Gathering threat intelligence and how to use it
How intelligence collection works, from gathering threat intelligence as raw data and processing it into actionable intelligence, to using it as part of your business security or asset protection plan.
As an industry-leading threat intelligence provider, with our threat intelligence platform and data feeds relied upon by clients across the globe, putting order into our intelligence collection process – and how we’re gathering threat intelligence – is essential.
This starts by knowing the difference between raw information and valuable threat intelligence. In the most basic terms, intelligence is the process of gathering raw data and transforming it into useful information: data cannot be labelled as intelligence unless it has been given a layer of context or undergone analysis in order to define it to the requirements of the end user.
Intelligence Fusion provides an industry leading solution to situational awareness that aims to help security professionals and global businesses manage risk and security issues by collecting, analysing and disseminating intelligence on a mass scale. We deliver real time threat intelligence, at speed, to clients through a direct platform subscription or an intelligence data feed that is integrated into your own software or platform via our simple API. Consequently, we utilise many different types of intelligence collection when it comes to populating our threat intelligence platform or API data feed – but all of it goes through the same military standard intelligence process to ensure the consistency and reliability of the intelligence we provide our clients. This means that whether they require security, tactical or operational threat intelligence, our clients can have confidence in the data we provide, as every incident plotted and piece of intelligence gathered is as accurate and actionable as possible.
Our process of gathering threat intelligence enables us to map risk against legacy data points by deploying the military principles learned by on-the-ground experience of situational threat awareness, coupled with insightful and experienced human analysis from our 24/7 intelligence analyst team, that provides global intelligence at a greater speed, breadth, depth and accuracy.
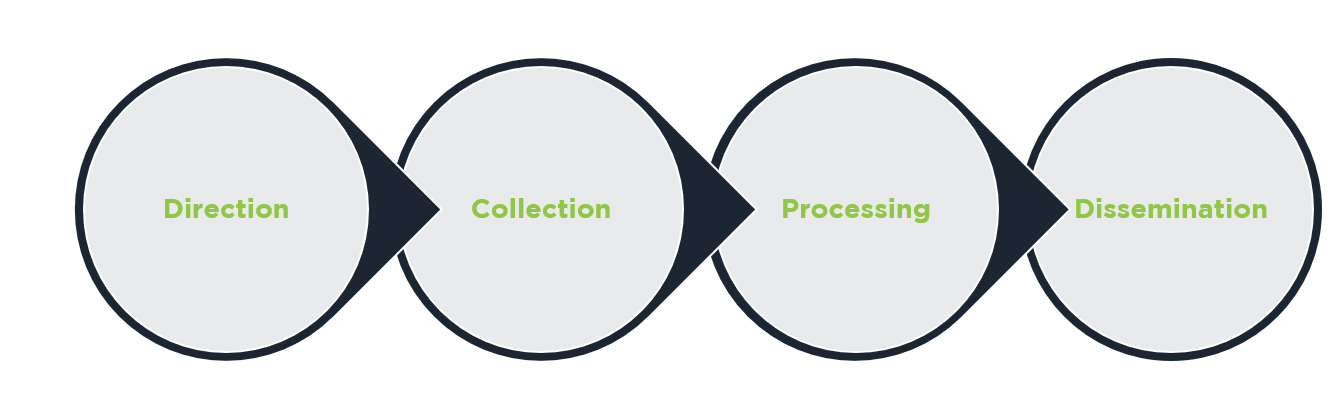
The intelligence cycle that guides our threat intelligence gathering at Intelligence Fusion
This process is based on a threat intelligence cycle that converts information into actionable intelligence:
1. Direction
Your business requirements are identified allowing us to cut through the noise and filter alerts so that you only see those which you need to be aware of. We monitor and report on all incidents across land, sea and air; anything across the world which may have an impact on your people or business activities.
Tailoring our support to a clients needs is core to the Intelligence Fusion proposition. We work on the foundation that delivering time sensitive material that is useful, practical and accurate can only be achieved by first understanding the unique requirements of your business – giving a clear focus and list of priorities for our intelligence collection team, and giving you a tailored threat intelligence solution that is geared towards your exact requirements.
