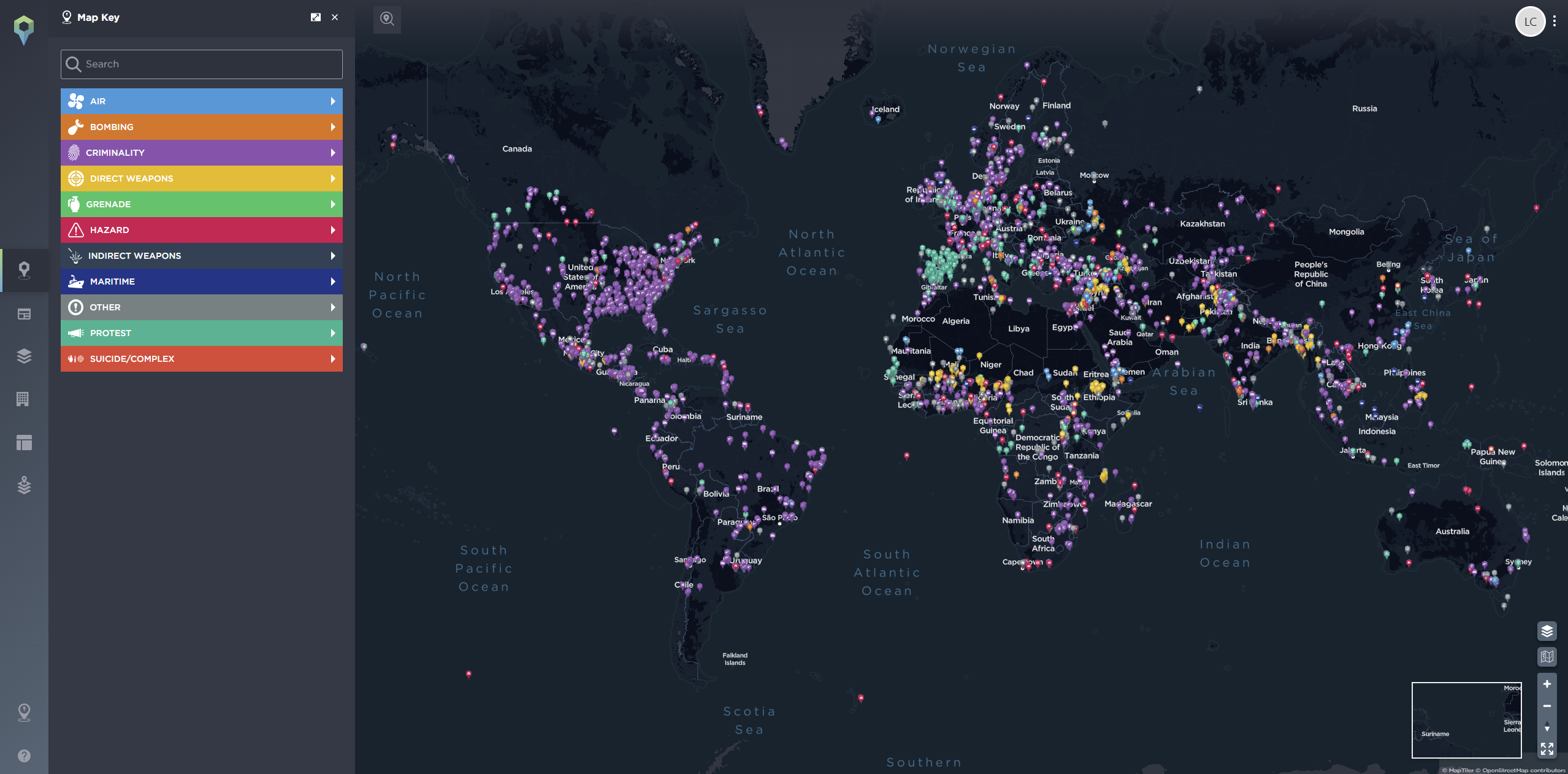
How to conduct an effective route threat assessment
A guide to conducting an effective route threat assessment for asset protection, corporate travel security and risk management, and the tools your security team will need.
When you understand how to conduct an effective route threat assessment, it becomes a valuable asset that can help you and your security team understand, and therefore plan for, the potential threats your travellers may face.
Ahead of any corporate travel, mission or deployment, there’s a process of risk management that must be carried out. It’s usually the responsibility of the security team leader to highlight the mission and the proposed routes to the intelligence analyst, or person conducting the assessment. Your intelligence analyst will then review historical incidents, as well as gather more data on the areas featured in the mission brief if required.
An effective Route Threat Assessment will usually consist of the following:
- A map of the area
- The routes involved
- Any boundaries
- Social context including demographics, tribes, military, police etc.
- The circumstances for example intent, weather or anything else of note
Based on the intelligence gathered, your analyst will then produce a threat assessment which will feature the assessed intent and capability of threat groups/individuals against the client/team. Often this will be broken down on a route or location basis, for example, Baghdad Airport Road, Baghdad International Airport.
There’ll also be a section which states the threat rating. Often the intent will be circumstantial, being in the wrong place at the wrong time as an example, rather than a known or direct threat. Depending on the profile or mission of your team or client, this would vary.
