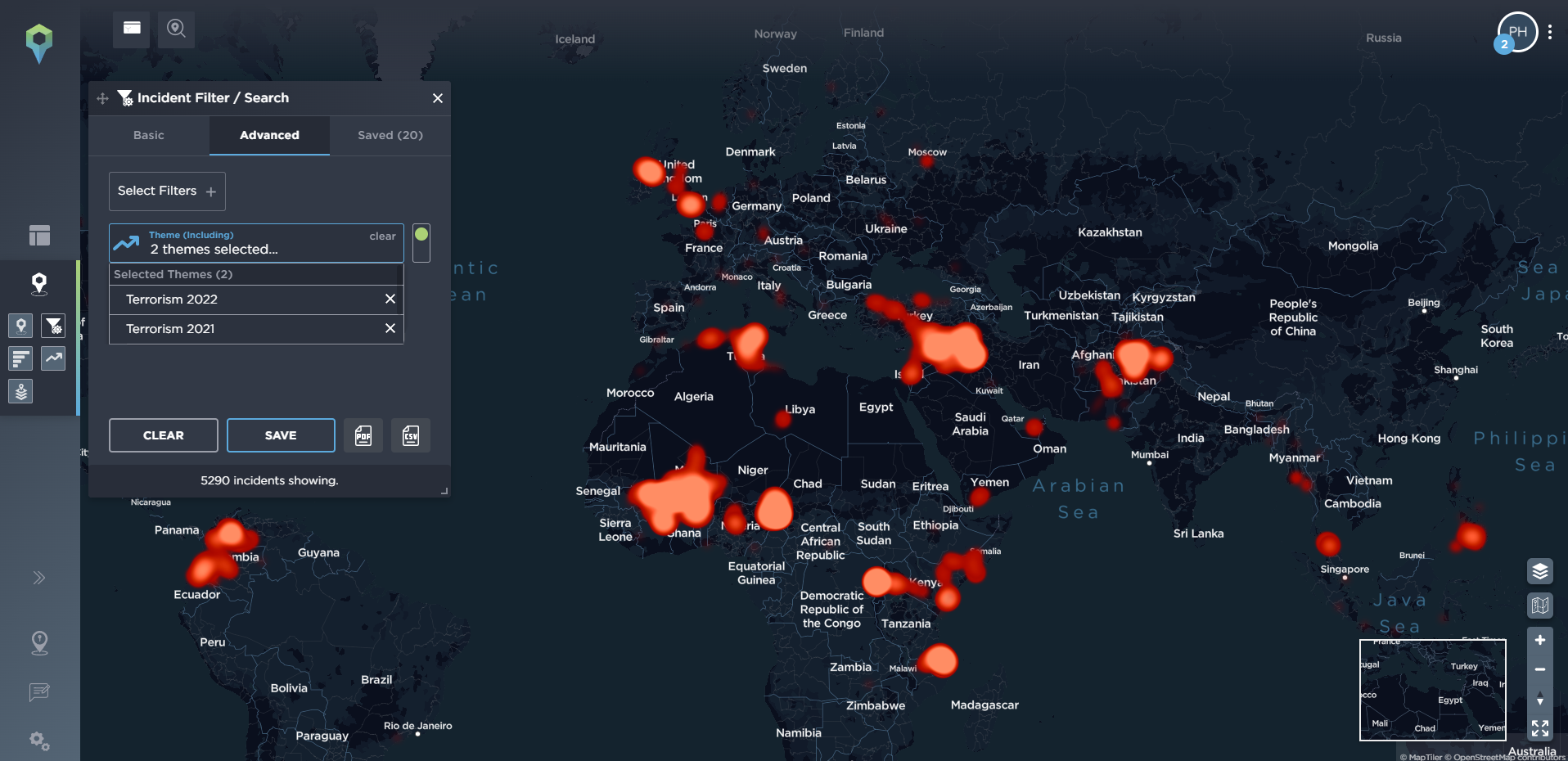
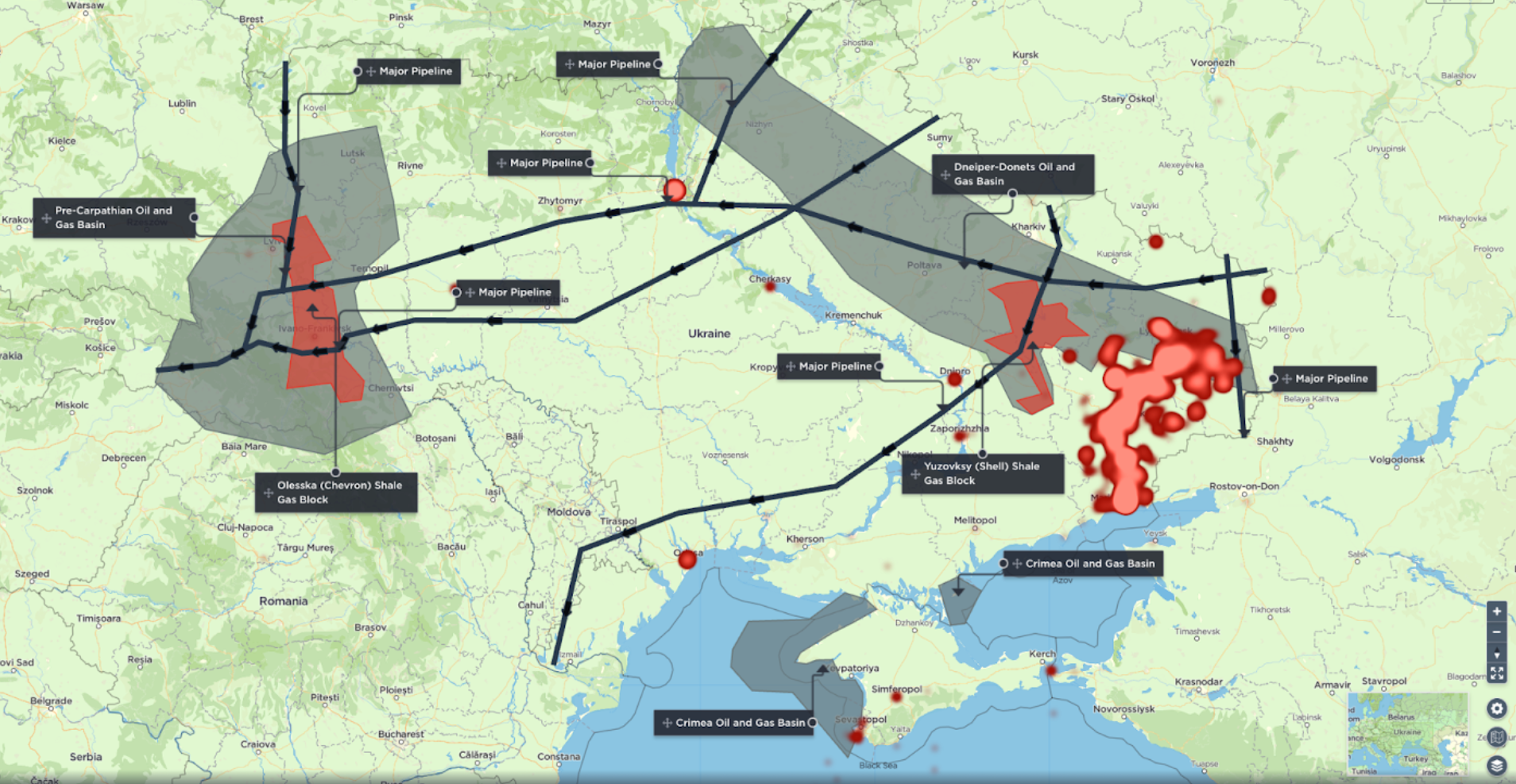
As our platform is populated by intelligence analysts, all of whom have been trained to military-standard methodology, we’re also able to identify particular themes ourselves, often involving ongoing or developing armed conflicts. This makes tracking these conflicts even simpler for our clients, who can then break them down even further by combining the theme with other filtering options. One such theme we’ve identified below is the Donbas conflict in Eastern Ukraine, which also includes tensions between Russia and Ukraine, too. Additionally, we also have themes for tracking Terrorist activity in a particular year or for groups such as Islamic State and its affiliates.
[image source: Intelligence Fusion; images show the ‘themes’ filter on the Intelligence Fusion platform: taking a detailed look at the Russia/Ukraine conflict in the Donbas region; showing the most common areas of terrorist activity across the globe from 2021 onwards using heatmaps from the Terrorism 2021 and 2022 themes]
So threat intelligence software can clearly allow you to track and identify patterns of intelligence related to armed conflict by digging through and combining historical data – but it can also alert you to any breaking developments, too. Any combination of filters our clients have put together can be saved and followed – with clients able to opt in to alerts notifying them when a new incident matching their filter is identified, or if a particular incident that they have opted to follow has been updated with new developments or information. We are also in the process of rolling out a new feature called Active Alerts that lets fellow colleagues who may not necessarily have a subscription to our platform still follow and receive alerts for any new incidents that are key to their security planning.
And it isn’t just business operations that benefit from threat intelligence software. As established earlier, threat intelligence is a military principle, and we have several clients in the military sphere who are able to use our threat intelligence platform to track and monitor armed conflicts in different regions in the world, prepare the battlespace and use it as a central hub for intelligence sharing, avoiding the duplication of effort and data that can occur within military intelligence programmes.
