AI vs. Human Analysis: Threat Intelligence Reporting
For security teams monitoring threats across the globe, gathering timely and accurate intelligence with context can be challenging. However, as we increasingly face more extreme threats, whether natural events driven by climate change or escalating geopolitical tensions such as conflict, the need to achieve this becomes more vital. These threats can be hugely damaging and far-reaching for businesses, supply chains and people – having the right information at the right time allows risk to be mitigated and resilience to be achieved.
There has long been a struggle between speed and accuracy in the world of threat intelligence. Receiving intelligence via AI and automated scrapers allows security teams to react quickly, but there is a risk that the intelligence may not be accurate, whereas human-led intelligence delivers quality and accuracy, but there is the risk that teams will receive this information too late.
Technology has evolved to allow security teams to work more effectively, analysing huge volumes of data at speed, enabling faster processing and threat detection – but it still makes mistakes.
In this digital age, social media can be one of the best sources for gathering intelligence; there is also a multitude of fake news and misleading information – so, what is the answer?
Introducing Intelligence Fusion’s, Virtual Analyst Tool
Combine the best of both worlds – the efficiency of artificial intelligence and the accuracy of human analysis.
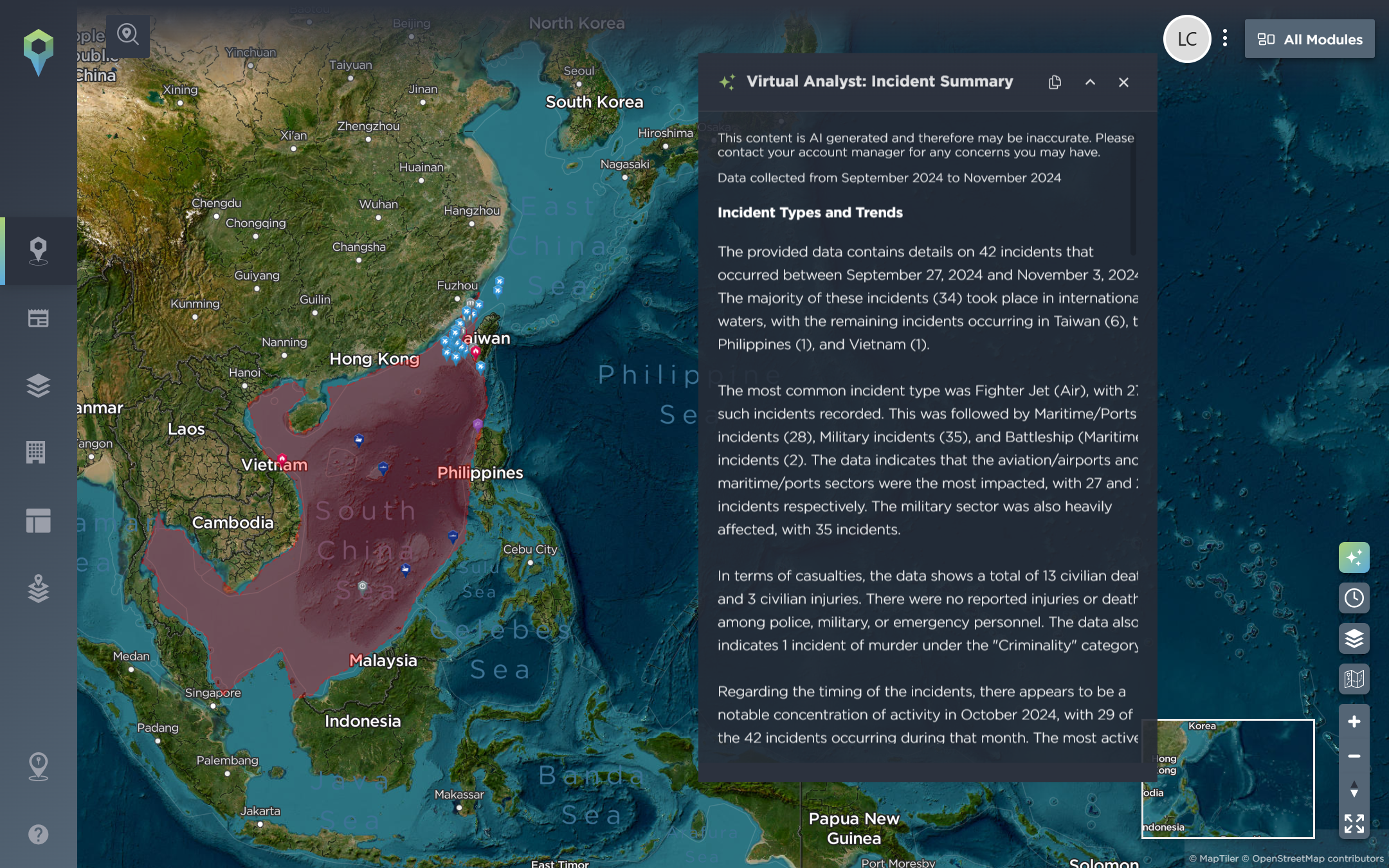
Incidents in South China Sea within a 7 day period being summarised by the Virtual Analyst Tool. [Image source: Intelligence Fusion]
HOW DOES THE VIRTUAL ANALYST TOOL WORK?