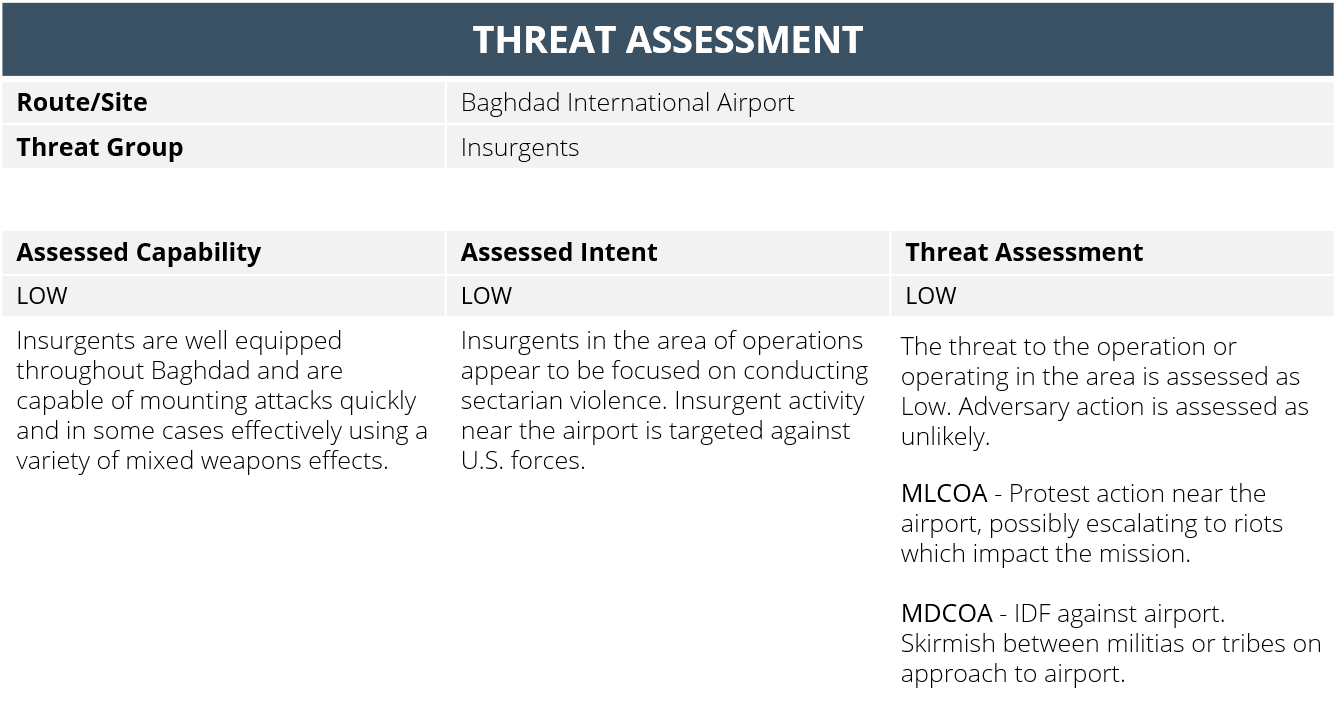
The key to any threat assessment, or mission planning in general, is intelligence data. Verified, accurate intelligence will help to guide the mission and aid in avoiding areas of elevated threat, as well as understanding the potential threat actors. In addition to the pre-mission planning, easy access to the intelligence data throughout is crucial for asset protection and the safety and security of your travellers.
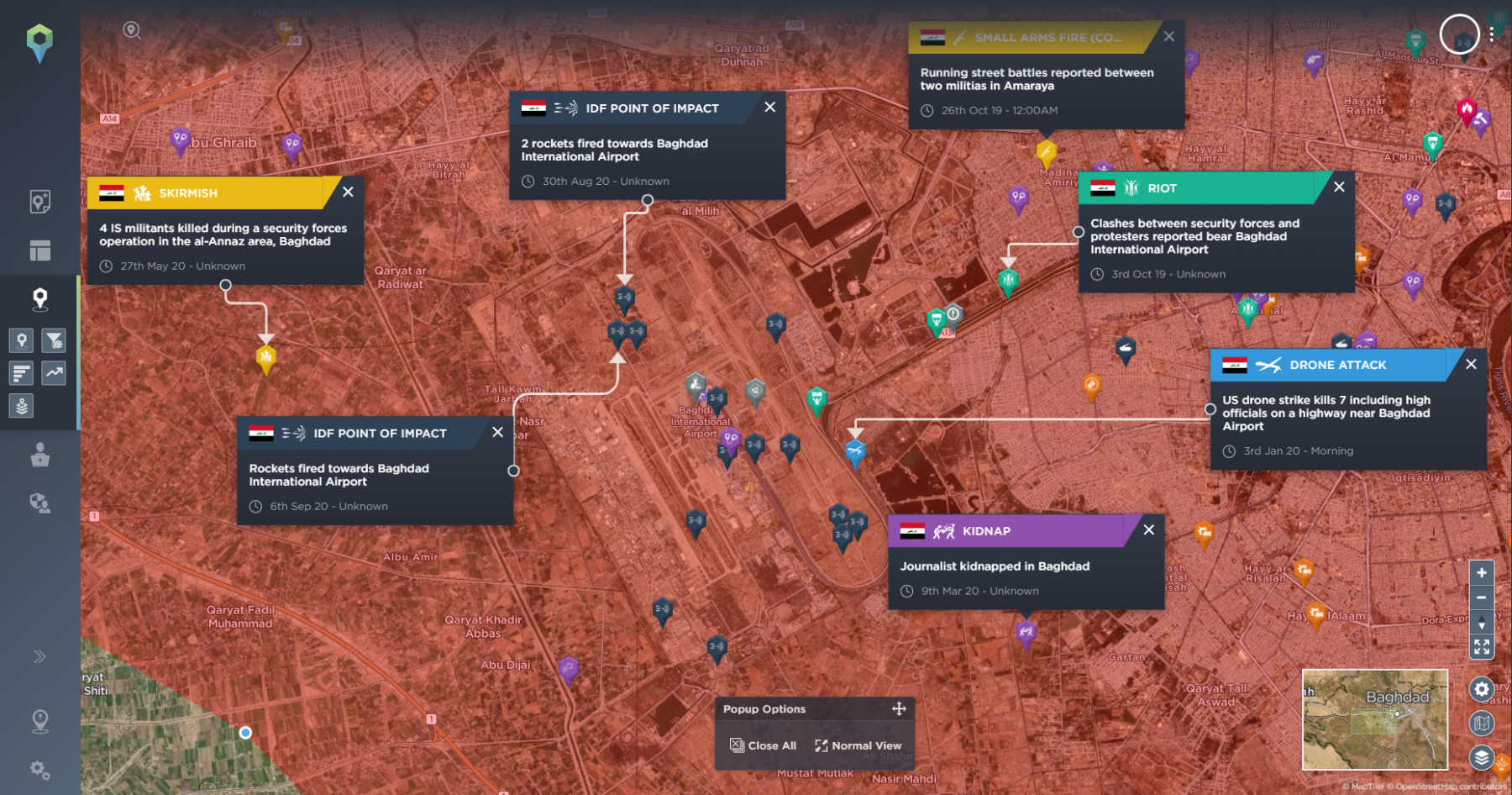
In previous roles, I would create a Route Threat Assessment in a Microsoft Word document which the team leader would then use to plan their mission, adjusting routes and timings based on the intelligence I provided.
On the day of the mission, the latest intelligence would be presented in a PowerPoint. This would be a multi-slide presentation broken down by the legs of the route, with my threat assessment at the end, including my assessed Most Likely and Most Dangerous Courses of Action, based on historical patterns and trends. Once out on the ground, the only way for me to get information to the team regarding new developments was via the Watchkeeper’s radio.