Intelligence Fusion's threat intelligence platform allows you to upload, share and access documents such as threat assessments with your whole team in one location [image source: Intelligence Fusion]
What are the causes of violent conflict?
So given the high level of risk that armed conflict presents businesses operating in conflict zones, how can businesses prepare for potential conflict in areas not currently seeing open and sustained violence? And can they identify potential factors that might lead to or cause conflict in their areas of operation?
This first requires being able to identify what drives conflict in the first place. The triangle theory put forward by Norwegian sociologist and founder of the Peace Research Institute, Johan Galtung, reduces conflict and violence to their most basic terms. For conflict, this comes down to the ABC or Attitude-Behaviour-Contradiction ‘conflict triangle’ – with conflict arising from the interplay of these three elements: Contradiction being the issue or resource over which there is an incompatible disagreement; the Attitude of the different parties towards the disagreement; and the Behaviour that arises from this. Galtung also has a similar model for violence, the DSC or Direct-Structural-Cultural ‘violence triangle’, with the Direct violence that we see arising from the Structural – for example inequality, exploitation or repression – and Cultural – for example cultural beliefs that certain ethnic groups, religions or nationalities are inherently superior/inferior, or a historic threat or enemy – violence that is often hidden beneath the surface. The two models are interlinked as shown below.
[image source: Understand to Prevent: The military contribution to the prevention of violent conflict, MCDC November 2014]
Essentially this means that certain conditions exist that, when combined, make the outbreak of violent, armed conflict much more likely. These conditions can therefore be monitored and tracked just like armed conflict itself. These could include, for instance, scarcity of resources such as potable water supplies, or pastures suitable for grazing livestock; poor economic and social conditions; or repressive political systems – all of which could fall under the Contradiction or Structural elements of the conflict and violence triangles.