2. Collection
Intelligence collection comes in many different forms, from a vast range of different sources. At Intelligence Fusion we currently monitor over 12,500 different sources as part of our 24/7 intelligence collection – which means that having a systematic and intelligent approach to gathering threat intelligence is vital in order to cut through the noise and find the most relevant information. The methods we use can vary – whether it’s our automated data-mining technology or our team of intelligence analysts trawling open-source channels, or even embracing the potential of crowdsourcing intelligence – but the principles instilled in how we gather our intelligence stay the same. Acting on the critical, whilst filtering out the irrelevant is fundamental to our bespoke analysis approach.
Intelligence Fusion has the resource and expertise to accurately report on incidents of every kind on a global scale. From post-incident analysis of high profile terror attacks like the Manchester Arena bombing to monitoring the increase in criminality in countries such as Sweden and a comprehensive library of resources and reports designed to bring an intelligent lens to all live data.
3. Processing
Our experienced intelligence analysts will then sift through the data, identifying the relevant information to be processed into intelligence through collation, evaluation, analysis, integration and finally interpretation.
We evaluate the credibility of the information and the reliability of the source for each incident we map, allowing us to understand how much confidence can be placed in each piece of information, and filter out fake news and disinformation – then by verifying the information reported, the significant facts and accurately geo-locating where it took place, as well as combining it with other similarly analysed information, we can turn this raw data into actionable intelligence, with valuable insights and interpretations ready for security teams to respond to quickly.
The human element of our threat intelligence services is crucial to the integrity of our data feed. Without the insightful and in-depth context that our analysts provide when gathering threat intelligence, our data is neither intelligent nor useful.
We currently process between 12,000-15,000 incidents every month, amongst which you can expect to find reporting on incidents such as;
- Conflict
- Terrorism
- Hazards
- Diseases
- Piracy
- Demonstrations
- Maritime issues
- Threats to aviation
- Criminality
- Non-traditional threats and many more
4. Dissemination
Our intelligence is then disseminated quickly and appropriately to our users via our cross-platform software and intelligence data feed. The right information at the wrong time is as potentially damaging as the wrong information at the right time; our aim is to provide the end user with relevant, accurate and actionable data to ensure they can make fast and informed decisions in response to threats.
Once distributed, the intelligence remains on our platform or in your data feed to access at any time. Intelligence Fusion currently has over 650,000 historical incidents and past trend reports from across the globe. Clients can use the data set for reference and analysis, to help users to make informed decisions regarding the environments in which they operate as well as anticipate and prepare for likely scenarios.
The Intelligence Fusion software is designed by analysts with years of real world experience of intelligence operations, creating a truly ground-breaking solution for security and risk management professionals around the world.
This threat intelligence gathering process was designed and built based on Intelligence Fusion’s 3 key elements; human analysts using their experience and knowledge to explore the right sources, and quickly identify significant incidents as well as misinformation; guided automated data scraping; teamed with our burgeoning crowdsourcing capabilities which, fused together, means that our intelligence has breadth of coverage, depth of insight and is entirely accurate, with multiple layers of validation. The depth and breadth of our intelligence data feed is unlike any other threat intelligence solution on the market currently.
That’s why an Intelligence Fusion data feed is the default choice for organisations of all sizes globally. With threat patterns constantly evolving and security risks increasing, we believe that our consistent and unique approach to gathering threat intelligence is the only way to bring our clients the assurance that they expect and need.
Looking back at this process, what becomes clear, then, is that the key to gathering threat intelligence that you can rely on is to have an effective threat intelligence program in place. A systematic way of putting order into intelligence collection to ensure consistency and accuracy of data is only possible once you’ve established a well thought-out overall threat intelligence methodology that works for your business – but if this is something you’re still putting together, you might need a little more guidance on what you need to make sure your threat intelligence program works how you want it to.
For this reason, we put together a FREE guide on How to Build An Effective Threat Intelligence Program. Download your free guide now to get started.