Later, when working on a consultancy basis, if I was contracted to complete a threat assessment for a client, I would have to spend days gathering enough historical data to make sure the assessment was as comprehensive as possible – a time consuming task meaning missions couldn’t be planned and conducted at speed. The cost would also reflect the time it took to gather the relevant data which could often be several days.
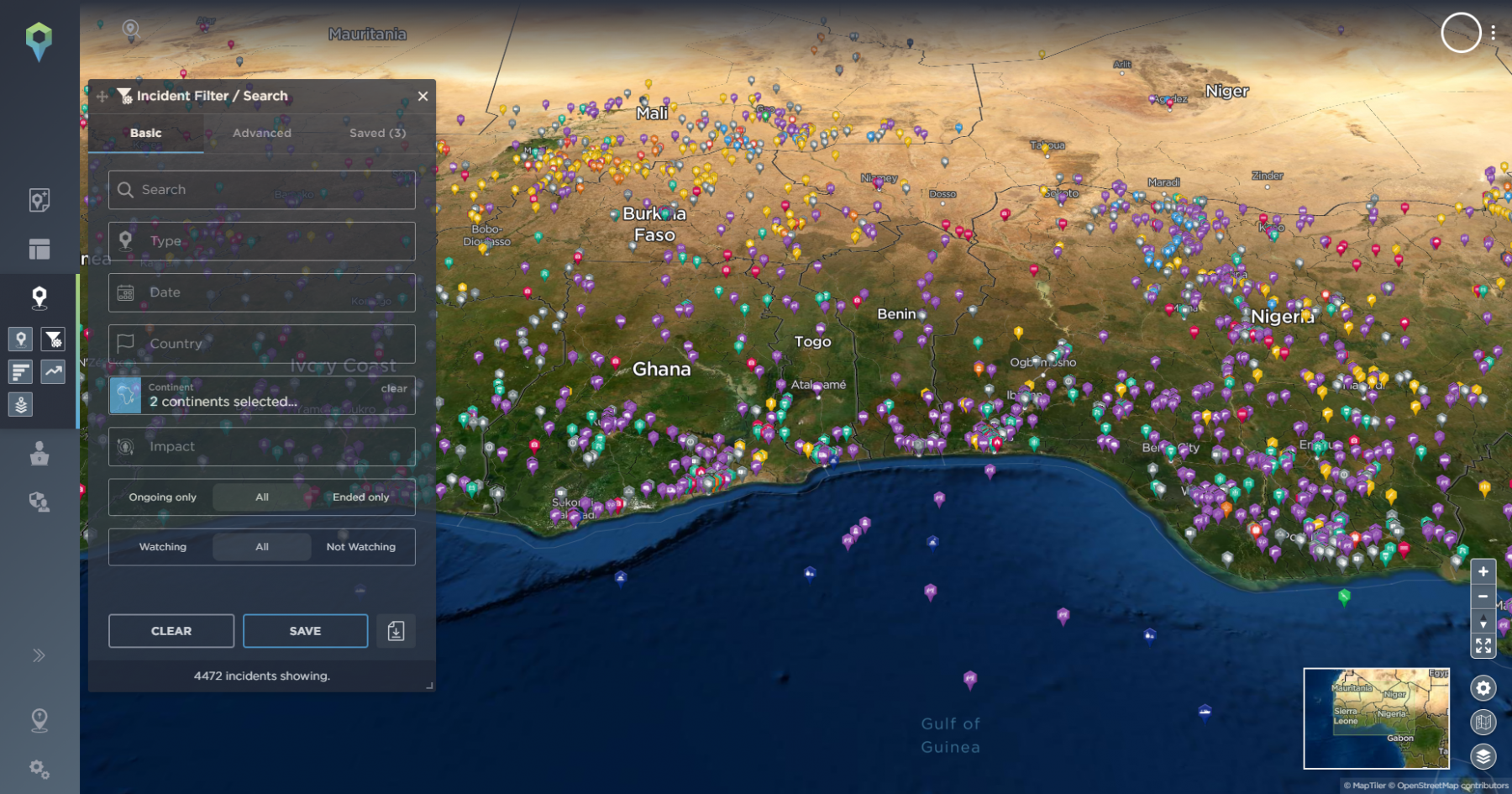
Fast forward 10 years and we have a completely different problem.
Security leaders now have access to a wide range of intelligence tools and software that can significantly speed up this process, saving them not only time but money too. However, in order to conduct an effective route threat assessment you need to ensure the solution you invest in meets your security team’s needs and can be tailored to the way you operate.
When choosing a solution for your asset protection or corporate travel security, you’ll need to consider:
1. Depth of Data
For a complete and comprehensive understanding of the route, you’ll need insight into the history of the area, including incident patterns, active groups and their targets/tactics.
Being able to really deep-dive into an area isn’t as common as you may think, with many intelligence providers archiving their data after 12 months or sometimes even less, making it difficult to build a comprehensive risk management profile of a location. Intelligence Fusion, on the other hand, have a historical dataset of over 1,200,000 incidents dating back to 2015 – all of which is freely available on our intelligence platform or via an API. If a client wants to understand the ground truth of almost anywhere in the world, they can access that data immediately.
Every incident has tactical value too. Our analysts are trained to adhere to military intelligence principles and ensuring our data is accurately geolocated is standard practice, meaning that every incident is mapped as closely as possible to the location that it occurred. This is vital when putting together an effective route threat assessment for asset protection on the move.
2. Breadth of Data
Intelligence goes beyond social media. In fact, reliable intelligence requires both multiplicity and balance so a provider with a wide ranging database of sources can offer more insight into an area than those who rely on a single source.
As a security professional, you’ll know that some sources are more reliable than others depending on the region or the kind of information you’re looking for. For us at Intelligence Fusion, our collection methods span across more than 12,500 different sources and mediums including all forms of social media, local news media as well as western media, Telegram and a growing on-the-ground network, with each source rated for its credibility and reliability.
With our online sources, we identify incidents by fusing together datamining and manual collection. Our 24/7 analyst team work around-the-clock to report breaking incidents and are supported by our datamining algorithms designed to increase the speed and consistency of our feed.
On a monthly basis, we collect over 20,000 incidents across the globe, prioritising the needs of our users first and foremost. Our clients drive our efforts through direction because when the reporting is shaped to closely reflect your organisation’s operations, you get a more useful and precise insight into the global security landscape, as well as its impact on your people, assets and reputation.
This means that we can be responsive too. So when your mission brief changes, your route takes you into new and unknown areas or the threat landscape evolves, you always have the relevant intelligence data for your travel security and asset protection needs.