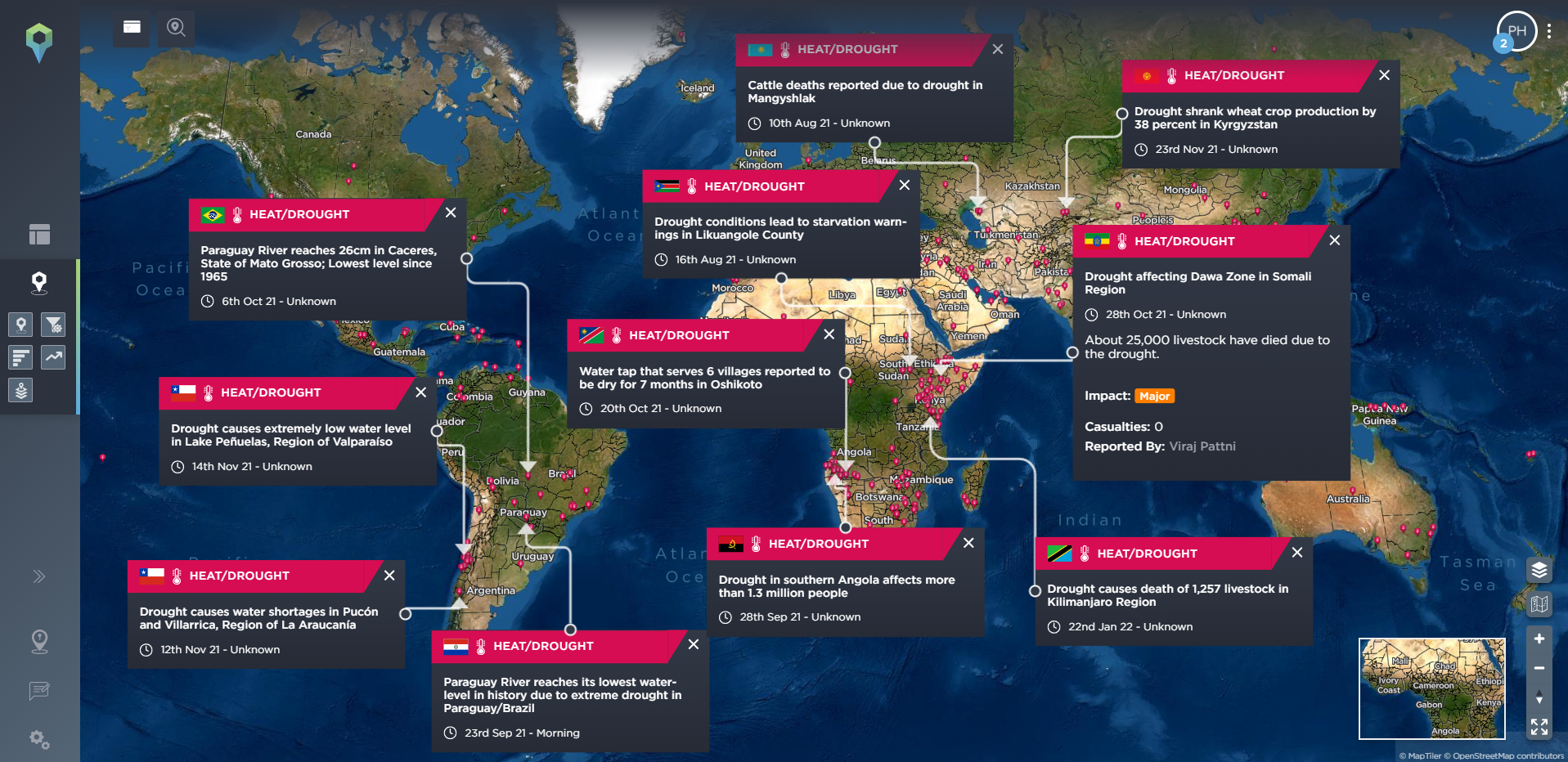
Droughts and water shortages could potentially lead to instability and conflict in the future [image source: Intelligence Fusion]
Building resentment, dissatisfaction or mobilisation in response to these conditions (as depicted below) are another sign of potential conflict – these might manifest themselves in protest movements, rioting, or clashes with either security forces or rival groups. And then, of course, there are smaller scale Direct violence incidents such as attacks, bombings or assassinations, that could be the precursor to large scale armed conflict
