The Rise of Nation State Cyber Attacks and the Threat to Business
How have nation state cyber attacks started to impact the world of business? A Q&A with cyber security expert Robert Hayes
Cyber attacks are quickly becoming one of the key operational risks that a business needs to plan for, with companies of all sizes now seemingly vulnerable to being targeted by cyber criminals.
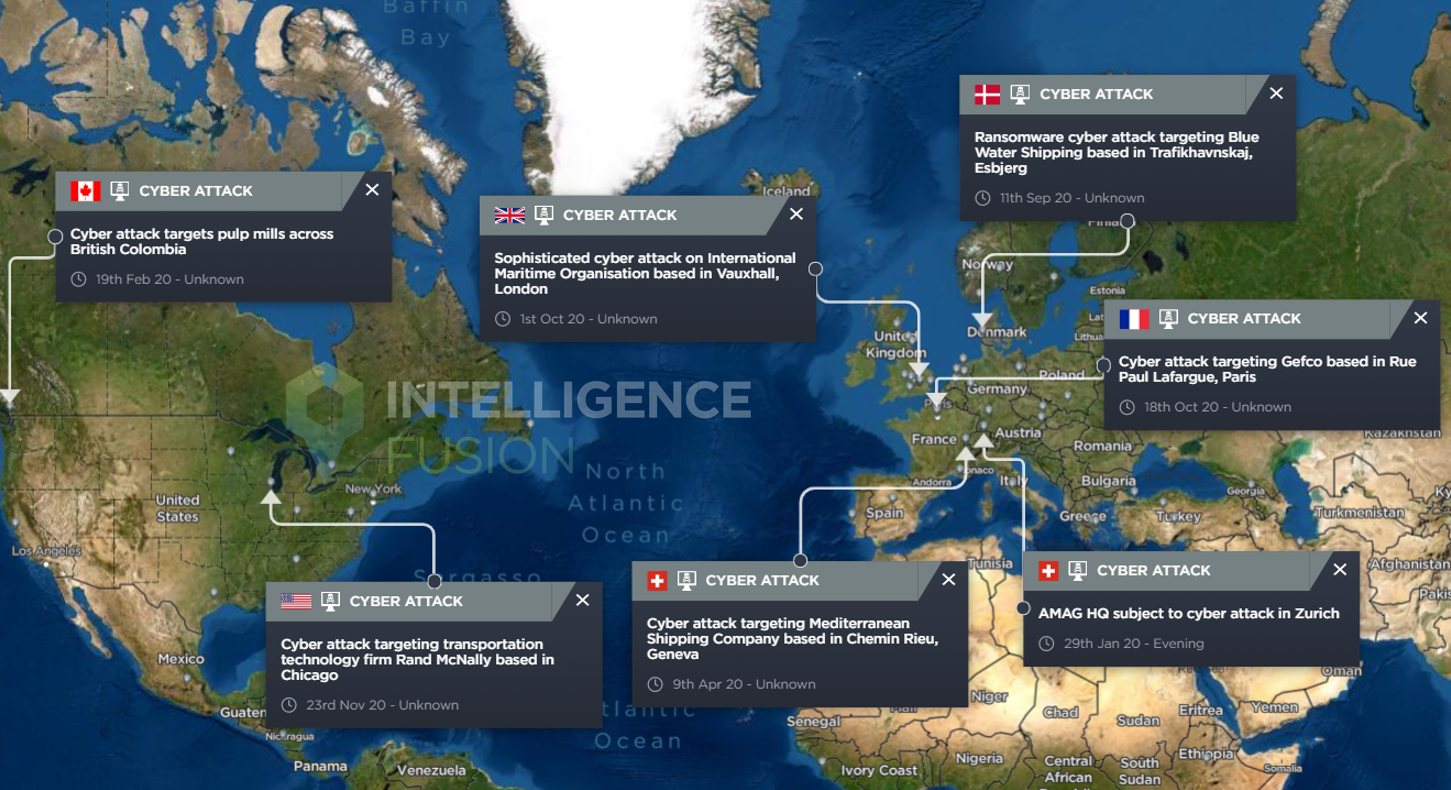
But it is not just criminal enterprises who are responsible for these attacks – geopolitical tensions are increasingly being felt in the world of cyber, and we have seen an exponential increase in nation state cyber attacks over the last 18 months, with businesses finding themselves caught up in the spillover of international tensions between different countries. With incidents like the Colonial Pipeline attack showing how a successful cyber attack can cost potentially millions in lost revenue, and cause severe disruption across all elements of the supply chain, this represents a significant threat to business operations. We sat down with Intelligence Fusion Chair, and cyber security expert, Robert Hayes, to discuss what kind of attacks we’ve seen, why the extraction industry might be particularly vulnerable to cyber attacks, and what actions could be taken to improve the security of their operations.

Robert Hayes has an extensive background in cyber and security
What is your background in cyber?
As senior police officer I ran several sensitive operations where technology was used as a tool to gather intelligence and evidence. This led to me being asked to set up and run the UK’s Hi-Tech Crime Training Centre where we trained officers from the police and customs services to investigate cyber crime and cyber attacks.
I then moved into British Intelligence where I led the UK National Technical Assistance Centre which provided specialist technical services to the UK law enforcement and intelligence community.
Following this I joined Microsoft as a Senior Fellow in the Microsoft Institute for Advanced Technology in Governments, which helped organisations find the sweet spot between security, policy intent, and innovation. I then moved to be Microsoft’s Executive Cybersecurity Advisor for EMEA, working to help enterprises in all sectors develop an effective end to end cyber security approach.
I now advise several organisations operating in the cyber and threat intelligence space.