3. Actionable Data
Misinformation and disinformation plagues the internet; verifying every incident can be a time-consuming and resource-intensive task. A solution that eliminates the need to fact-check can ensure your team is responding to reliable information.
It can be difficult however, when speed and timeliness of alerts are key. Even more-so when your team or client is in transit. Many solutions solely rely on algorithms to feed incidents to users, which guarantees speed, but can it guarantee accuracy?
At Intelligence Fusion, we allow for a balance, ensuring timely, actionable data but without removing the human element that takes raw data and turns it into tactical intelligence. Even the information that’s identified by our datamining is fed into a moderation area in order to be verified and more importantly, correctly geolocated onto the map before it’s disseminated to you as the end-user. This saves you vital time while still being the accurate and reliable data that is key to effective asset protection or corporate travel security, allowing you to take action as soon as you’re alerted – and make any necessary changes to your planned route as quickly as possible.
4. Accessible Data
A solution that you can use at every stage of the route threat assessment provides the most value for money. So rather than having to create a PowerPoint presentation, your analyst should be able to brief directly from your intelligence platform. The same platform can then be utilised by the security team on the ground, who can be monitoring the route from a mobile or tablet device.
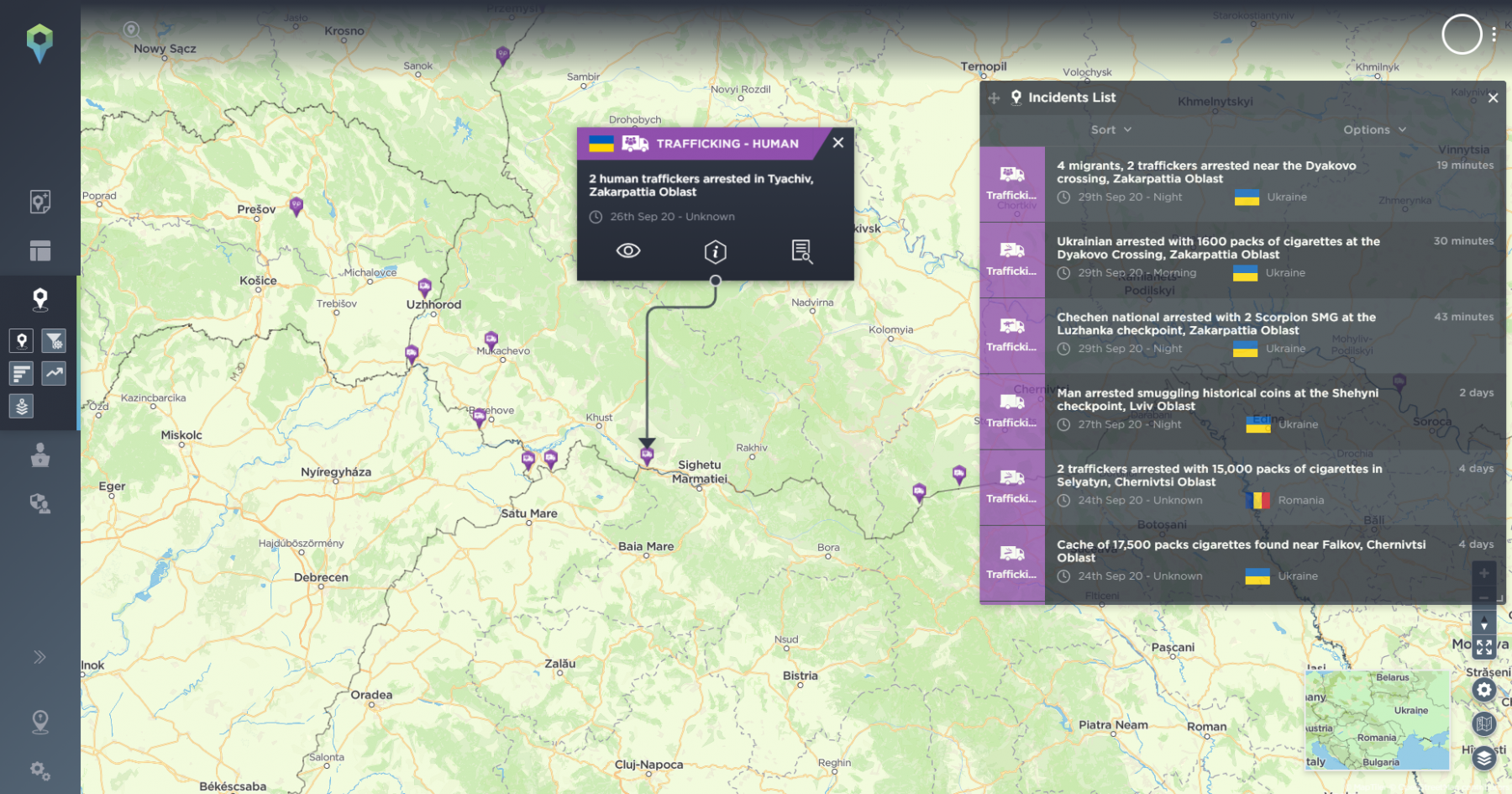
The Intelligence Fusion platform is interactive, with an intuitive UX. During a briefing, your analyst can click an incident and bring up full incident details, including images and footage. They can also dig into the historical data, when fielding questions from the security team or client.