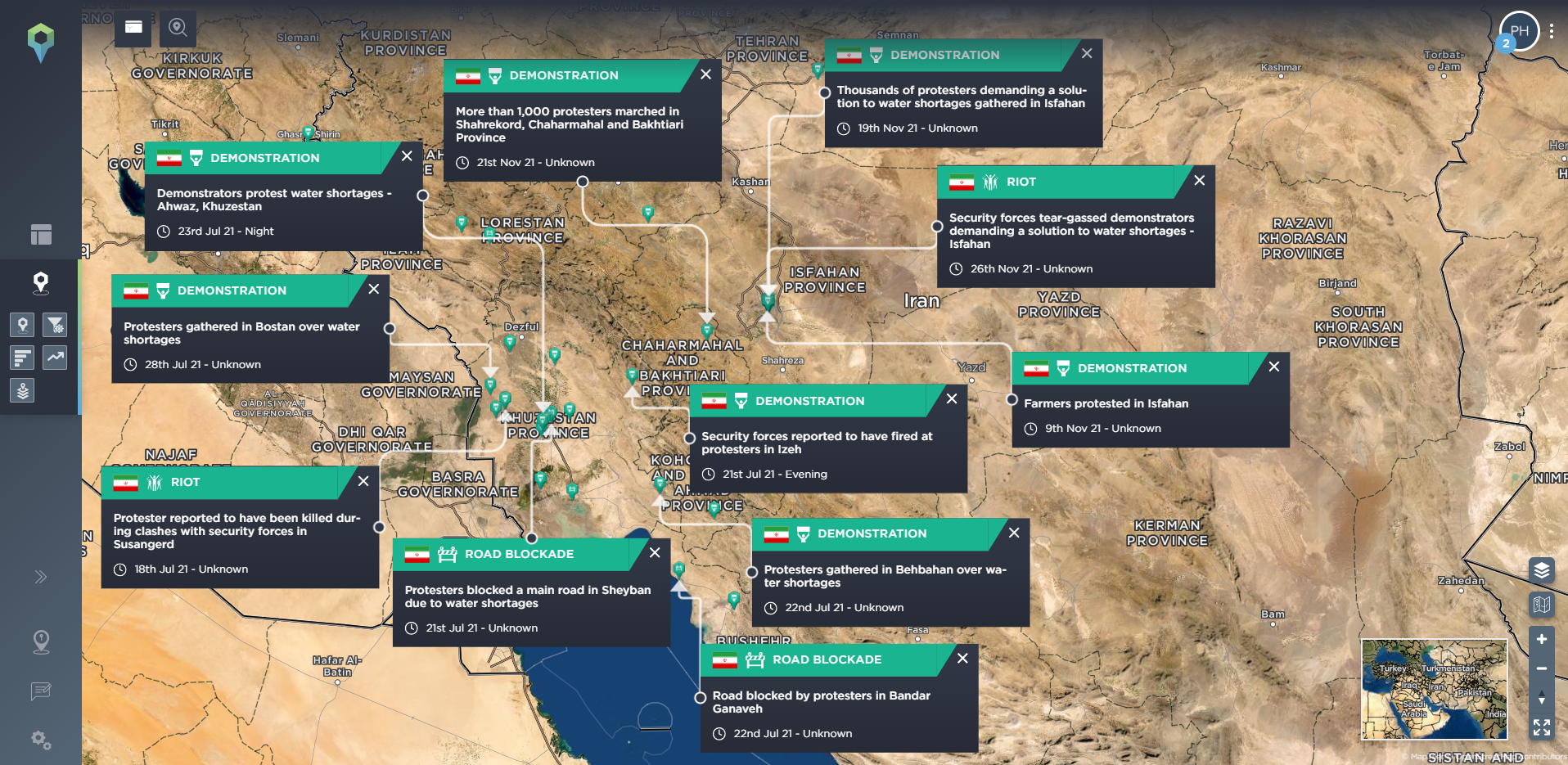
Water shortages are a frequent cause of protest in Iran [image source: Intelligence Fusion]
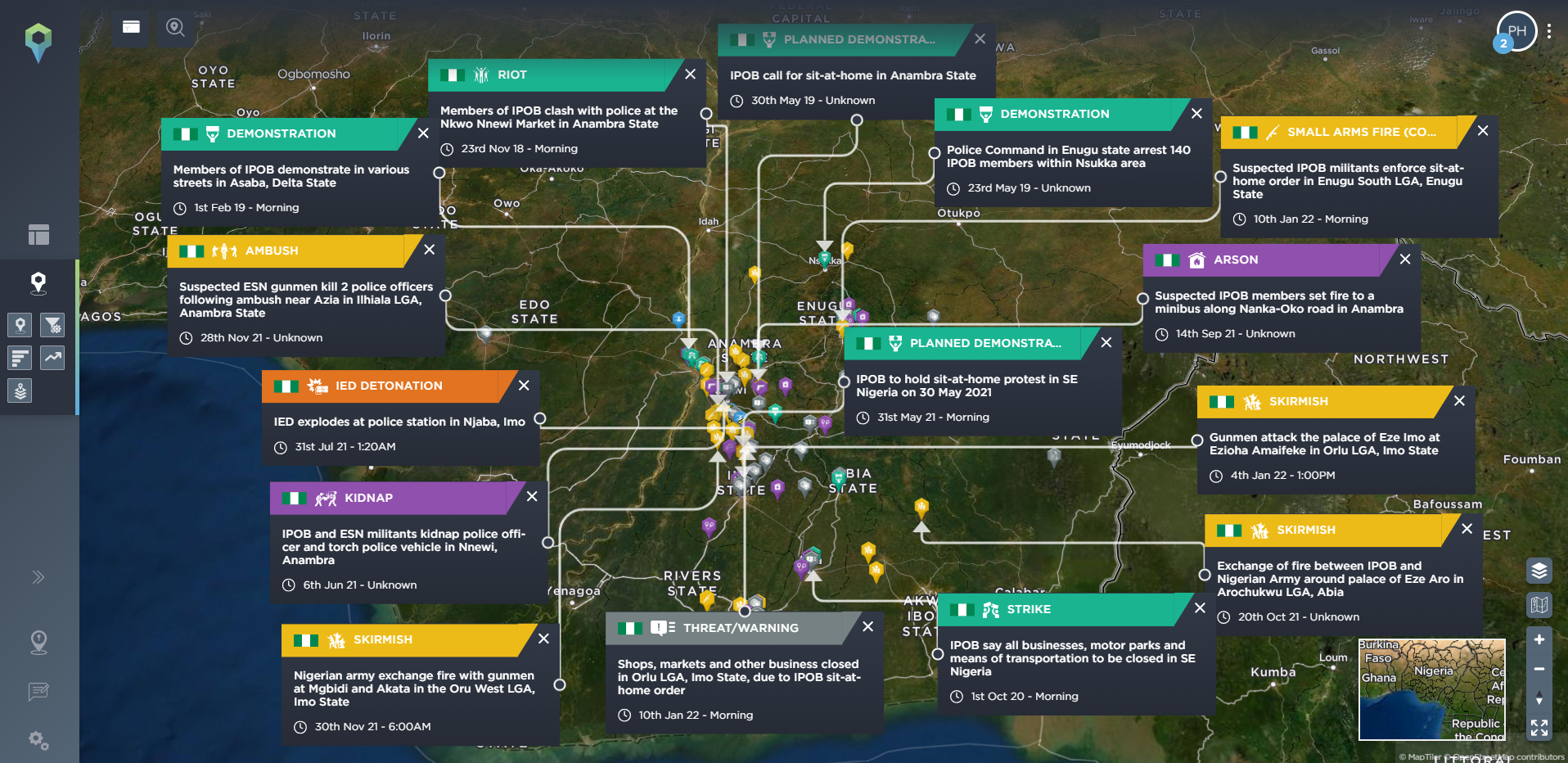
Ethnic tensions are a frequent cause of conflict. Image depicts protests carried out by the Indigenous Peoples of Biafra (IPOB) in South East Nigeria, followed by violent clashes, arson, bombings, assassinations and eventually armed conflict with security forces [image source: Intelligence Fusion]
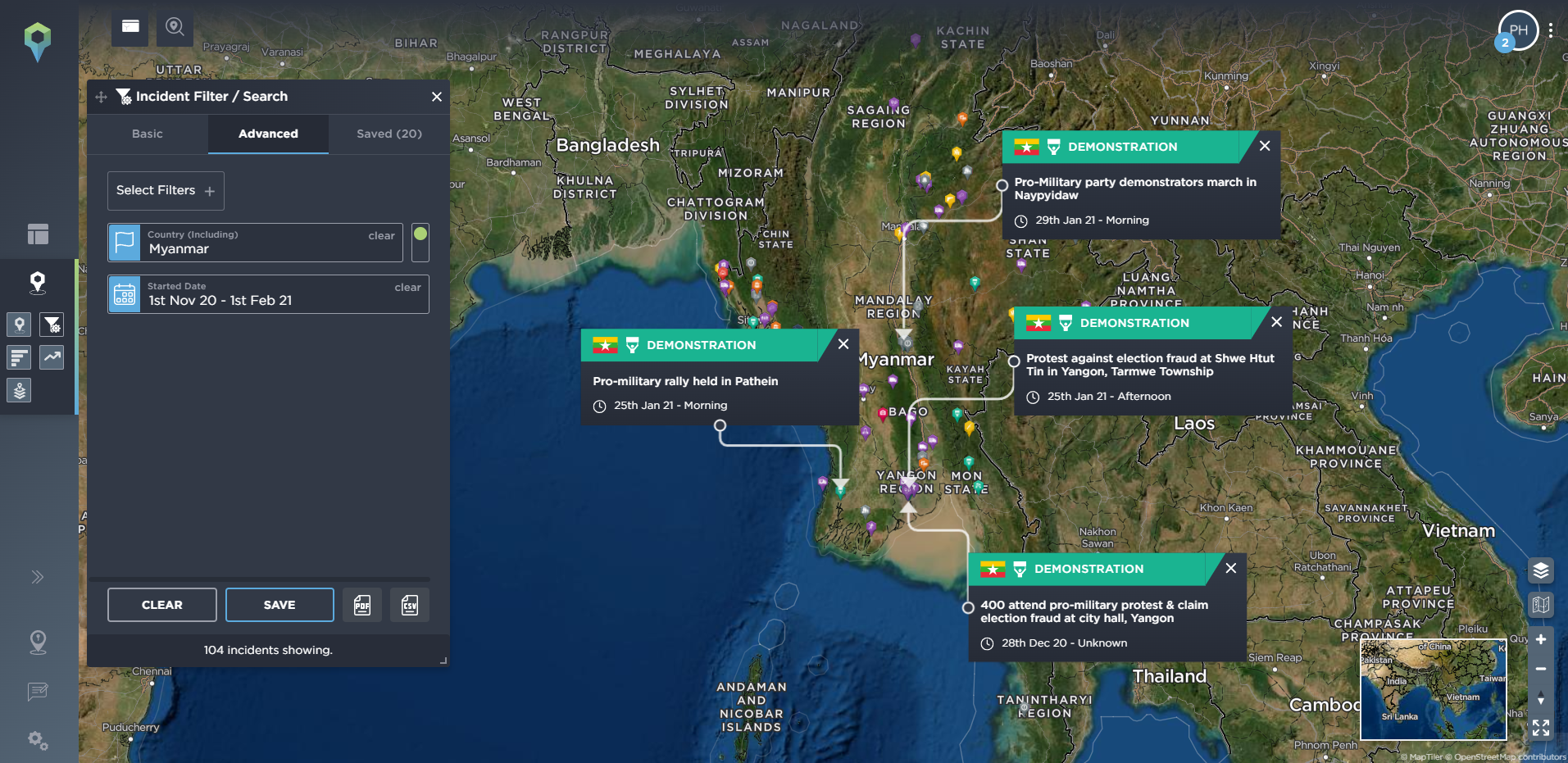
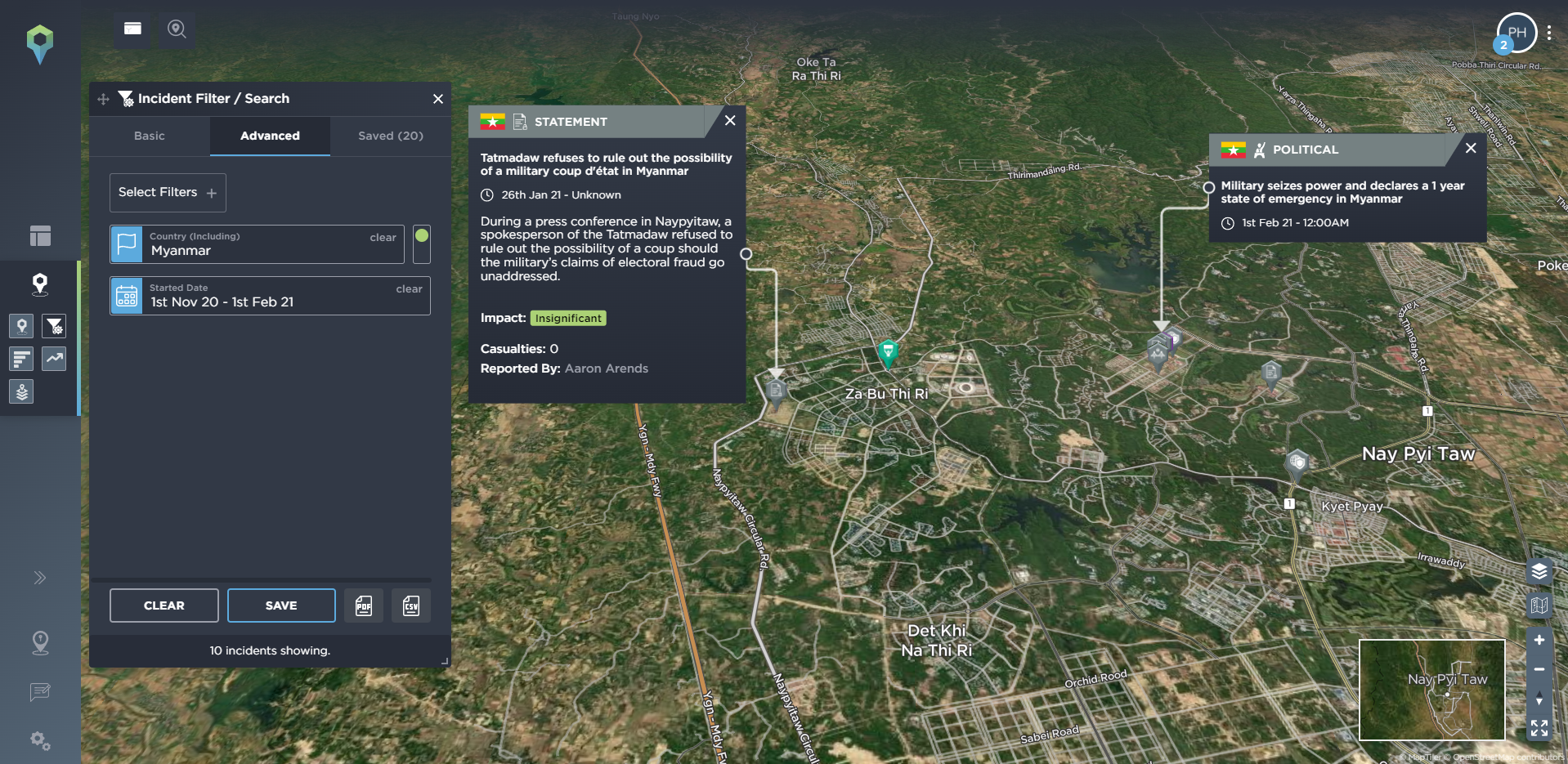
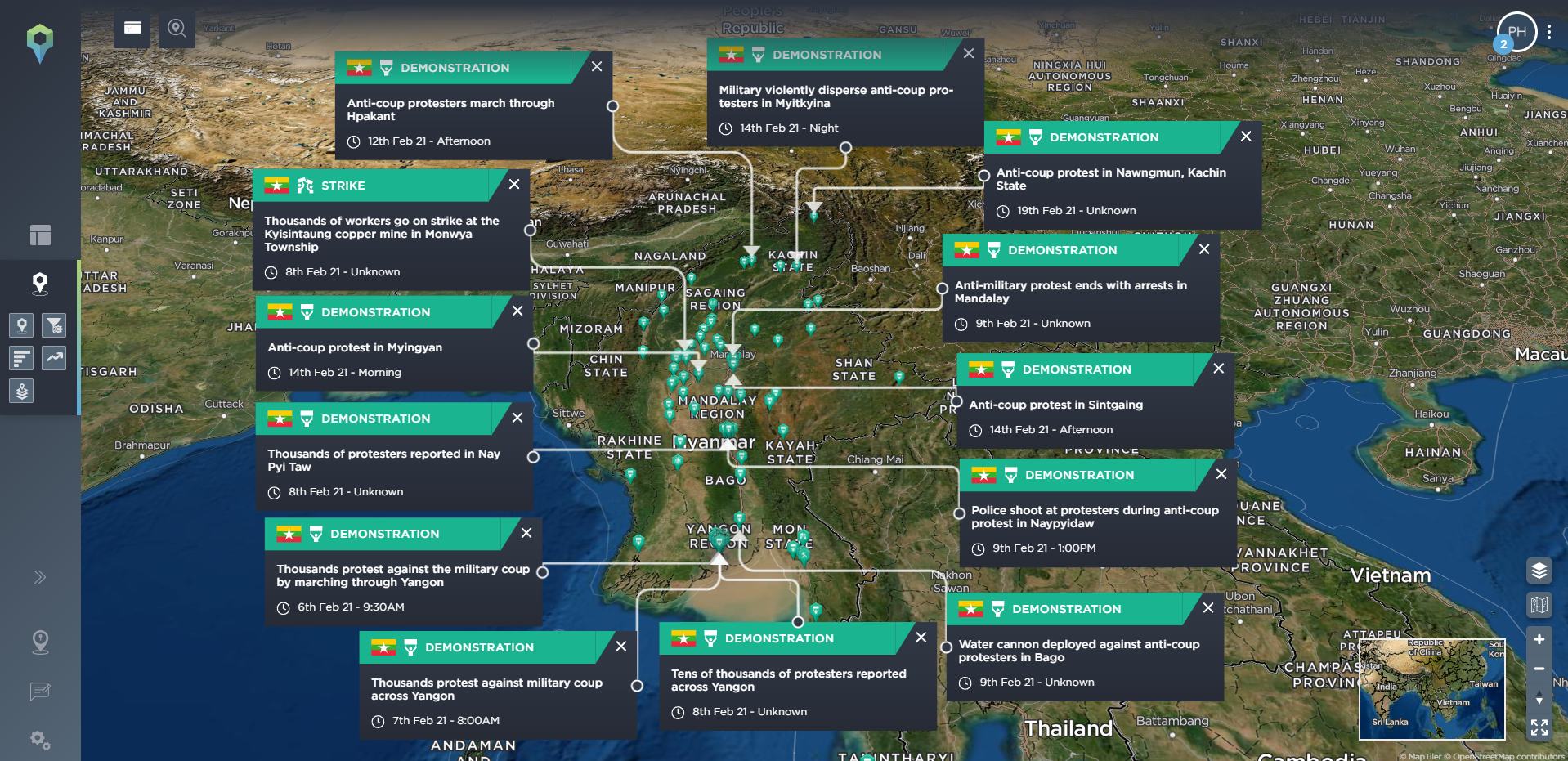
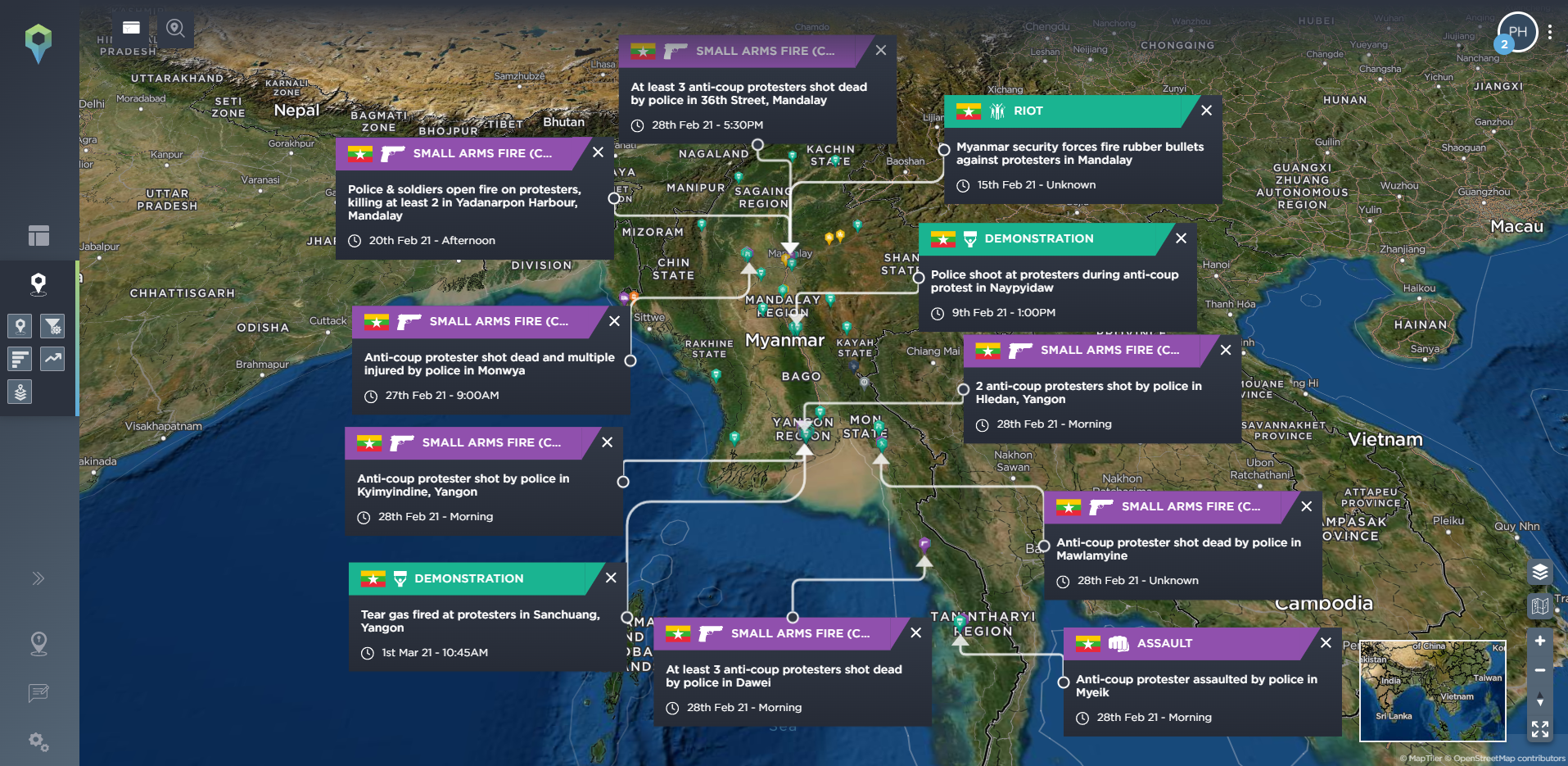