The combination of nation state sponsored and organised crime activity has made the last twelve months by far the worst for cyber attacks – I do not see this improving in the short to medium term.
What have we seen over the last year or so that has impacted the world of cyber?
Cyber is really an extension of the material world, so issues in the physical world have an impact in the cyber domain. A good example of this is geopolitics; arguably relations between the West and China, Russia, Iran and North Korea are currently worse than they have been for decades, and so it is no surprise that this has led to an increase in cyber attacks on western infrastructure and organisations attributed to these actors.
Organised crime groups, some strongly associated with nation state governments, have also realised that extortion attacks against organisations using ransomware is much more lucrative and lower risk than traditional criminal activity, and the cost of entry is very low.
This combination of nation state sponsored and organised crime activity has made the last twelve months by far the worst for cyber attacks – I do not see this improving in the short to medium term.
Who is carrying out these cyber attacks? What is their motivation?
Motivation varies. Most organised crime groups are seeking money, but in some cases organised crime activity seems to be supporting nation state objectives.
Nation state cyber attack activity can range from classic espionage operations seeking information, such as the attack against the US Government Office of Personnel Management in 2015 which stole the details of millions of security cleared individuals and which has been widely attributed to the Chinese Government; operations to disrupt infrastructure, such as attacks on the Estonian power grid which has been widely attributed to Russian state actors; or simply to make a point or damage reputation, such as North Korea’s attack on Sony Pictures following the release of a film satirising the North Korean leader Kim Jong-Un. Interestingly, it also seems clear that North Korea are also using ransomware attacks as a revenue generator for their government.
How do these cyber attacks work?
A significant proportion of cyber attacks still require a degree of user action to succeed, whether this be clicking a link, opening an attachment, or social engineering to cause an employee to share a password. These initial activities offer the attacker a point of entry into the organisation that they can exploit to gain privileged access to accounts with administrator access.
Defences exist against these types of cyber attack – using multi-factor authentication across organisations and particularly for administrator accounts is an absolute must. Likewise educating employees on the types of reconnaissance and social engineering that attackers use.
What attacks have we seen recently? Are there any notable examples that stand out to you?
The last few months have particularly highlighted cyber attacks on the supply chain of organisations. Attacks such as Solar Winds or Kaseya targeted software applications that were used by many organisations – this worked by the attacker compromising the vendor and adding malicious code to the regular software updates that were sent out to customers. Once customer systems downloaded the update, the attacker gained access to those networks, and was able to exfiltrate data and inject malicious code into the host systems. These attacks successfully compromised many governments and enterprises which used the application.
How might the extraction sector be affected by cyber attacks? How can attackers disrupt their supply chains?
In my experience, many organisations in the extraction sector have not re-assessed the risk and potential impact of a cyber attack for some time and accordingly their defensive capabilities are underpowered when assessed against today’s threat actors. This is a potentially very costly oversight when you consider the damage that a successful cyber attack can cause to extractive operations.
The ransomware attack against the Colonial Pipeline Company in May 2021 shut down pipeline operations for five days and resulted in the payment of a $4.4 ransom to the organised crime group behind the attack. It is likely that the attacker first targeted the administrative computer system, probably through a malicious email attachment, and once a bridgehead had been established in the network, moved laterally until they found an account with credentials to access the operational systems such as the pipeline management; these credentials allowed the attacker into the operational systems of the company. The ransomware that the attackers deployed paralysed many of the core systems of the company leaving Colonial no choice but to suspend operations.
It is likely that the attackers had been quietly active in the Colonial network for weeks or even months before the ransomware was deployed. This is not unusual as attackers use this time to map networks, discover and exploit vulnerabilities, and leave further latent access points to facilitate future attacks.
Do we see any other real-world actions taken before or alongside these cyber attacks? Are there any indicators people can pick up on ahead of time?
Absolutely. As I mentioned earlier, cyber is often an extension of the physical world, and increasingly cyber is a precursor to physical activity, or part of a blended physical/cyber-attack.
Many governments offer excellent cyber threat advisories. These should be complemented and assessed alongside a physical/political threat assessment service.
What actions can companies take to mitigate the risk or impact of any potential cyber attack?
I would highlight three key activities for every organisation:
1) Embedding of appropriate cyber resilience controls and processes – for example audited compliance with a standard such as ISO 27001.
2) Demonstrating the effectiveness of those cyber resilience controls and processes through appropriate third-party technical testing of those controls against realistic threat scenarios and attack paths.
3) Demonstrating the maturity of their cyber incident response processes and associated executive engagement through appropriate cyber exercises with independent feedback.
How can an effective threat intelligence program help with this?
In my experience, most organisations significantly underestimate the scale and impact of the threat posed against their people and infrastructure. Underestimating the threat results in weak defences against attack – and attackers are adept at seeking out weak targets.
An effective threat intelligence program, ideally one custom made for the individual organisation, is essential if organisations are to make the right risk assessment decisions, and develop appropriate defences.
As Robert points out, then, failure to properly assess the risk to your business – and then take the appropriate steps to address these risks – can be catastrophic. For extractive companies in particular, being unable to run as normal can cost millions for every day of inactivity, as seen by the Colonial Pipeline cyber attack.
This is just as true in terms of physical security as it is for cyber, though, as we see on a regular basis on our threat intelligence platform. The Intelligence Fusion platform has a database of more than 600,000 recorded historical incidents, with more than 12,000 new incidents logged every month – helping clients understand the threats to their operations across a wide range of industries, including the extractive sector. Take a look at our guide on the 5 Biggest Threats to the Oil and Gas Industry in 2022 and learn more about how threat intelligence can help you identify the risks facing your oil and gas operation.