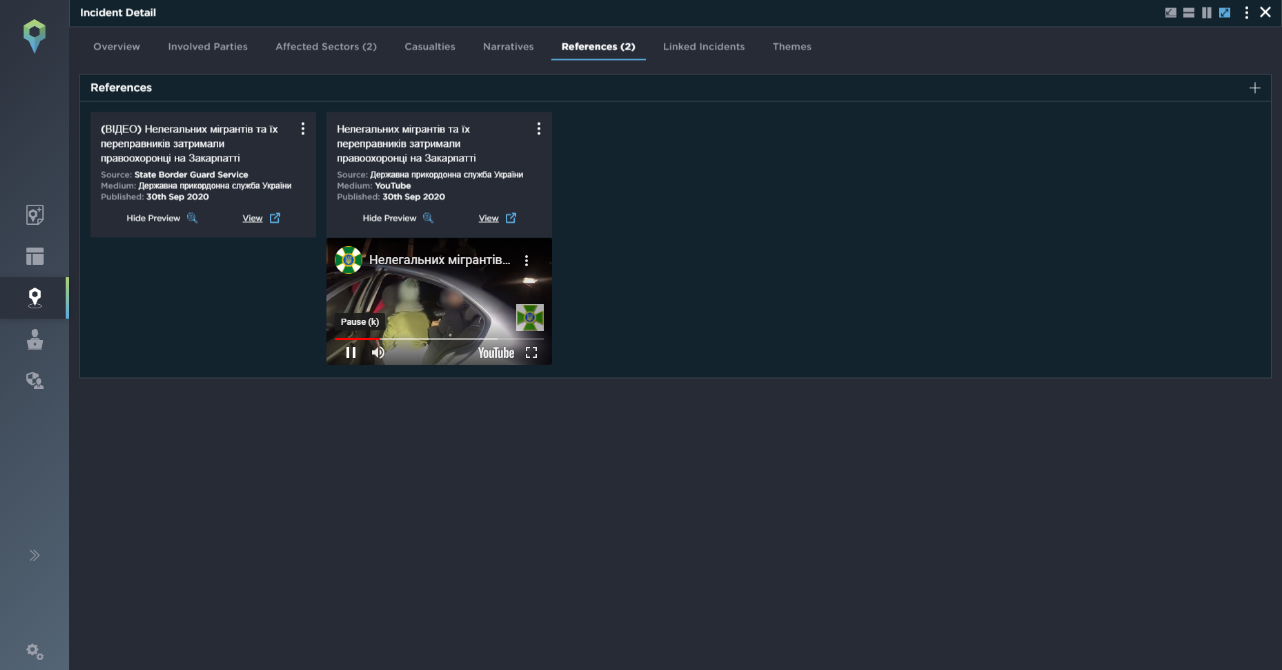
On the ground, a responsive platform means that the threat picture becomes dynamic and much more accessible. If a major incident happens, the security team has an entire intelligence cell in the palm of their hand, gathering details regarding the incident, as well as supporting the security team.
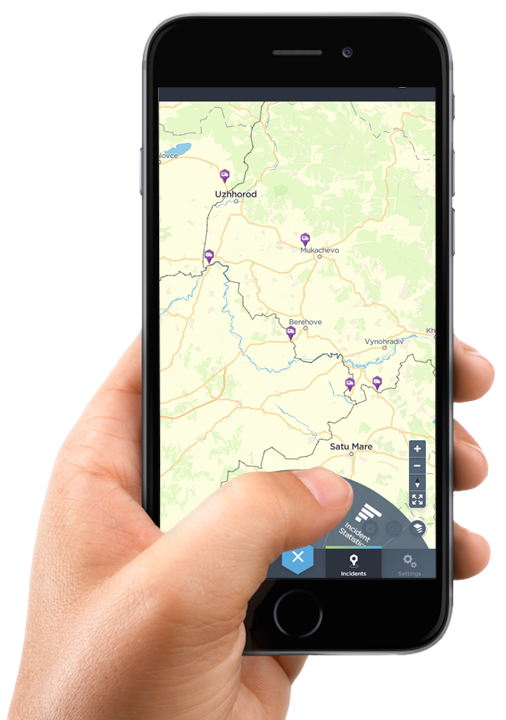
This doesn’t mean that your team needs to keep an eye on the map at all times. You can use our notifications tool to be alerted immediately if anything happens within your set parameters.
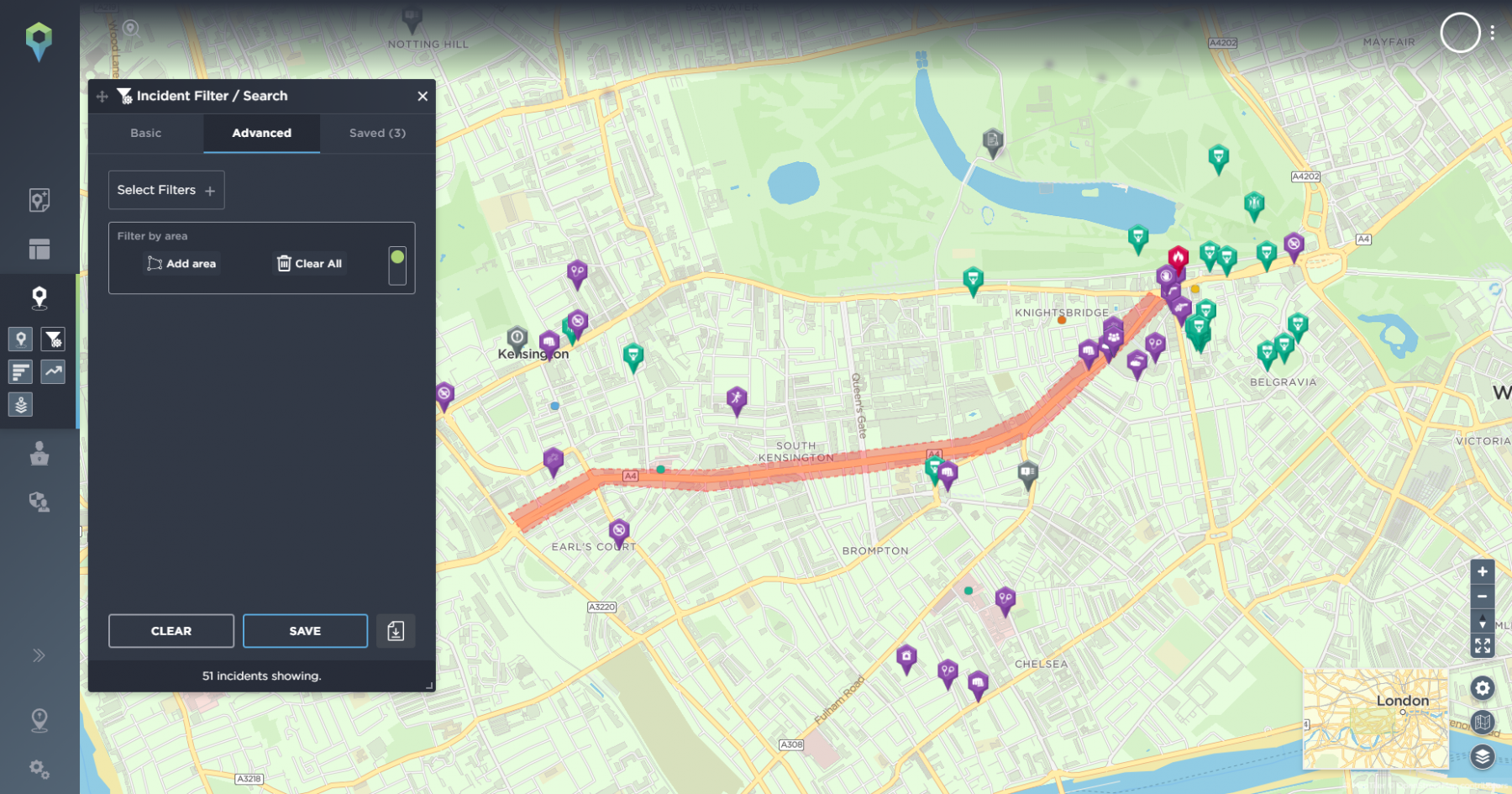
Our filtering options are extensive, so in addition to geofencing around your route, you can also specify the types of incidents you’d like to be notified of if they involve a certain group or party or even if they’re of a particular severity level.