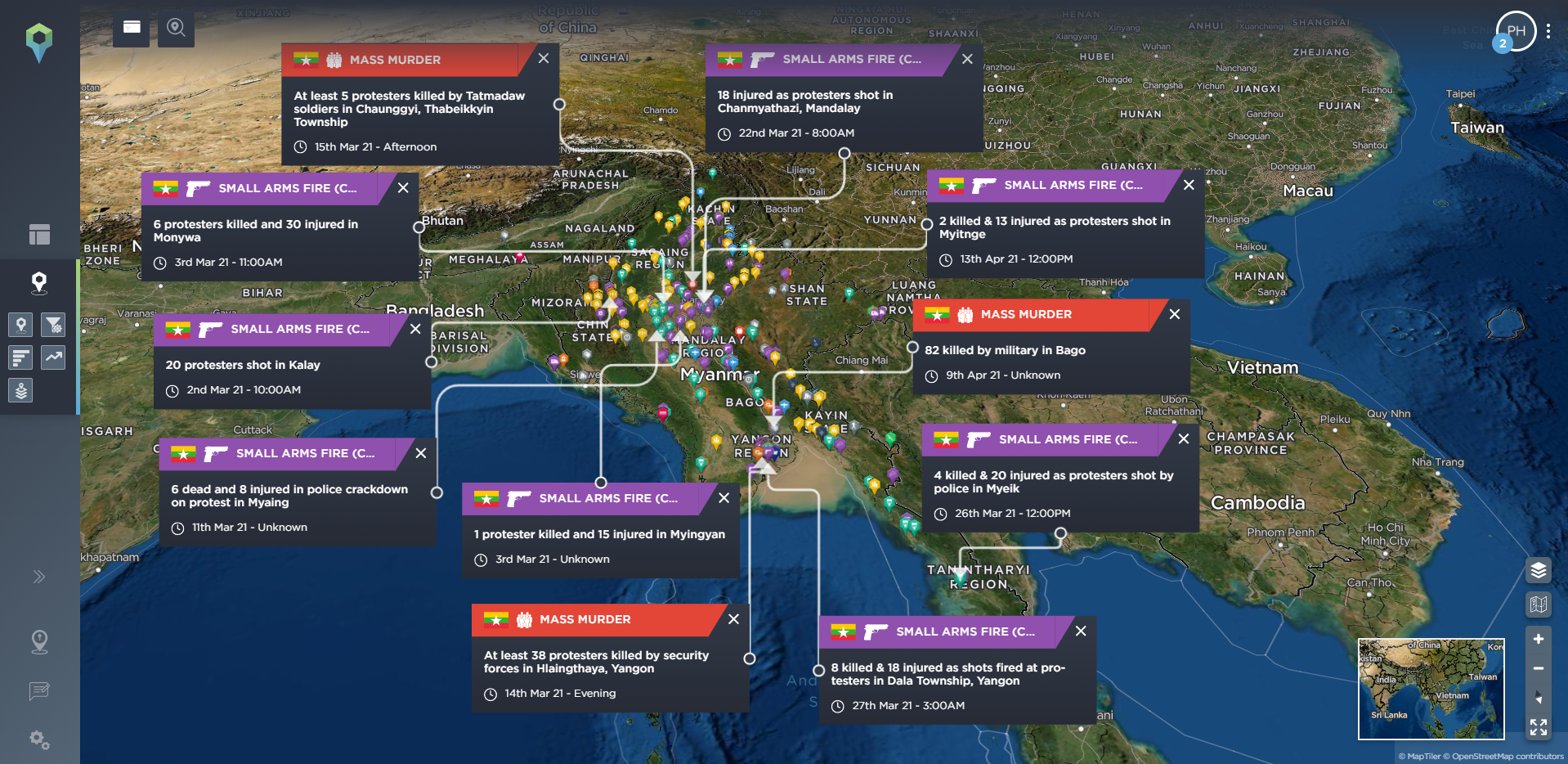
All of these are incidents that can be mapped and monitored on our threat intelligence software, with our platform tracking almost 160 different incident types across 11 different categories. These include tracking political incidents or threats and warnings issued by different groups, hazards including reports of drought, or protest-related incidents including riots, road blockades, or rock-throwing. Let’s take a look at Myanmar as an example to see how these elements can build towards wider armed conflict.