Rapid Contextual Understanding
Our team of expert analysts monitor the global threat landscape 24/7, reporting incidents across 159 different category types and capturing multiple data points, including accurate geo-location, impact rating, causalities and more. These incidents are 100% human-verified before being added to the platform, and analysts will add insights and commentary to help users better interpret context and relevance, connecting threats to specific organisational impacts.
We map over 20,000 new incidents each month and have a database of over 1.3 million historical incidents that can be useful for planning and reporting.
Our analysts are all based in-house and have diverse skill sets with varied intelligence backgrounds. Within the team, multiple languages are spoken, with analysts joining us from all over the world.
The data collection is based on military intelligence principles. We use the Intelligence Cycle to help us focus our collection efforts to best meet the needs of you and your organisation. In addition, we use Intelligence Collection Plans, which is a process often used by armed forces and intelligence services to ensure that the intelligence requirements of a mission or client are met.
An ICP helps to close gaps in knowledge and provides clear direction for the collection process. They also give intelligence teams a standard structure to work from to help analysts remain focused on the task at hand.
Combining this with the Virtual Analyst Tool allows users to process vast amounts of data in seconds, identifying patterns, trends and anomalies.
At the click of a button, the incident summary tool will provide an overview of hundreds of human-verified incidents, helping to enhance users’ understanding and allowing you to delve further into trends and themes without having to manually review all individual incidents. This allows analysts and users to concentrate on more complex analysis, using AI to enhance understanding and bolster an organisation’s response readiness.
For example, you may want to review incidents in the South China Sea in the last 7 days – you can use the Draw Area Tool to select a specific location and then use the Advanced Filters to get as granular as you like – the utilising the Virtual Analyst Tool will give to a report summarising the incidents – you can save this filter meaning you can return and generate more reports, for example on a weekly basis – giving you strategic intelligence at the click of a button.
In addition, our AI-assisted news feed crawls more than 1 million news articles every month – that’s 23 articles per minute. Providing you with fast raw news updates that can be filtered to provide further speed and insight.
Versatile Application
The Virtual Analyst Tool can be accessed from various locations on the Intelligence Fusion platform. Custom filters can be set up to get granular results based on what matters most to you and your organisation. You can also summarise incidents near your physical assets to get an understanding of the biggest threats in the areas you are operating in. In addition, you can summarise country profiles to see the biggest risks, incident types, geographic distribution and trends impacting specific countries.
Efficient Reporting
The Virtual Analyst Tool can enhance your productivity by speeding up the writing of comprehensive summaries or reports for clients/senior management. Simply copy and paste the analysis, fine-tune filters and regenerate an analysis or use the incident summary tool as the basis for a report. If you want more in-depth analysis, you can reach out to speak to a member of the analyst team in order to access a comprehensive human-generated report.
Unified Intelligence
Using the Virtual Analyst Tool integrates tactical, operational, and strategic intelligence, allowing users to make confident decisions based on a complete picture and anticipate future threats to safeguard your organisation.
BEST PRACTICES FOR COMBINING AI AND HUMAN INTELLIGENCE IN THREAT REPORTING
Implement a hybrid approach
Understand the benefits of AI and leverage it to your advantage. Plug gaps and speed up manual processes, but be wary of the downsides – this should enhance your threat intelligence collection and analysis but should not replace humans.
Training and continuous improvement
Technological advancements mean AI is constantly evolving; do not stand still; work with an organisation that will keep striving to improve processes, features and user experience.
Specific training for security teams can be useful to enhance skills that AI does not replace and gain the best output.
A continuous feedback loop will allow features to keep evolving and improving – work with an organisation that truly has a customer-first mentality, ensuring features are shaped by end users to create the best possible product.
Building Trust with Transparent Processes
Understand how AI works and how insights are generated; AI is constantly learning and improving. Work with an organisation that clearly states what processes are AI-driven and which are human-driven – this allows you to make decisions with confidence.
At Intelligence Fusion, the Virtual Analyst Tool is in BETA test mode, so be the first to try it and shape the future of the platform. We strive to keep improving and delivering the best product for you and your teams.