Users can also use our static assets management feature to build up a complete operational profile of the mission area. For example, if a mission was operating in the area of Knightsbridge in London and the first task location was the Consulate General of Turkey, you can plot the exact location onto our map.
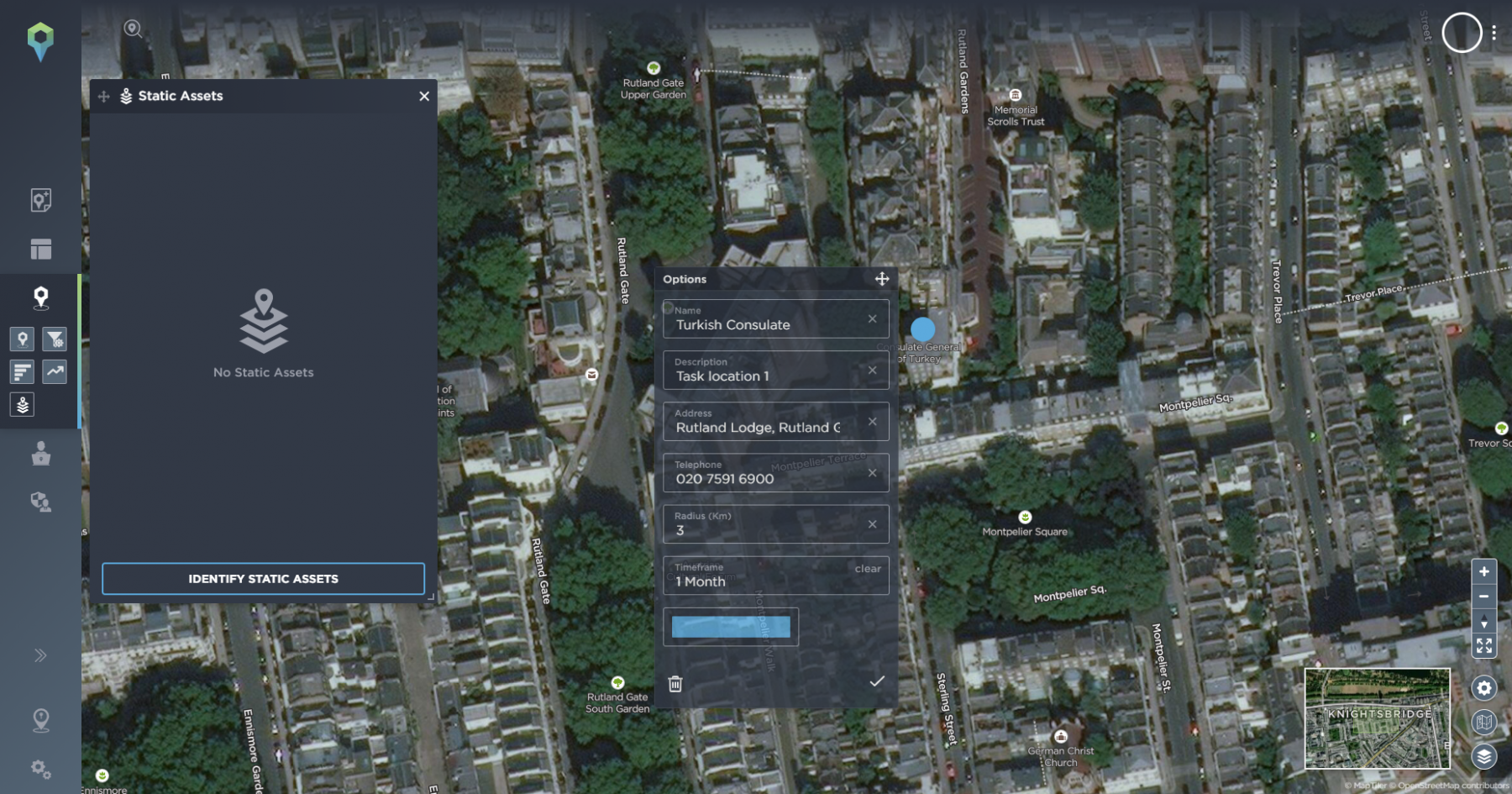
In Intelligence Fusion, you can either have your own individual static asset map or an organisation-level map. At organisational-level, if you have multiple users across the team, you’ll all be able to see the same assets. You can input all the mission locations, telephone numbers, addresses and any additional notes, which can then be accessed by your entire team, as well as the operations staff, making a unified asset protection strategy easy to establish.