[image source: Intelligence Fusion; images show the development of the armed conflict in Myanmar; from claims of electoral fraud by the pro-military party; the Myanmar coup led by the Tatmadaw military; the outbreak of anti-coup protests; the increasingly violent crackdown by the Tatmadaw; the developing armed resistance movement and insurgency involving People’s Defence Forces; and the open armed conflict and state of civil war within the country. Existing ethnic armed groups were already in conflict with the Myanmar military before the coup took place, making the armed conflict even more complex.]
By keeping an eye on these conditions, then, organisations can not only track armed conflict itself, but use threat intelligence to track the potential for conflict in areas that aren’t currently active conflict zones – for example in places that have been the site of previous or dormant conflicts – and better prepare their security teams for possible worst-case scenarios.
Moreover, by tracking these key sources of tension, businesses can also make sure that their actions do not exacerbate these tensions and cause conflict to escalate. Instead, by taking careful action to address these tensions, businesses can in fact play an important role in providing peace and stability in areas of tension and conflict, by helping to mitigate a lack of economic opportunities and high unemployment that can both be key sources of fragility that can lead to violent conflict.
Last year, Intelligence Fusion’s threat intelligence solutions helped our clients – many of whom are active in areas of high conflict – keep more than 200,000 people safe across a wide range of industries. To take a closer look at the features we’ve highlighted in this report, and to see how we can work to help your organisation, talk to a member of our team today – we’d be more than happy to provide you with a demo of our software.