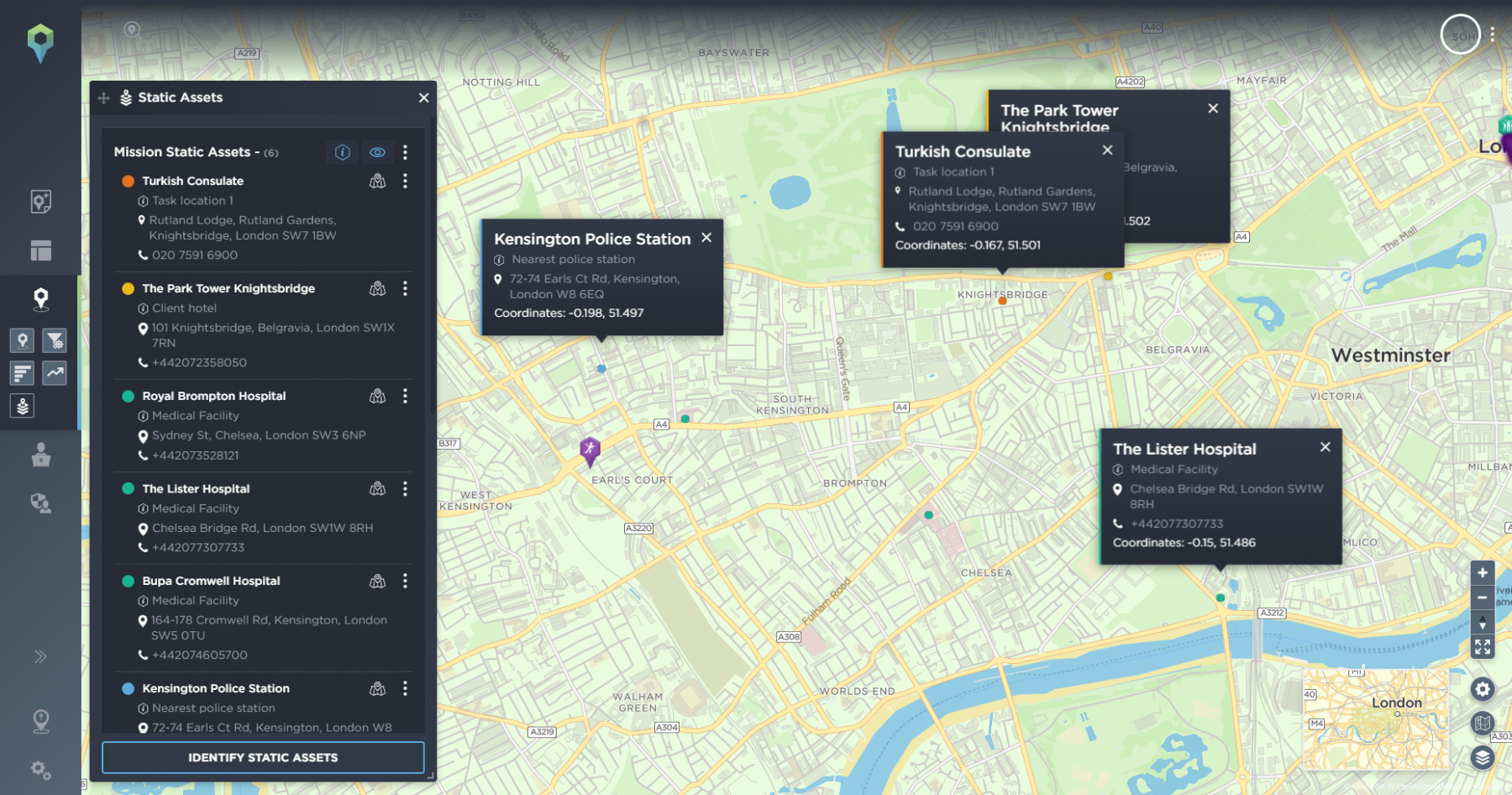
With the quantity of intelligence we disseminate it can become overwhelming, so users have the ability to set filters around static assets based on radius and timeframe. For example a timeframe of the last 30 days and a radius of 3km will significantly narrow down what the map displays around that asset, reducing the noise and giving the team a focused, mission specific map.
5. Long-term Investment
Many solutions, like Intelligence Fusion, are great because they’re highly customisable and can be easily aligned with your operations. This can often mean an investment in your time, ensuring that the system is set up correctly, but this isn’t a process you’ll likely want to replicate every 12 months as you move providers. Choosing a scalable software that evolves in line with new technology and changes in the industry means you have a long-term partner to grow into.
In order to ensure we’re always the ultimate solution for threat intelligence, we are constantly developing and have further exciting additions in our roadmap that will be released soon, including AI incident reporting and active alerts. However, focusing on some recent exciting developments that have been released shows how we can further allow you to hand-pick the most important tools and features for you and your team.
Country profiles: If you have operations across multiple countries, or offer corporate travel security or VIP asset protection for clients travelling to countries across the world, you need a constant understanding of the latest developments. We’ll provide you with extensive country data including information such as population size and demographics as well as a list of key incidents that may have impacted the security situation and the key groups operating in each region. This will all be encapsulated with an assessment from our intelligence analysts.
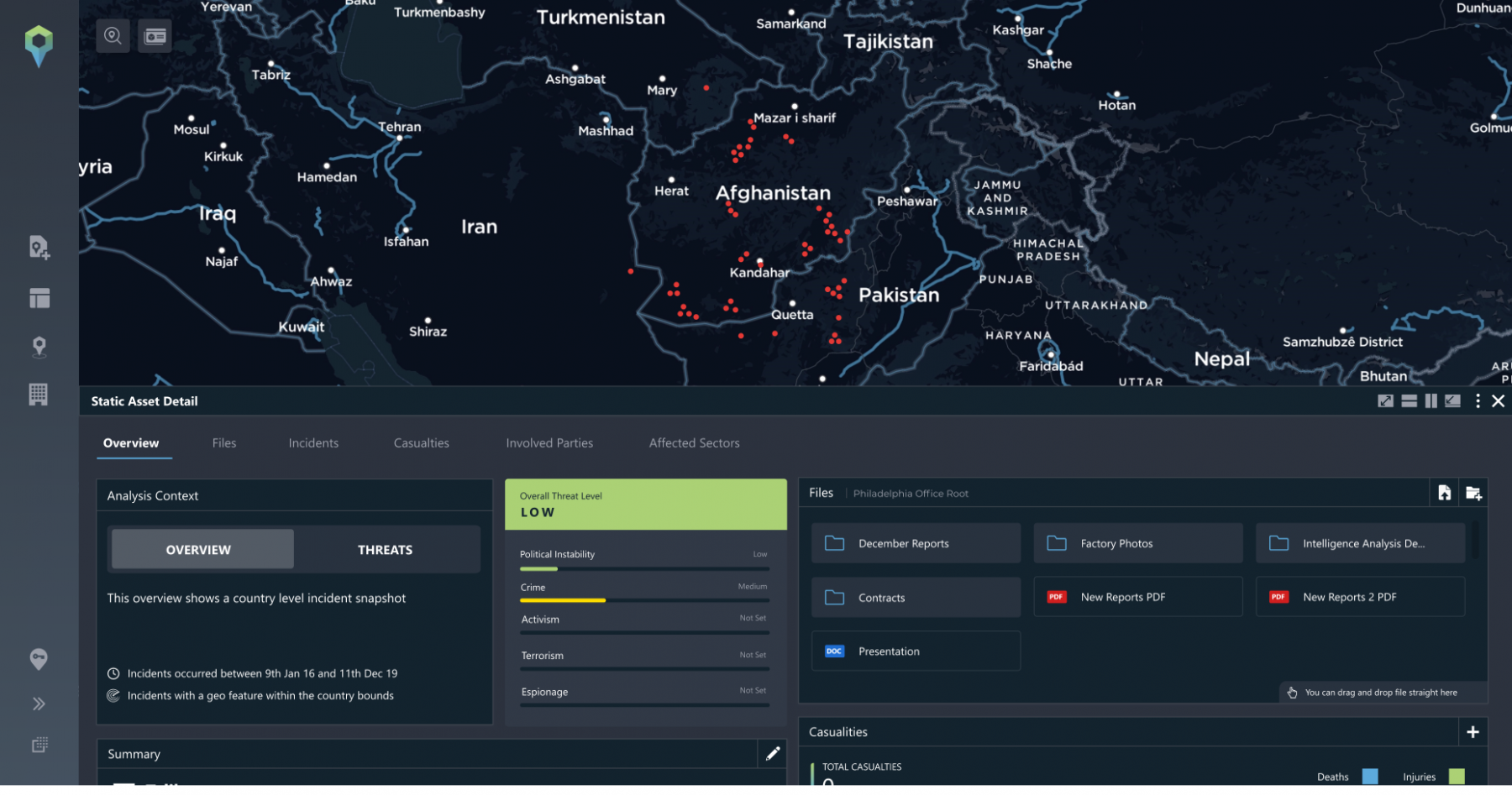
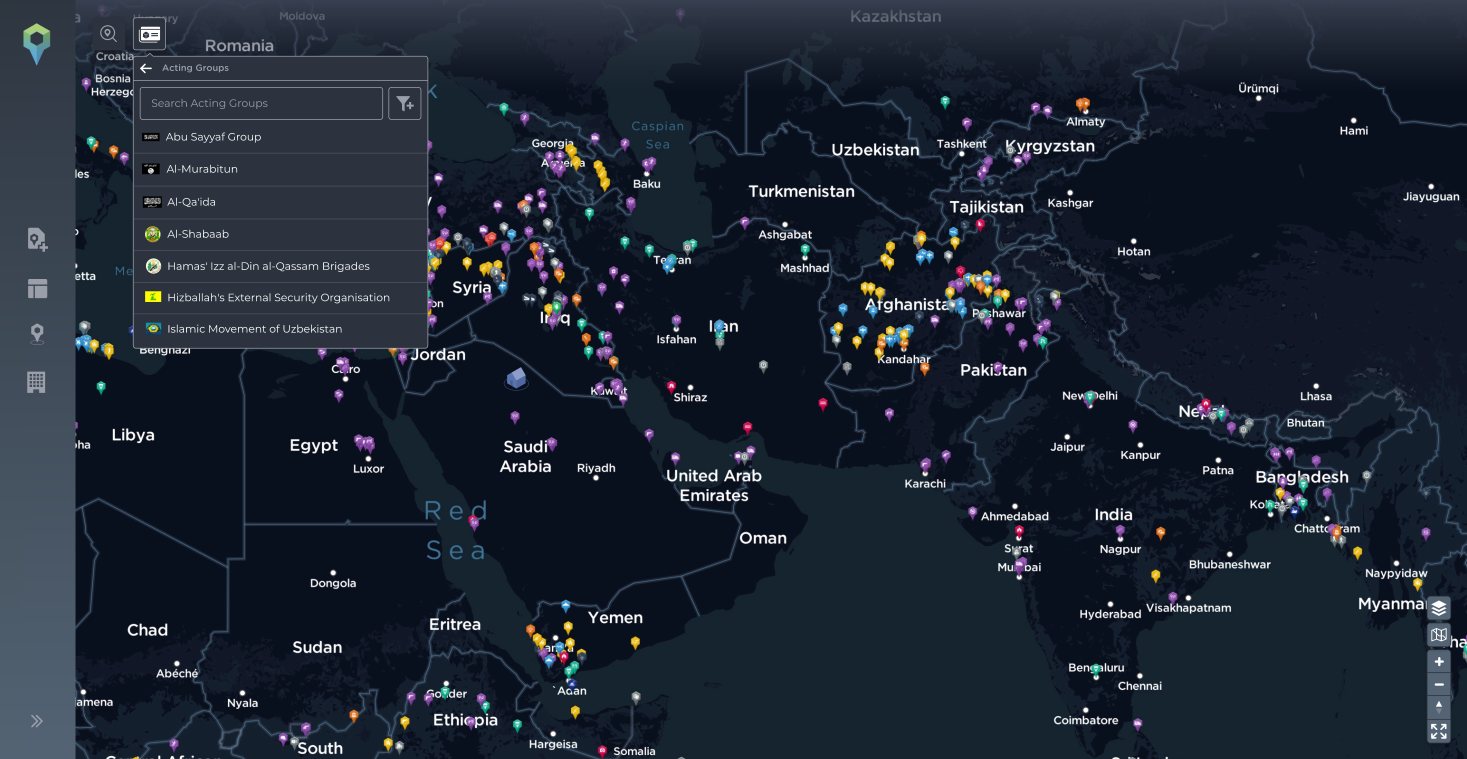
Alongside the country profiles, we also have actor profiles. We highlight groups, parties and individuals that are involved in every incident, whether that be because they were an actor, directly targeted or even indirectly affected by that incident. The involved parties feature includes criminal groups or terrorist organisations as well as activist groups or even military and security forces. Users can click on each of these involved parties for a complete profile.
You can access a full list of the incidents they have been linked to, a map showing their geolocated activity, key leaders, as well as our analyst’s assessment. In terms of the route threat assessment and mobile asset protection, this adds greater context when trying to understand the capability and intent of groups within your mission area.
We also offer the option to add a document storage feature, giving you the ability to upload, manage, share and store documents of all file types. For example, if you have a crisis management plan related to a specific mission, you can upload it and then disseminate it to all static and mobile assets linked to the mission. All documents will be securely protected behind two factor authentication, as opposed to having hard copies of maps and mission plans, streamlining your operations and simplifying processes.
We’re constantly harnessing new technology and evolving our collection methods to ensure you stay one step ahead. We’ll never remain stagnant or stop innovating, meaning we’re a long-term partner for growth and keeping up with the ever-changing threat landscape.
Summary
In summary, an effective route threat assessment requires a solution that can bring the operational picture to life, making it easier for you to understand what’s happening around your assets at all times as well as the impact of an incident and how you can respond quickly and effectively to it.
Technology is allowing us to make huge advances in how we can support you and your security team on the ground. Not only in terms of disseminating intelligence using the principles of timeliness, appropriateness and standardisation, but also cost effectively, through empowering the end user with all of the data.
Given the significant deterioration of the security landscape in the last decade, having a solution that you can shape to meet your business needs is important. But an innovative technology partner that can provide long-term protection as your business evolves and the world continues to change, is crucial.
If you’d like to find out more about how we can support you in better protecting your people, assets and reputation through bespoke intelligence solutions, speak to a member of the team today.